Trust-Minimized Applications: The New Standard
In a well-functioning society, trust is abundant, serving as the glue that underpins productive social and economic activities. However, a high level of trust in society doesn’t necessarily mean there is an equivalent level of truth. When belief in how a system works diverges from how the system actually works underneath the hood, cracks will appear and begin to be noticed by its participants, eventually snowballing into conflict and demand for system overhauls.
Society is currently in the midst of a growing misalignment between the perceived and the real relationships that exist between users and established institutions—both in regards to the actual legal obligations written into contracts and people’s belief in the truth of marketed statements and their eventual execution. This misalignment is surfacing in society across a variety of fronts, with consumer prices increasing in spite of institutional “promises” to control inflation, personal data breaches in so-called “secure” databases, user account limitations despite the promotion of “fair” financial access, and selective censorship from supposedly “unbiased” social media companies.
Fortunately, blockchain and oracle infrastructure has begun to emerge, providing cryptographic guarantees that whole or specific functions of digital contracts will execute as agreed upon. This new “cryptographic truth” underpins a coming wave of next-generation applications for which trust-minimization is a fundamental part of their DNA.
In the following blog, we will dive deep into a variety of similar-sounding yet distinct terms related to trust before looking deeper at cryptographic truth and how it’s setting the stage for a new competitive battleground for Web2 and Web3 applications centered around what type of trust-minimized guarantees they offer to users.
First Principles: Trusted, Trustless, and Truth
Before exploring the concept of trust-minimized applications, it’s important to first define the terms trusted, trustless, and truth, as well as look at the relationships between them.
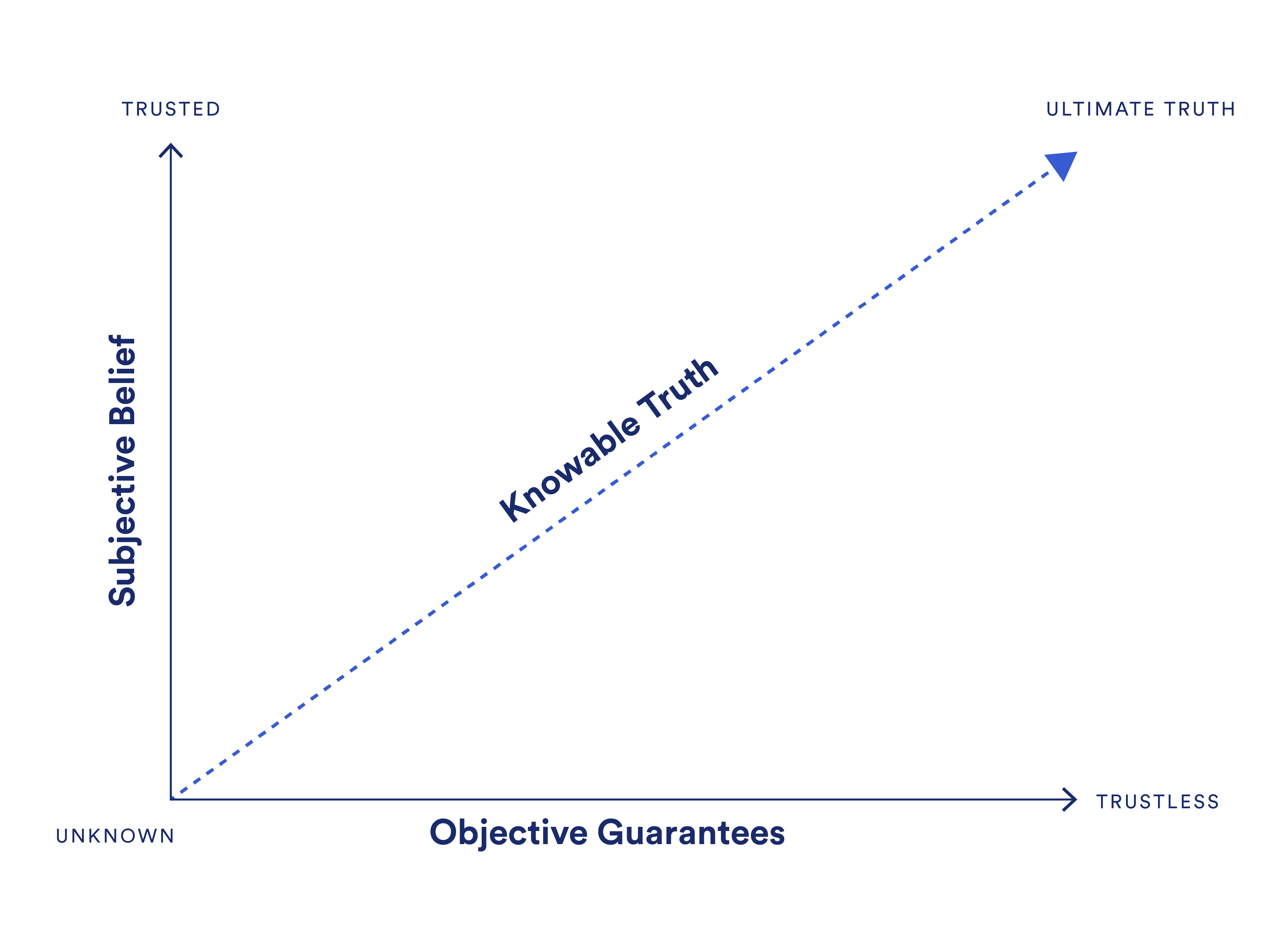
Trusted is a state of strong belief in an assumption about one’s self, other people, or external events holding true. For instance, if one walks down a public street, they may believe it’s safe because they trust in their self-defense skills, the good mental health of others, and/or that the penalties for committing a crime are high enough to deter potential attackers.
Trust is ultimately a subjective belief, meaning how much trust one places in something will differ from person to person. However, societal trust can be represented as the average magnitude of belief the collective of individuals has in an assumption holding true. A maximum state of trust is when someone fully commits to a belief, even if they don’t have all the evidence needed to form such a concrete opinion (i.e. faith). In reality, most beliefs are represented as a percentage, such as someone being 50% confident that it will rain tomorrow.
