The Five Levels of Cross-Chain Security
Billions of dollars in user funds have been lost to bridge hacks. Beyond harming individuals, these losses slow industry adoption and undermine Web3’s efforts to create a robust onchain economy where trillions in tokenized assets are seamlessly transacted on a daily basis. Cross-chain exploits can be avoided if the industry moves away from centralized and single-network bridges toward a defense-in-depth cross-chain solution featuring multiple layers of decentralization and onchain risk management.
This blog outlines the five levels of cross-chain security and showcases how Chainlink CCIP sets a new industry standard in cross-chain communication, capable of supporting a secure and scalable cross-chain economy for both DeFi and traditional finance.
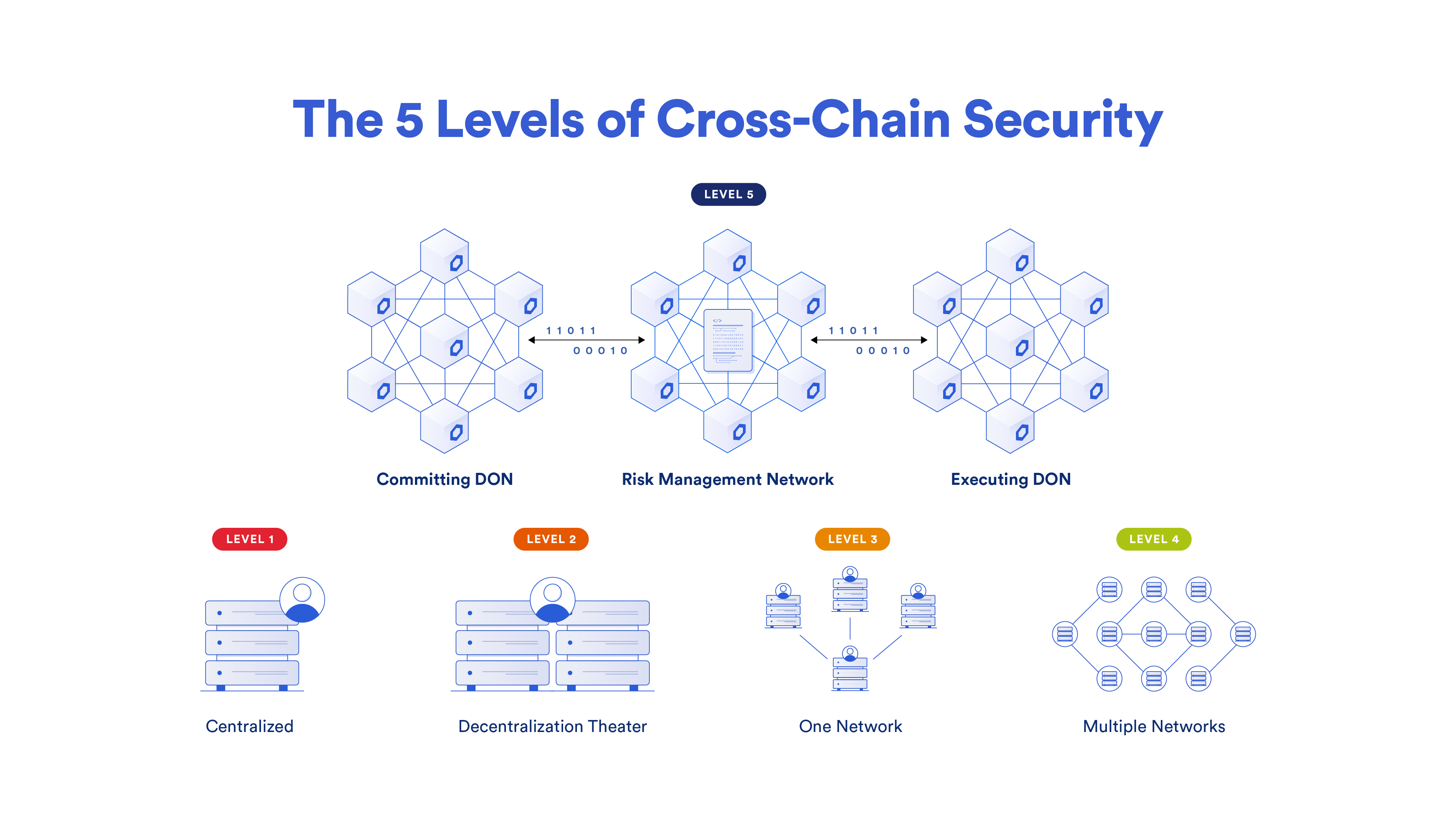
Level 1: Centralized
The most basic cross-chain solution is one where a single entity utilizes a single server that’s secured by a single private key. This architecture introduces a variety of critical attack vectors, creates single points of failure, and presents conflicts of interest that put user funds at serious risk. Centralized cross-chain solutions ultimately undermine the advantages that Web3 provides over existing Web2 solutions.
