Chainlink 2.0 Super-Linear Staking: An Overview
The recently released Chainlink 2.0 Whitepaper introduces a variety of innovations aimed at significantly improving the capabilities of Decentralized Oracle Networks (DONs), most notably by enabling DONs to perform secure off-chain computations. With DONs providing smart contracts access to a wider array of decentralized services beyond data delivery, a more expansive hybrid infrastructure becomes available to developers, empowering them to combine on-chain code with off-chain resources to build increasingly advanced smart contracts.
One dimension to provisioning these next-generation hybrid smart contracts is creating a robust cryptoeconomic security model for DONs that maximizes the cost of attack. This is critical to scaling the security of DONs as they become increasingly involved in securing key functions within high-value smart contracts that affect user funds. To achieve a heightened level of tamper-resistance, the paper presents Explicit Staking—an advanced cryptoeconomic system in development where Chainlink nodes lock up LINK tokens as collateral that can be slashed for malicious and undesirable behavior.
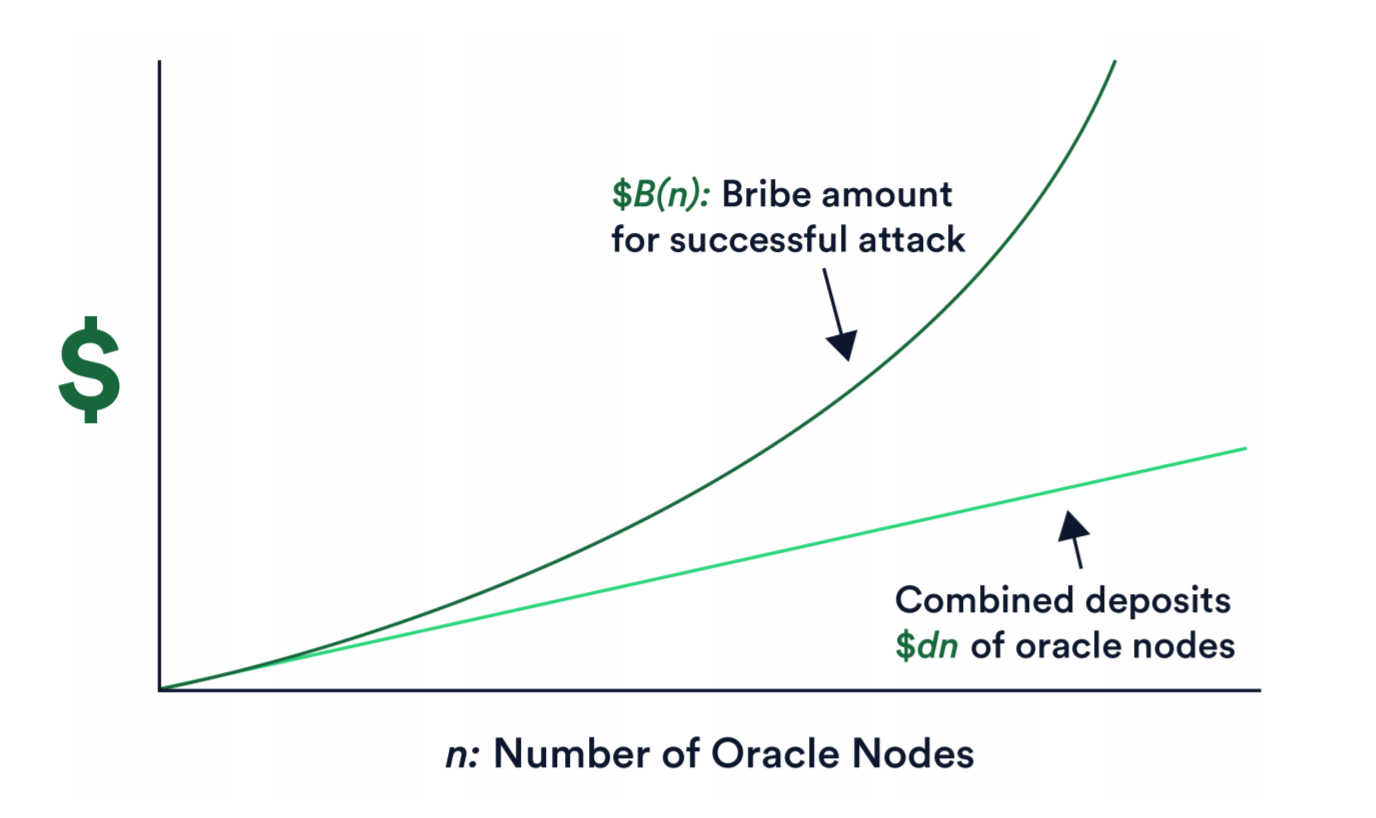
The Chainlink staking model is unique because it’s designed to protect against an extremely broad class of well-capitalized adversaries, as well as achieve a super-linear staking impact—a mechanism where malicious actors are required to have a budget significantly larger than the combined deposits of all nodes within a DON, creating increasingly greater security guarantees for high-value smart contract applications in a cost-efficient manner.