Trustless is a state of guarantee that something will occur exactly as intended, whether that be because of the fundamental laws of nature, highly repetitive patterns, or some type of well-thought-out mechanism design. Trustless can be generally thought of as determinism—a situation where a specific input will always lead to a specific output. For instance, a mathematical equation such as x + 1 = y will always generate an answer (y) that is exactly one more than x. Gravity is another example, where the statistical chance of someone on Earth coming back down to the ground after they jump is high enough to be considered essentially a guarantee.
It’s debatable how many situations in the world are fully guaranteed, as most processes have some level of uncertainty, even if it’s just because of unknown unknowns. However, situations can move further towards a trustless state by incorporating disciplines such as cryptography, physics, and game theory to create greater statistical certainty around outcomes—particularly by reducing the amount of randomness and volatility derived from external variables. So while a process might not be fully trustless, specific parts of it can come with certain guarantees or statistical probabilities.
Truth is when the magnitude of one’s belief in an assumption holding true matches the objective statistical certainty of such an outcome. It’s important to note that one can only know the truth to the extent of available information one has access to (i.e. knowable truth). This is key to how truth scales, as knowing the ultimate truth of a situation may not be achievable if some information is unknowable or purposely hidden.
When a person’s belief in a process outcome is greater than the actual statistical guarantees currently present for such an outcome, they can generally be thought of as naive or misled about the truth or simply a speculator on the future changing. When a person’s belief in a process is less than the statistical guarantees present, then they can be thought of as skeptical or unaware of the truth.
The value of individuals and society as a whole being in alignment with truth and moving further along the trust line is that it creates a better foundation for logical decision-making and increased understanding as to why outcomes occur. This generally leads to more realistic expectations, less speculation, and a reduction in conflict throughout society. Alignment with truth is ultimately the only way to increase desired states of societal well-being such as peace, solidarity, and high collective consciousness.
Placing Web2 and Web3 Applications on the Truth Alignment Spectrum
Let’s see where Web2 and Web3 applications currently reside on the truth alignment spectrum. Then, in the next section, we will examine how applications can move in different directions on the spectrum.