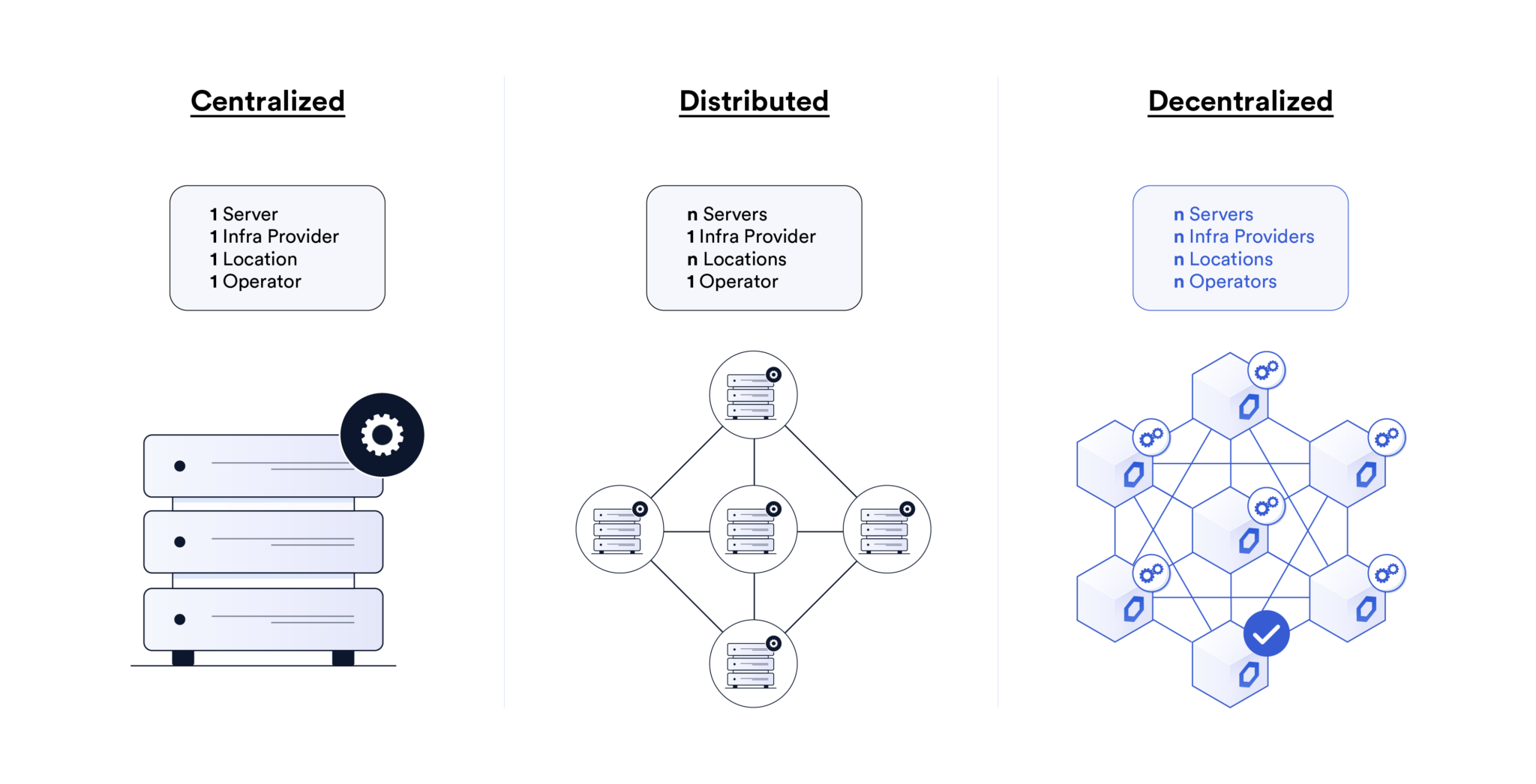
Level 2: Decentralization Theater
Decentralization theater is when a protocol creates the appearance of decentralization without actually being meaningfully decentralized. This often takes the form of a single entity maintaining control of two or more servers to give a false impression of decentralization. This cross-chain design is especially dangerous because it projects a false sense of security, which may lead to users relying on solutions that they normally wouldn’t use if they had full disclosure of their centralized design.
One example of this can be seen in the case of Multichain: “Despite their previous assurance of decentralization, the Multichain team revealed that the protocol’s multi-party computation servers and private keys were all under the exclusive control of [Multichain CEO] Zhaojun, which were handed over to police. Without access to such items, the protocol had to shut down, and its team members were nowhere to be found.”
More recently, the Mixin Network experienced an approximately $200M exploit after a cloud service-related compromise, highlighting the dangers of cross-chain infrastructure that has centralization risks and single points of failure.
Trust less. pic.twitter.com/ztjMXePvsy
— Chainlink (@chainlink) September 24, 2023
Level 3: One Monolithic Network
A single decentralized network made up of independent node operators with distinct private keys is a clear step-change improvement in security from Level 2. However, a single monolithic network simply cannot scale to support a cross-chain economy with heavy transaction volumes, much in the same way that a single blockchain is unlikely to support the whole of Web3. When all bridges are secured by a single network, spikes in usage on a single bridge can then affect the reliability of all other supported bridges.
