Eight Essential Cross-Chain Security Considerations
Listen to this blog post:
When selecting a blockchain interoperability solution, security should be the number one priority for everyone from top-tier protocols to world-leading financial institutions. As asset managers and banks increasingly tokenize real-world assets, the importance that end-users place on cross-chain security will only grow. In this post, we explore several industry best practices for selecting and integrating a cross-chain solution.
Zoom in. pic.twitter.com/5NLkYipvoI
— Chainlink (@chainlink) February 11, 2024
1. Use Independent Risk Management Networks
Robust security for a cross-chain solution requires independent monitoring of cross-chain transactions and the ability to detect suspicious activity and halt the network if required. This ability is necessary for a cross-chain solution to achieve the fifth and highest level of cross-chain security.
2. Use Decentralized Infrastructure
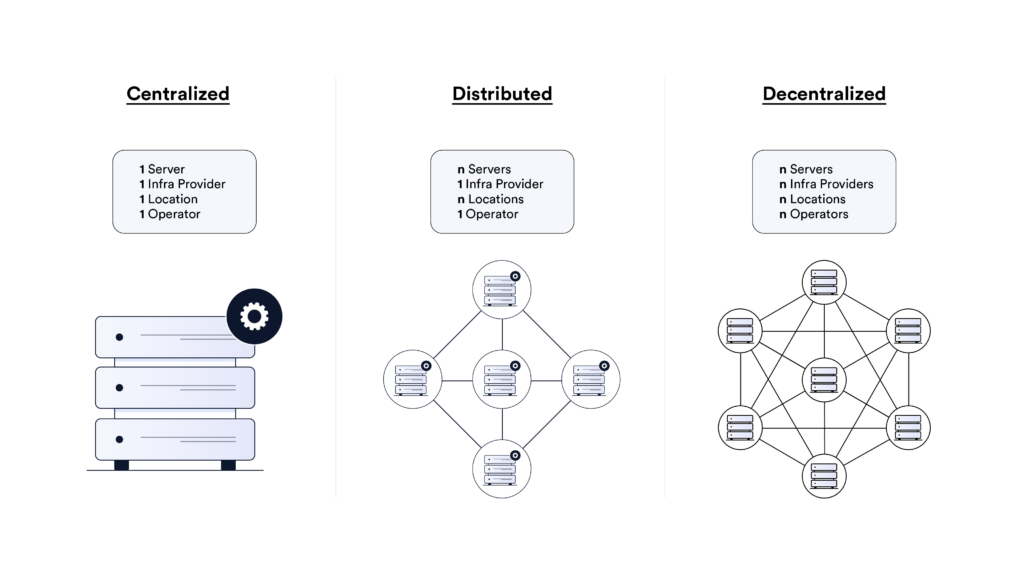
Eliminating single points of failure is critical for maximizing the security, reliability, and independence of a cross-chain protocol. A decentralized architecture featuring many nodes makes internal malicious attacks more difficult and ensures centralized parties cannot exert control over the network to gain an unfair advantage, such as by ordering transactions to frontrun end-users.
3. Use Established Protocols
Using only established protocols with a proven history of uptime, reliability, security, and high-integrity behavior is a necessity. This is not only important for securing your protocol, but also for attracting liquidity from users who value the high security standard that only established protocols can provide.
4. Understand the Implications of Vendor Lock-In
Cross-chain vendor lock-in occurs when a protocol becomes dependent on a specific cross-chain solution because the switching costs and/or operational impact are too high to quickly move to an alternate solution. This is critical to avoid in Web3 because applications must maintain their ability to quickly and easily integrate an alternative cross-chain solution if security vulnerabilities and reliability issues arise. Historically, assuming that your cross-chain solution is going to last longer than your protocol has been a costly mistake for many. Additionally, granting token permissions to cross-chain solutions that are neither fully secure nor future-proof is inherently high risk.
Moreover, as the blockchain landscape is dynamic and new chains are frequently emerging, it’s important for dApps to be able to connect to the most liquid and in-demand ecosystems as they evolve. The easiest way to avoid vendor lock-in is to leverage a cross-chain solution with open standards, safeguarding against obsolescence.
5. Consider Risks Around Multi-Bridge Architecture
Beyond introducing unnecessary trust assumptions, multi-bridge architectures also decrease the security of your protocol across multiple vectors. Architectures that allow any bridge to mint and burn tokens increase the attack surface for malicious actors to target, while a bridge that uses multiple cross-chain solutions to reach consensus in a multisig pattern reduces liveness and increases costs, and is complex to audit, implement, and maintain. Additionally, multi-bridge architectures increase integration time and maintenance costs, make it significantly more challenging for users to verify the security assumptions of your app, and enable users to access potentially insecure bridges.