Note: Web2 is used as a generalized term to include any service that does not make use of a blockchain on the backend. Web3 is used to describe any application that uses a blockchain as its backend computing infrastructure. These are generalizations, so it’s not a perfect representation, and there will be exceptions to the rule and differences of opinion.
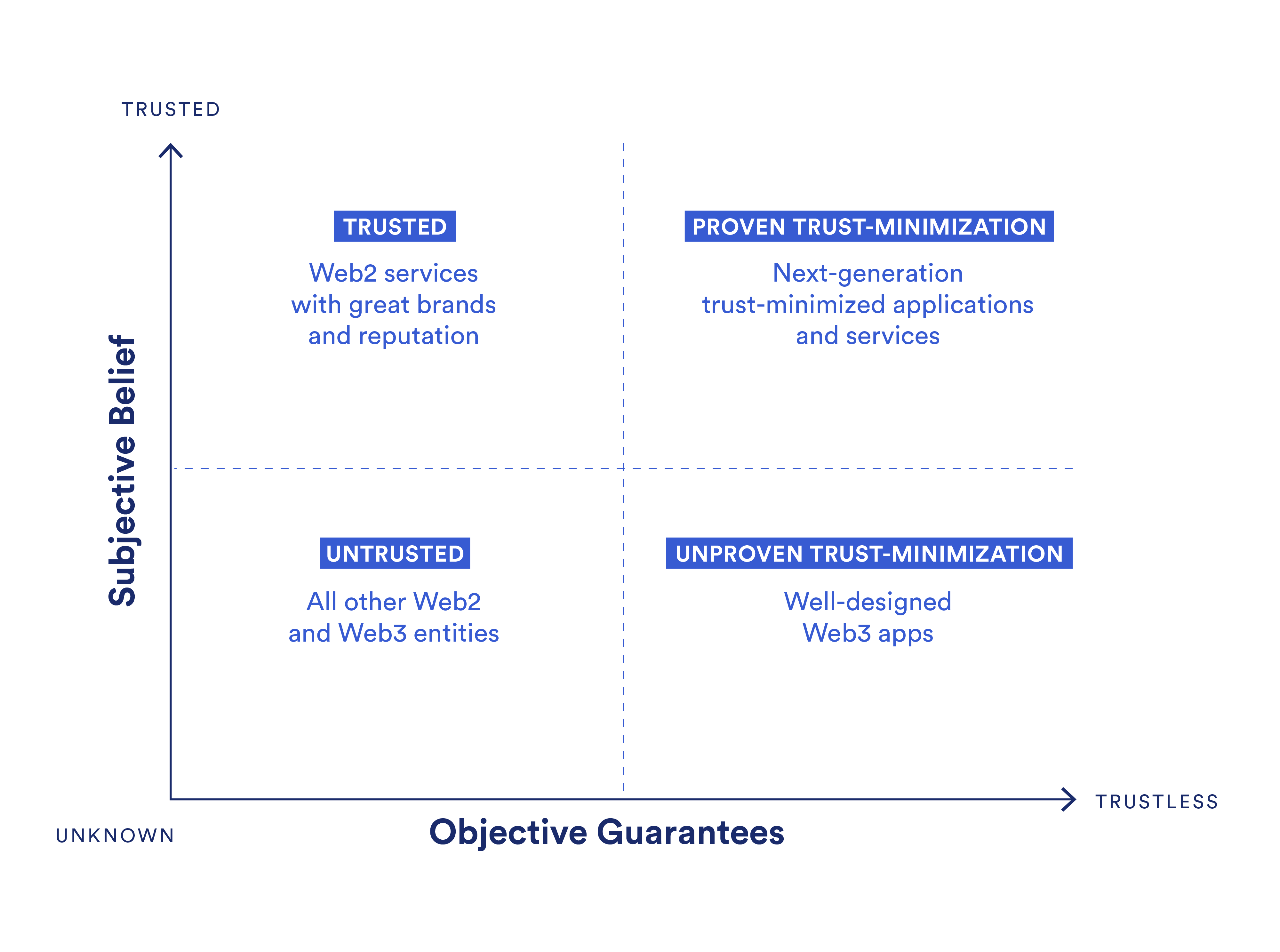
Untrusted: The bottom-left quadrant represents a wide variety of less trusted and less proven Web2 services and Web3 applications. A project may reside here for a variety of reasons, but some common ones include the project being relatively unknown, its design being flawed or unproven, or it not providing users with enough evidence of its soundness. Most mid-to-low level Web2 companies and Web3 startups would fall into this area.