The other concern to look out for is the decentralized network having a large dependency on a single infrastructure provider, such as a cloud service. According to Cisco network intelligence company ThousandEyes, there were 15,000 cloud outage events in 2022 alone.
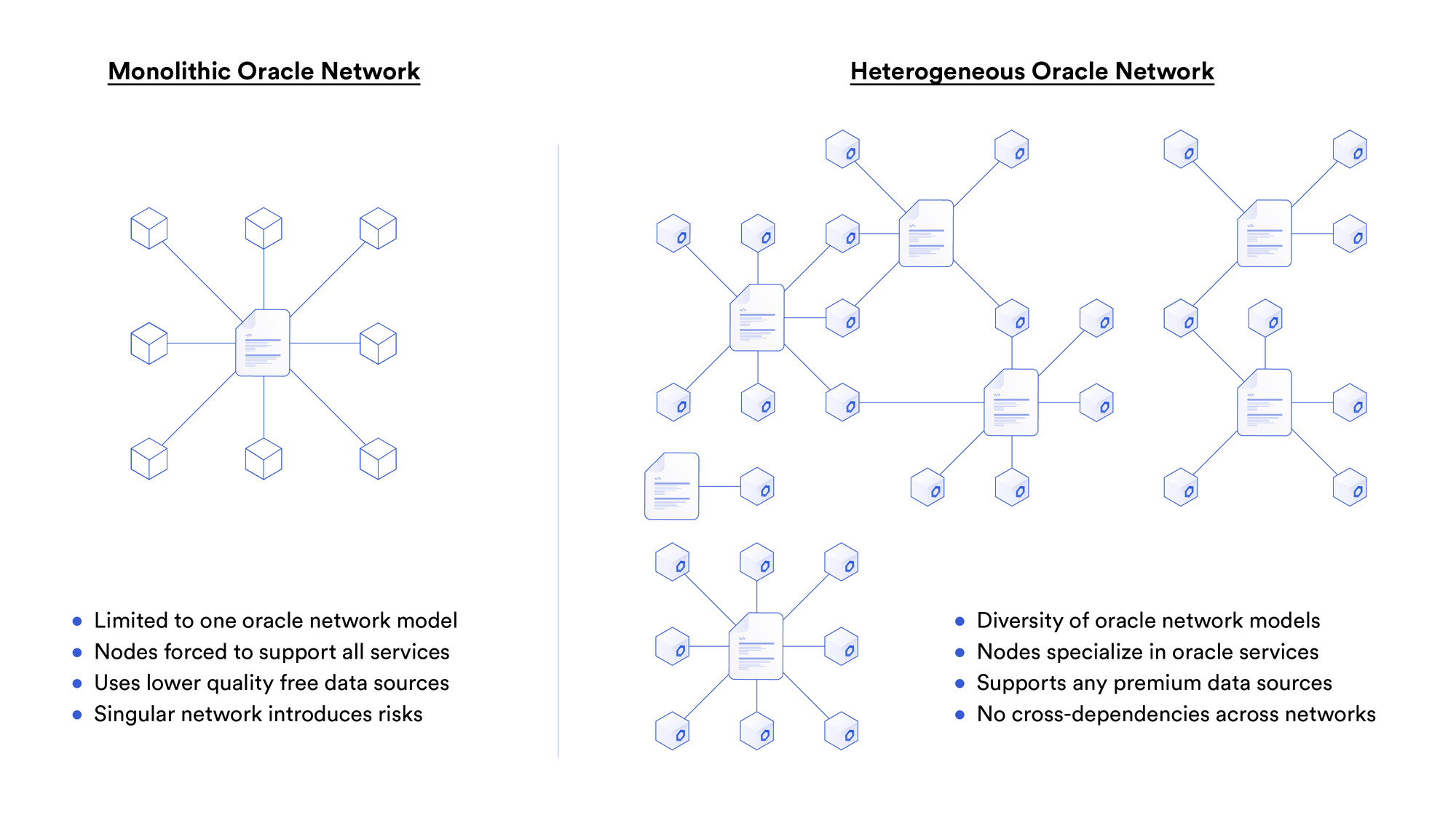
Level 4: Multiple Decentralized Networks
Utilizing multiple independent decentralized networks (DONs) to underpin a cross-chain solution eliminates single points of failure and allows the network to handle greater transaction volume and deal with sudden spikes in usage. For a DON to perform a function, there needs to be a supermajority consensus among its participants. By isolating bridges as independent networks, users can customize and scale the security of each bridge. Chainlink services have been operating at level-4 security for over three years, successfully enabling over $12 trillion dollars in transaction value.
However, due to the complexity of cross-chain transfers and the massive amounts secured, additional risk management techniques are necessary to establish a universal cross-chain standard that can support trillions of dollars in value flow.