Within this article, we provide an overview of explicit staking in the Chainlink 2.0 Network and how it will generate a much greater level of cryptoeconomic security for users. For more information on Chainlink’s explicit staking model and all of its technical nuances, refer to section nine of the Chainlink 2.0 Whitepaper.
Role of Explicit Staking in Decentralized Oracle Networks
Chainlink’s explicit staking mechanism aims to achieve a fundamentally different goal than staking within blockchain networks. While Proof-of-Stake blockchains use a staking mechanism to generate global consensus on a set of transactions ordered into continuously created blocks, explicit staking in Chainlink 2.0 aims to achieve the creation of reliable and tamper-resistant oracle reports that accurately reflect the state of specific real-world events outside a blockchain (off-chain).
Ultimately, the goal of explicit staking in Chainlink 2.0 is to increase the cryptoeconomic security of DONs, giving users greater guarantees around the validity and timeliness of the external data and off-chain computations that their high-value hybrid smart contracts rely upon. Oracle staking mechanisms to date have only been designed to protect against a narrow set of attacks, without the capabilities of a realistic adversary. By comparison, Chainlink’s explicit staking mechanism protects against a broad range of attacks, including advanced strategies like prospective bribery, in which nodes are targeted according to their role in the network, such as those selected for report adjudication.
The Foundations Underlying Chainlink’s Explicit Staking
The Chainlink 2.0 Whitepaper describes how explicit staking will secure DONs that are tasked with delivering financial market data on-chain, a common external data resource required by many DeFi applications. The proposed explicit staking mechanism consists of multiple independent components that combine to generate a significant amount of cryptoeconomic security.
Service Agreements
Behind each DON is a service agreement that will define the number of LINK tokens each oracle node is required to stake and key performance requirements, such as how far an individual node’s response can deviate from the aggregated value and how far the aggregated value in an oracle report can deviate from the correct value it should represent. The service agreement can also define other parameters such as the data sources used, how often updates should occur, how much each node is paid, and more.
Outputs produced by a DON are structured into reporting rounds, where each round involves the creation of a new oracle report containing each node’s individual response for a particular piece of data (e.g. the price of ETH/USD), with all the individuals responses aggregated into a single value (e.g. taking the median). A DON network’s service agreement defines how each report should be generated and the conditions in which a node’s stake can be slashed.
Any selection of nodes can be chosen to take part in a DON’s service agreement, including the existing collection of highly reliable and reputable node operators who already secure tens of billions of dollars within the DeFi ecosystem. Nodes can be filtered and selected using existing Chainlink reputation frameworks such as the Chainlink Market, which offers a permissionless marketplace that highlights historical node operator performance such as uptime, latency, response deviation, supported networks, data sources, and more.