By only interacting with the onchain economy via a single high-security cross-chain solution instead of using bridges, protocols and institutions can enhance the security of their application while reducing development requirements and ongoing maintenance costs.
6. Get Your Code Audited
Smart contract audits are detailed analyses and reviews of your application’s code to preemptively identify security vulnerabilities. This enables you to remedy them before deploying to mainnet and prevent costly exploits by malicious actors. Audits are important for all Web3 applications responsible for securing value, but particularly for cross-chain apps given that $2.75B in value has been hacked from them. Learn more about how to audit a smart contract.
7. Set Rate Limits on Token Transfers
Rate limiting refers to the ability to cap the amount of value that flows across a cross-chain solution over a given time period. It adds an extra layer of security that limits the impact of an attack, which is especially important for protocols securing a large amount of value.
8. Plan Ahead for a Multi-Chain Ecosystem
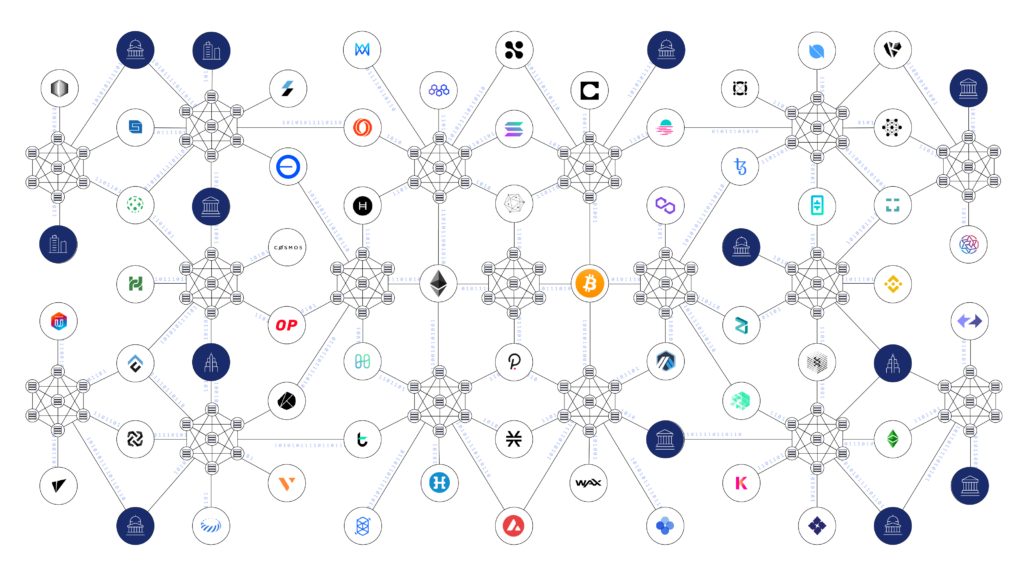
With the future of Web3 set to be a multi-chain ecosystem with hundreds or even thousands of public and private blockchains, the type of cross-chain solution selected should be able to securely and efficiently connect various chains. In contrast, native bridges only provide a single lane on each bridge, which means a multi-chain ecosystem that relied on native bridges would require many separate bridges, creating complexity and expanding the attack surface. In order for tokens to be sent between layer 2s in a multi-chain ecosystem relying on native bridges, they would need to be sent via a layer 1 or use wrapped tokens—introducing liquidity management issues.
Ideal for a multi-chain ecosystem and in contrast to bridges, a cross-chain solution with a secure burn and mint mechanism is simple to deploy across multiple chains and enables liquidity to flow seamlessly, including between layer 2s.
Conclusion
Protocols like Swell moved from alternatives to Chainlink Cross-Chain Interoperability Protocol (CCIP) because it provides an open standard for cross-chain communication, can seamlessly connect to any public and private blockchain along with legacy systems, is actively monitored by the Risk Management Network, and features unparalleled levels of decentralization. Designed with the above considerations in mind, along with an array of defense-in-depth approaches, CCIP is the most secure cross-chain solution available. That’s why world-leading organizations powering the global economy—such as Swift, DTCC, ANZ Bank, and Vodafone—are actively exploring CCIP.
“Only CCIP reaches the fifth level of cross-chain security using multiple levels of decentralization, which we do believe financial institutions will eventually need to safely manage quadrillions of dollars in transactions, eventually bringing the entire capital markets industry onchain.”—Sergey Nazarov, Co-founder of Chainlink