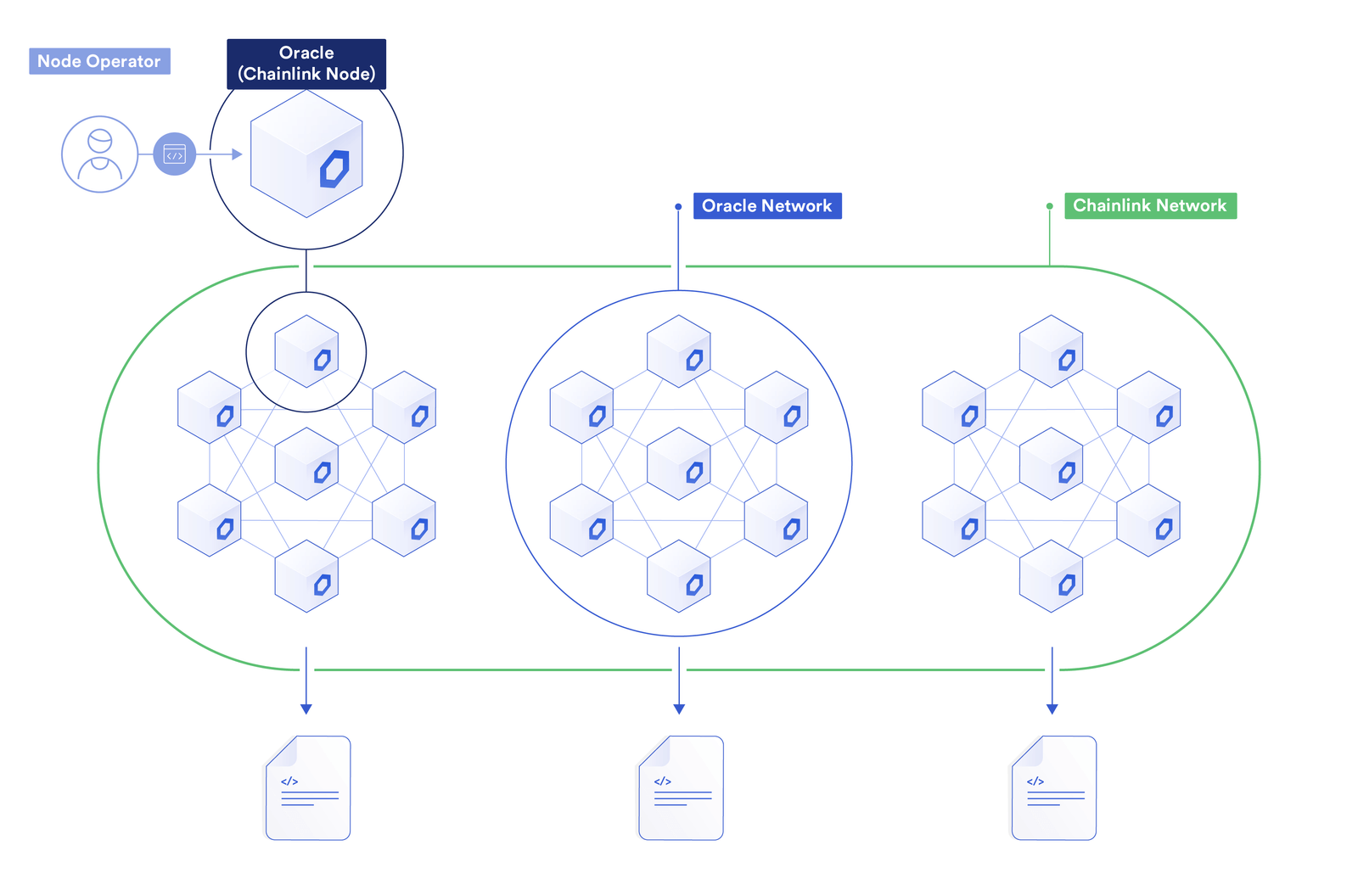
Level 5: Defense-In-Depth
Level-5 cross-chain security achieves unprecedented levels of decentralization by utilizing multiple decentralized networks to secure a single cross-chain transaction, along with incorporating additional risk management systems to identify risks and take actions to prevent them, such as by implementing emergency shutdowns or imposing rate limits.
The fifth level of cross-chain security doesn’t just give you one independent network for your cross-chain data or messages; it gives you multiple networks, made up of independent nodes all working together to secure each bridge.
While many bridge solutions operate using a single node or multiple nodes under the control of one key holder (e.g., Multichain), the fifth level of security uses multiple independent nodes with their own independent key holders and even splits them up into two separate groups of nodes: the transactional DON nodes and the Risk Management Network nodes. One additional key feature of the separate networks in CCIP is the creation of two entirely separate implementations, with two independent code bases, so that CCIP features an unprecedented level of client diversity/decentralization for cross-chain interoperability.
With CCIP you get:
- Multiple independent nodes run by independent key holders.
- Three decentralized networks all executing and verifying every bridge transaction.
- Separation of responsibilities, with distinct sets of node operators, and with no nodes shared between the transactional DONs and the Risk Management Network.
- Increased decentralization with two separate code bases across two different implementations, written in two different languages to create a previously unseen diversity of software clients in the bridging world.