Two-Tier Oracle Networks
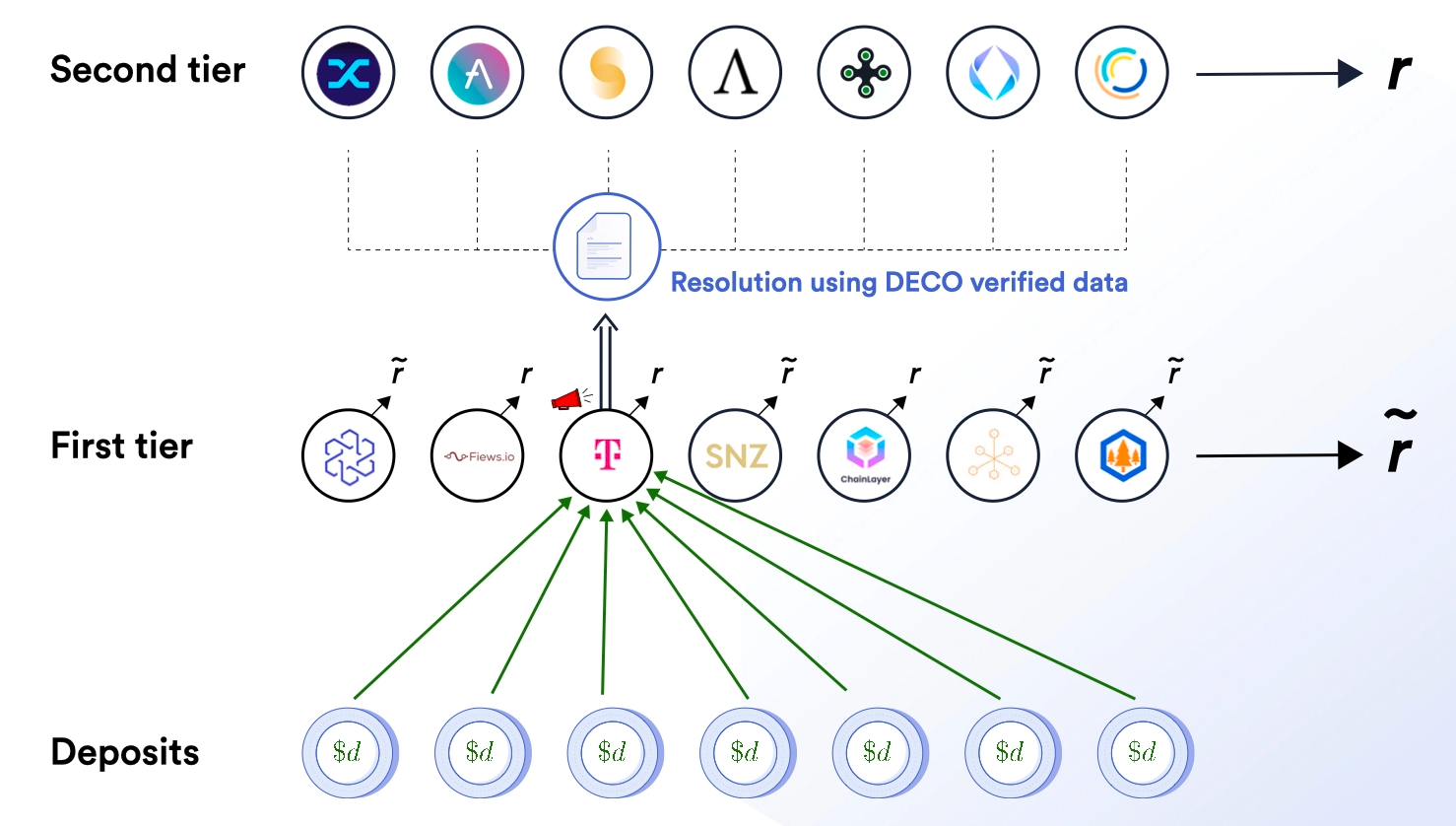
To ensure the terms of the service agreement are adequately fulfilled, a two-tier oracle network design will be used. This involves a high-efficiency and low-cost first-tier DON, made up of nodes that explicitly stake LINK tokens and take on the responsibility of continuously generating new aggregated oracle reports on a regular basis. Additionally, a maximum-security and higher-cost second-tier DON will be used to settle any disputes created regarding the validity of oracle reports generated by the first-tier. The two-tier oracle network design optimizes for efficiency during normal use, while prioritizing tamper-resistance and precision during second-tier arbitration to ensure nodes in the first-tier network are held accountable for malicious behavior and poor performance.