- Never-before-seen level of risk management that can be rapidly adapted to any new risks or attacks that appear for cross-chain bridging.
Featuring a Committing DON, the Risk Management Network, and an Execution DON, the Chainlink Cross-Chain Interoperability Protocol (CCIP) is the only cross-chain solution that can provide cross-chain token transfers and messaging with complete level-5 security. Let’s quickly walk through how multiple decentralized networks come together in CCIP to create a new industry standard for cross-chain security and reliability.
Step 1: Committing DON
The Committing Decentralized Oracle Network (DON) provides foundational security. It commits to CCIP messages on the source chain that are finalized by creating a Merkle tree of these messages and publishing its Merkle root on the destination chain.
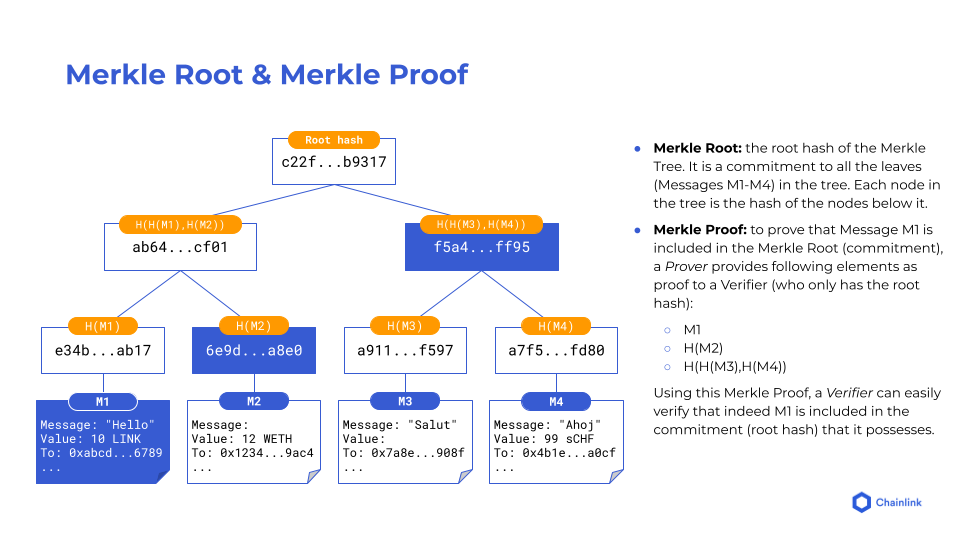
Step 2: Risk Management Network