The Chainlink Network in its current implementation has operated for over two years, generating millions of on-chain transactions and securing tens of billions of dollars in the DeFi economy. There has never been a need for an arbitration layer, as the existing cryptoeconomic incentives have ensured the highly reputable Chainlink node operators continue to reliably publish accurate oracle reports on-chain without issue, even during blockchain network congestion, so as to not jeopardize their reputation or revenue. However, as an overabundance of caution, in the extremely unlikely chance that a dispute may arise, the Chainlink 2.0 model supports a built-in second-tier arbitration layer, providing even greater security assurances.
Cryptoeconomic Security of Second-Tier Networks via User Voting
In the rare case where a dispute would ever be raised on an oracle report generated by the first-tier oracle network, triggered by the watchdog/alerter mechanism described further below, the dispute would be settled by a slower second-tier committee consisting of the hundreds and eventually thousands of independent Chainlink users such as Aave, Synthetix, Compound, and more. If a dispute were ever generated, these users would vote on the accuracy of the original oracle report in question using a cryptographic TLS proof produced by DECO that provides definitive Zero-Knowledge Proof based evidence from one or multiple data providers. DECO provides efficient, low-cost, and tamper-proof arbitration, allowing second-tier participants to resolve disputes even without access to the original data source.
Because the security of each Chainlink users’ smart contract application, and user funds it contains, depends upon accurate oracle reports from the Chainlink Network, each second-tier voter is highly economically incentivized to correctly resolve disputes as to not jeopardize the security, reputation, and usability of their application or potentially harm the value of their application’s native token. Even under the extremely unlikely chance a minority of users vote maliciously, the vast majority of second-tier participants have a significant degree of skin in the game as their application fundamentally relies upon accurate oracle reports. With every additional paying user, the security budget of Chainlink oracle network not only increases, but so does the number of economically-rational second-tier participants.
These second-tier participants can consist of the core development teams managing Chainlinked applications as well as Decentralized Autonomous Organizations (DAOs) that consist of token holders who govern such applications. In the case of DAOs using their native governance token to vote on a second-tier dispute, the cryptoeconomic security of the second tier increases proportionally with the total economic value of all governance tokens used in the process. Any second-tier participants who vote against the DECO proof will be outvoted by the collection of users who are incentivized to vote for the accurate oracle report and will establish an on-chain record of voting incorrectly, which may damage their application’s reputation.
Prioritized Watchdog Reports
To ensure the second-tier oracle network is properly called into action if a dispute ever occurs, any node in the first-tier network can act as a watchdog by raising an alert if it believes the aggregate value from an oracle report is incorrect. During each reporting round, every node in the first-tier network is randomly assigned a public priority number that determines the order in which their alerts (if any) are processed by the second-tier network. For example, in a first-tier network with 100 nodes, each node would be assigned a unique number ranging from 1-100.
If an alert is raised by watchdog nodes and the second-tier network determines the original aggregate report of the first-tier was incorrect, then all of the staked LINK deposited by the malicious majority of first-tier nodes is slashed (taken away) and given to the alerting watchdog node with the highest priority number. This generates a strong financial incentive for first-tier nodes to act in an economically rational manner as watchdogs, particularly because if the aggregated oracle report is determined to be incorrect, the watchdog has an opportunity to earn a significant amount of slashed stake.
Concentrated Rewards
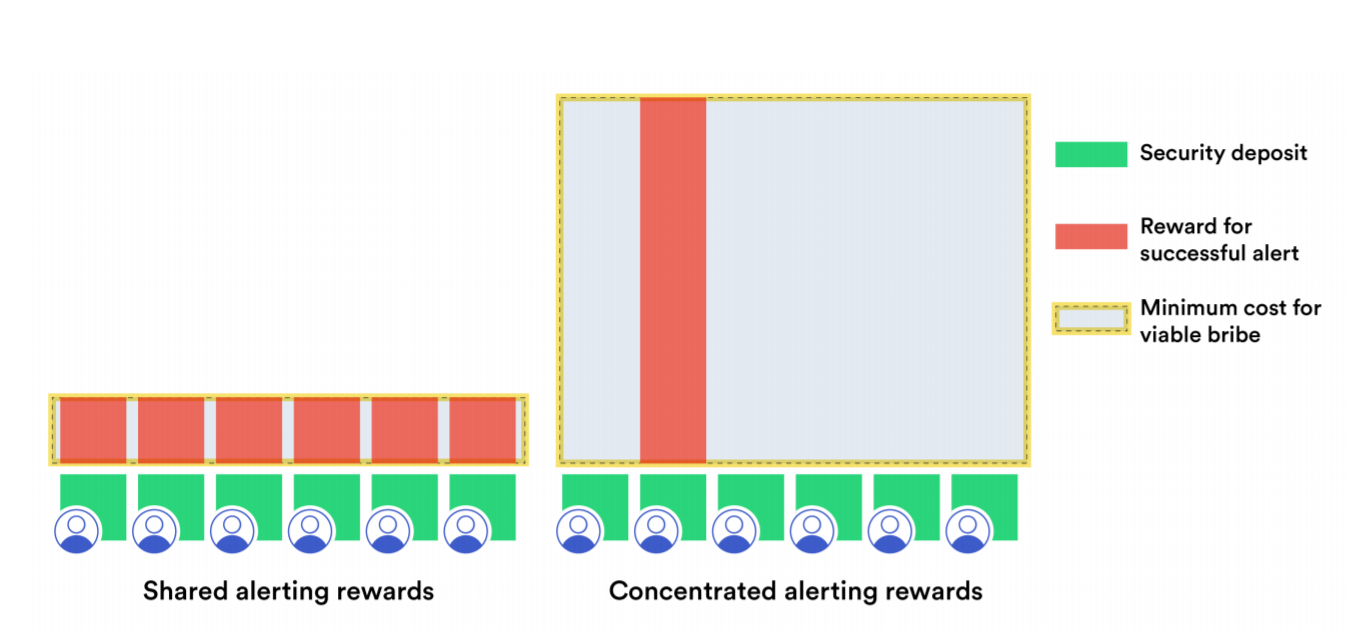
This prioritized watchdog report system drives reward concentration, resulting in a super-linear staking impact—where the budget required for a malicious actor to successfully corrupt a DON increases quadratically as a function of the number of nodes, creating maximum tamper-resistance against even well-capitalized adversaries. While the concentrated slashed stake reward is given to the highest priority node, any node in the first-tier network has the opportunity to act as a watchdog. Therefore, lower-priority nodes are still incentivized to raise an alert if the aggregate report is wrong, since they could win the slashed stake if the higher priority nodes did not raise an alert (e.g. those nodes were bribed or offline).
In order for a malicious actor to prevent any alerts from being raised to the second-tier, they would be required to bribe each first-tier DON node the full concentrated reward amount, significantly increasing the total minimum cost for a viable bribe to corrupt a DON. By giving a concentrated alerting reward to a single node, more cryptoeconomic security is created for the DON as a whole than would be possible sharing the slashed stake across all alerting nodes equally.