Next, an independent Risk Management Network—built as an independent implementation, on a different stack, in a different programming language—verifies the Committing DON by performing the same task. If the Merkle roots match, the onchain Merkle root gets “blessed.” Therefore, two independent networks, each with distinct sets of node ops, must commit to the messages for them to be executed. The Risk Management Network can support additional conditions to what it sees as a risk, enabling it to rapidly adapt to new attacks and adversaries as they appear.
Additional defense-in-depth measures of CCIP include the ability for the Risk Management Network to trigger an emergency shutdown if it detects suspicious activity, as well as customizable rate limits on the number of tokens able to be transferred within a given time period, and a timelock contract where a quorum of CCIP node operators can veto proposed upgrades or alternatively explicitly approve onchain configuration upgrades before deployment.
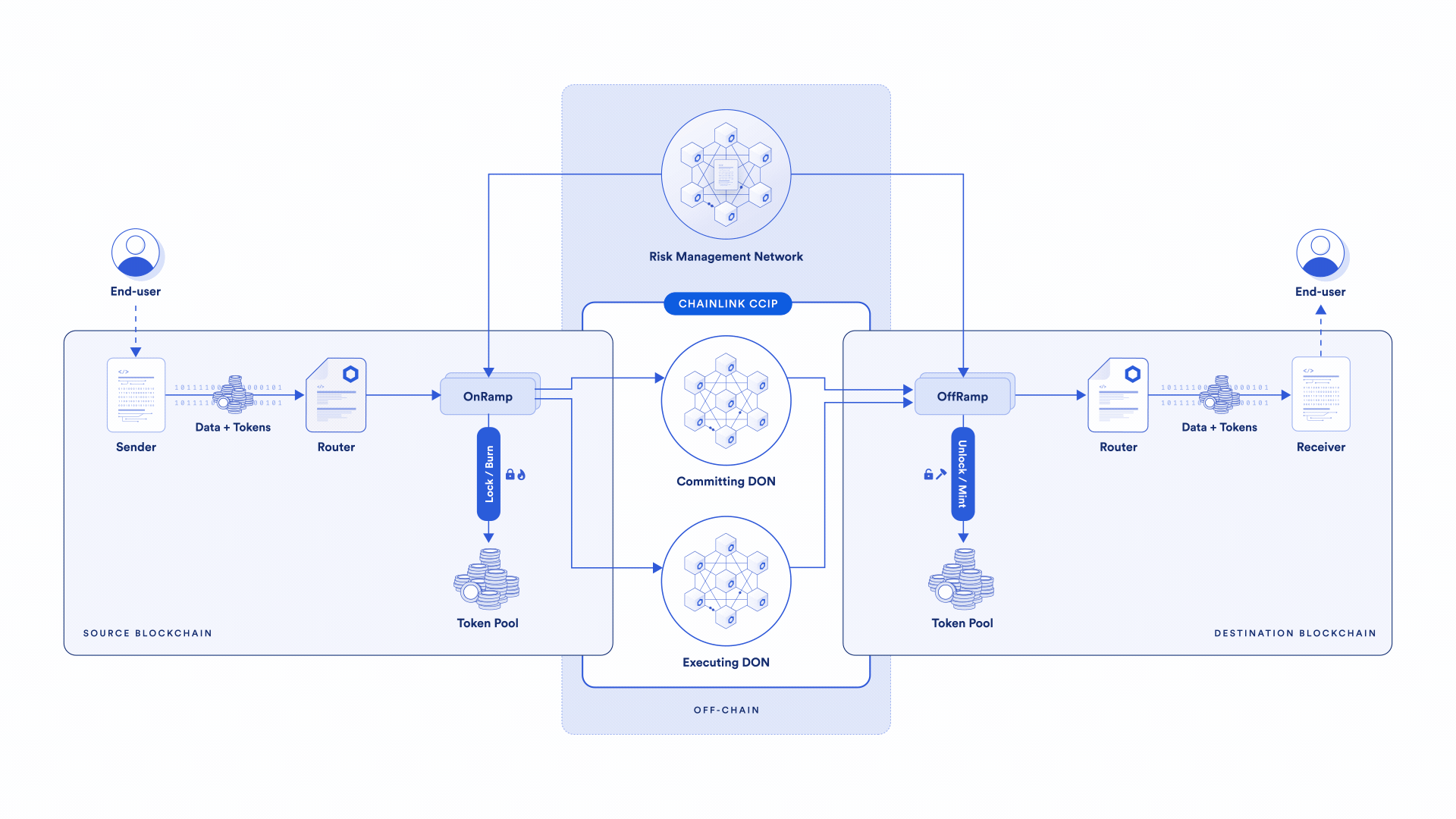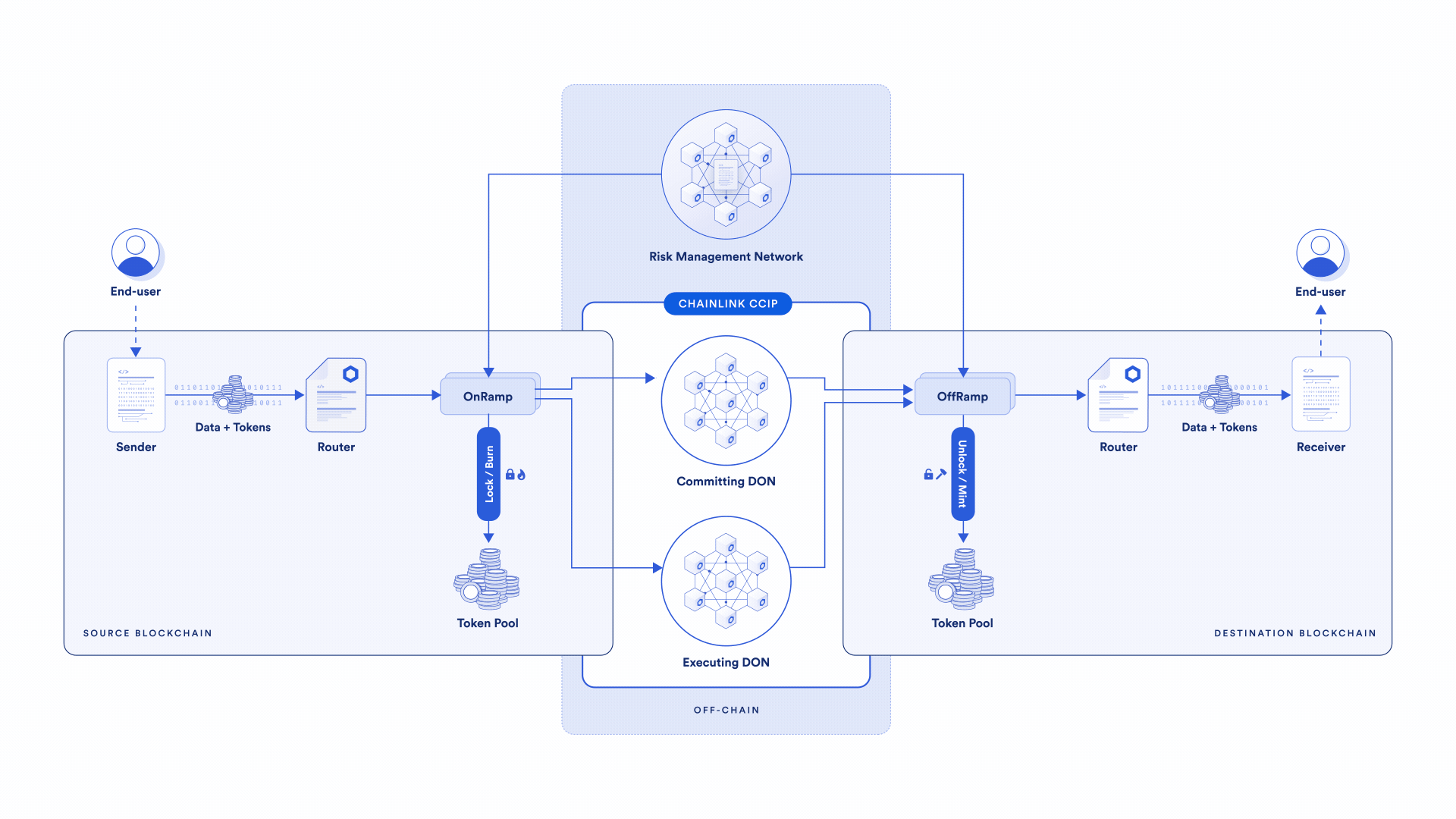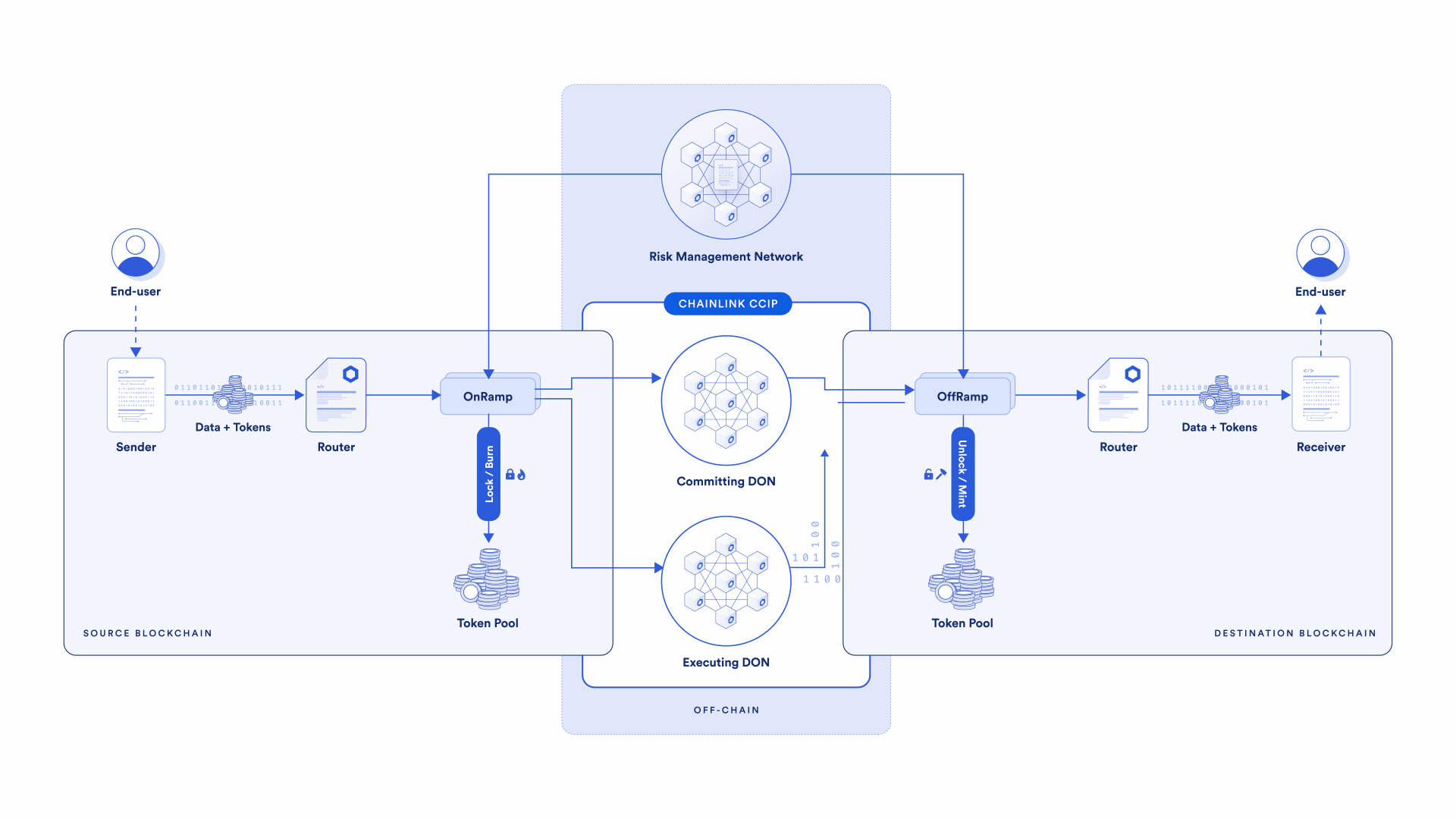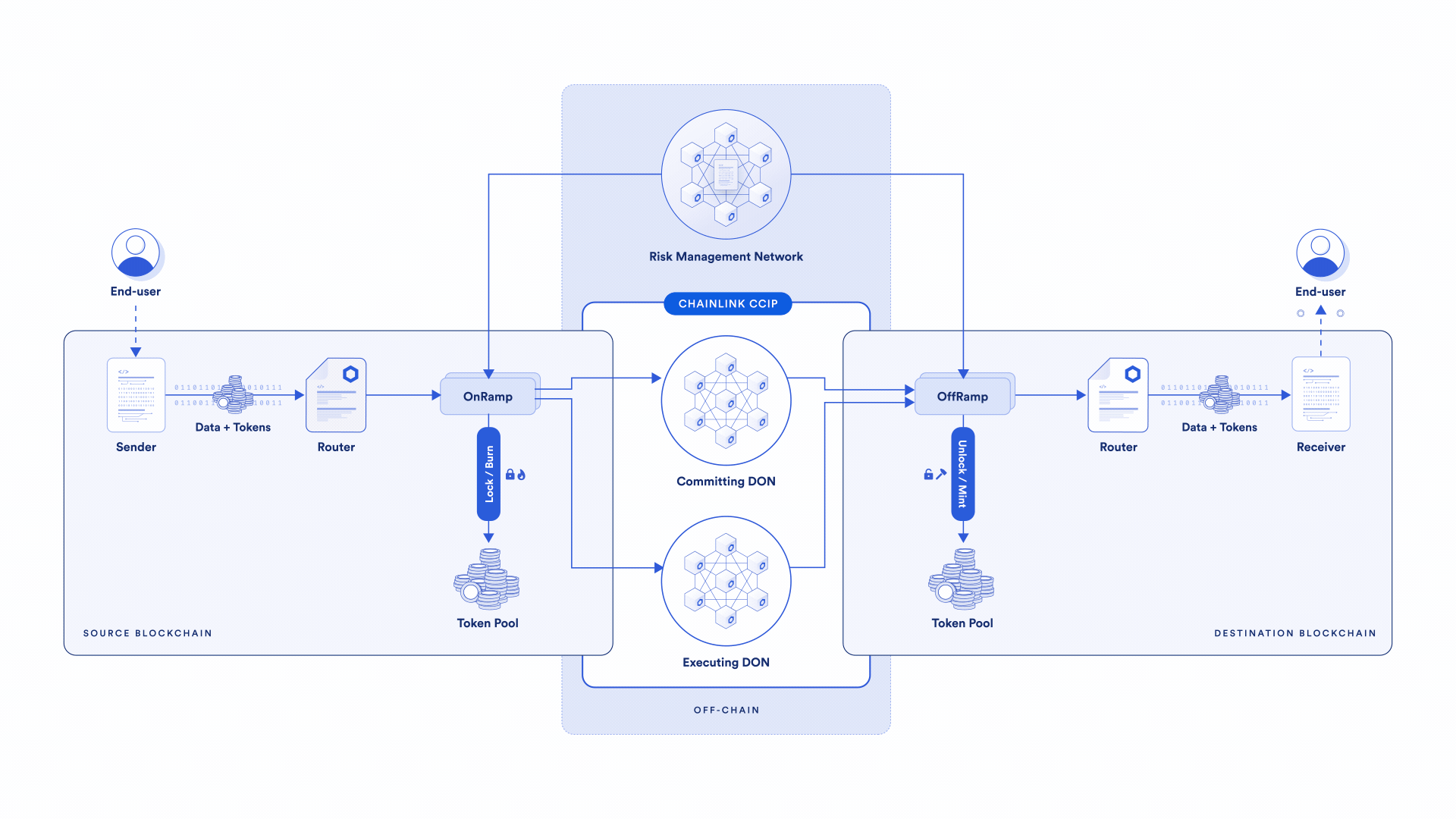
Step 3: Executing DON
The Executing DON submits messages to the destination chain for execution, along with cryptographic proof that the messages are included in the blessed Merkle root. CCIP verifies these proofs against the blessed Merkle root, and if successful, the messages are executed on the destination chain.
Chainlink CCIP: The Level-5 Interoperability Standard for Web3 and Global Finance
“Only CCIP reaches the fifth level of cross-chain security using multiple levels of decentralization, which we do believe financial institutions will eventually need to safely manage quadrillions of dollars in transactions, eventually bringing the entire capital markets industry onchain.”—Sergey Nazarov, Co-founder of Chainlink
Chainlink CCIP gives Web3 protocols and financial institutions access to cross-chain interoperability with level-5 security. That’s why leading institutions such as Swift, DTCC, and ANZ, along with premier DeFi protocols like Aave and Synthetix, are already working with CCIP to explore and enable cross-chain use cases. Backed by an unparalleled level of security and decentralization, CCIP is positioned to become the universal interoperability standard between any public and private blockchain.
Zoom in. pic.twitter.com/5NLkYipvoI
— Chainlink (@chainlink) February 11, 2024
If you want to learn more about CCIP’s underlying architecture and code and start building highly secure and reliable cross-chain use cases, check out the CCIP developer documentation.