Quantifying the Security of Chainlink Explicit Staking
To quantify this super-linear staking impact dynamic, the whitepaper provides the following explanation:
Imagine there exists a first-tier DON with n nodes, where each node deposits d amount of stake, resulting in the total amount of stake in the network to be dn. The creation of an incorrect aggregate oracle report requires the majority of nodes to be corrupted, ensuring the collective value of the staked funds by malicious nodes is at least dn/2. If an alert is raised and deemed to be valid by the second-tier, then the highest priority watchdog would therefore earn at least dn/2 from all of the slashed malicious nodes. However, because any node can be a watchdog, each node would need to be bribed by at least this same amount to not raise an alert. As a result, the total budget an adversary requires to corrupt a first-tier DON is at least dn²/2, a value quadratic in the number of nodes.
The image below, taken from section 9.4.2 of the Chainlink 2.0 Whitepaper, provides a concrete example of how an increase of decentralization of a first-tier network quadratically increases the budget an adversarial actor requires to corrupt a DON.

Potential Outcomes of a Raised Alert
With this explicit staking mechanism, there are three potential outcomes that could occur after a first-tier DON has published an aggregated oracle report:
- Complete Agreement: All first-tier nodes are operating properly and collectively agree that the aggregated value within the oracle report is correct. Each node is paid a fixed per-round payment for their oracle services.
- Partial Agreement: Some nodes are offline or a minority of nodes report corrupted data, but the majority of nodes produce the correct value and the aggregate report is created with no alerts raised. All honest/operational nodes are paid a fee for their service while all faulty/offline nodes have their stake slashed by a modest amount (e.g. 10x the fee payment).
- Alert: If one or multiple nodes in the first-tier network believe the aggregate report is incorrect, they publicly trigger an alert, escalating verification to the second-tier network resulting in two possible outcomes:
- Correct alert: The second-tier network confirms the aggregate report from the first-tier was incorrect, resulting in the entire stake of all the malicious nodes being slashed and awarded to the highest-priority alerting watchdog.
- Faulty alert: The second-tier network agrees with the aggregate value produced by the first-tier network, deeming the escalation faulty and resulting in all of the alerting nodes seeing their stake modestly slashed.
As a result of the explicit staking mechanism, each node within the first-tier network not only has a strong incentive to provide accurate and reliable data for each report but also has a strong incentive to report the misbehavior of malicious nodes if the final aggregated oracle report is corrupted.
Misreporting Insurance
While all of the slashed stake from malicious nodes is awarded to the highest-priority alerting watchdog, users may still want compensation should an incorrect oracle report be generated. This is because in the multi-round alerting mechanism implementation, users can choose to optimistically accept new oracle reports from the first-tier (secured by the credible threat of arbitration) or can wait to see if any alerts are raised and resolved by the second tier.
Misreporting insurance can be provided by underwriters selling insurance to users who optimistically accept oracle reports from a first-tier oracle network. This insurance agreement can take the form of an on-chain smart contract that executes based on the signed oracle reports generated from the first-tier and second-tier oracle networks. If these reports differ, a payment can be automatically paid out to the policyholder. Because the Chainlink Network generates a large amount of data regarding the historical performance of each node and DON, the cost of insurance can be kept low while still being sustainable for the underwriters.
Conclusion
Through the creation of additional cryptoeconomic security via super-linear explicit staking, the Chainlink Network can scale to support next-generation hybrid smart contracts that secure increasing amounts of value. If smart contracts are to become the dominant form of digital agreement, this heightened level of cryptoeconomic security will be critical to providing users maximum guarantees around the accurate, timely, and tamper-resistant execution of decentralized applications that rely directly on oracle reports and computations.
The Chainlink 2.0 whitepaper provides a deeper analysis of Chainlink’s proposed explicit staking mechanism, such as additional nuances, design considerations, and explanations behind each component. If you are interested in learning more, refer to section 9 of the whitepaper.
- Chainlink 2.0 Lays Foundation for Adoption of Hybrid Smart Contracts
- Next Steps in the Evolution of Decentralized Oracle Networks
- SCRF Chainlink 2.0 Whitepaper Summary
If you’re a developer and want to securely connect your smart contract to off-chain data and computation using the Chainlink Network, visit the Chainlink developer documentation or connect with an expert.