Trusted: The top-left quadrant contains highly trusted Web2 services with strong brands, useful services, and/or wide consumer adoption. However, these trusted services are supported by relatively weak guarantees compared to Web3 technologies in terms of features such as transparency, user auditability, censorship resistance, and other concerns stemming from centralization. Their trust model revolves more around promises that are backed by their reputation and legal contracts. Most well-known enterprises or successful small businesses would exist here.
Unproven trust-minimization: The bottom-right quadrant is made up of Web3 applications that generate higher levels of trust-minimization using techniques such as cryptography, economic incentives, and distributed consensus while also having a baseline level of success running in production. However, Web3 as a whole is a relatively new and untested industry compared to Web2, meaning most Web3 applications (i.e. dApps) have yet to achieve scale or widespread public belief in their guarantees beyond a small niche of users. This section would likely consist of some so-called “blue chip” Web3 applications.
Proven trust-minimization: The top-right quadrant is the ideal state where an application/service achieves widespread belief and adoption while also offering verifiable guarantees that its operations are sound. Very few, if any, Web2 or Web3 applications fall under this category, mostly because of the infancy of blockchain and oracle technology and the public’s limited understanding of the value of objective guarantees. However, this quadrant will undoubtedly be the area where next-generation applications do battle, with Web2 services and Web3 applications increasingly attempting to migrate here over time to remain competitive.
How To Move Through the Truth Alignment Spectrum
There are four ways a project or company can move on the spectrum from an original starting point: up, down, left, and right. Let’s look at each one to get a general sense of what drives these movements:
- Up: Trust can be gained in a variety of ways, some of which include executing marketing campaigns to increase awareness, increasing adoption to show strength in numbers, attracting public support to showcase buy-in from influential people, or simply waiting for people to get used to a new service. Most Web3 apps actually need to gain consumer trust by demonstrating their value proposition over a longer timeframe, as well as extend awareness of the value of Web3 guarantees to a broader audience.
- Down: Losing trust can stem from a series of mistakes, the exposure of a previously unknown flaw, poor relationship management, or the launch of competitors that completely reframe the entire landscape of trust in a specific market vertical. For instance, new Web3 dApps may make existing Web2 apps and previous Web3 apps look less trustworthy over a long enough timeframe given that more guarantees are likely to be reciprocated with higher levels of trust. Truflation—a project building independent, open-source inflation rate data—is pushing to reshape the trust society has in official CPI metrics, potentially lowering the usefulness of official CPI data if Truflation is more consistently reflective of reality.
- Left: A reduction in guarantees is usually the result of new research or a new product that redefines the technological landscape. For example, the successful introduction of quantum computing has the potential to make existing forms of cryptography insecure, moving applications that rely on it to the left on the spectrum if they fail to upgrade to a quantum-resistant form of cryptography.
- Right: An increase in guarantees provided to users is now achievable through blockchain and oracle technologies, both of which generate a unique form of trust-minimization. These trust-minimized guarantees are generated through techniques such as cryptography, distributed consensus, economic incentives, or simply proving the soundness of guarantees by battle-testing them in a variety of situations over time.
Cryptographic Truth: A New Method of Trust-Minimization
Trust-minimization refers to a general set of techniques designed to make processes more predictable by accounting for all variables and either controlling, incentivizing, or severely minimizing their impact. Instead of users needing to believe in certain assumptions holding true—whether because of altruism, personal relationships, brand reputation, or legal contracts—they receive a certain set of guarantees rooted in math, physics, game theory, and/or mechanism design that specific assumptions will hold true to a very high statistical level of certainty.
The introduction of blockchains and oracles has provided society with novel infrastructure that supports the development of next-generation trust-minimized applications and services. This method of generating trust-minimization using blockchains and oracles is generally referred to as cryptographic truth.
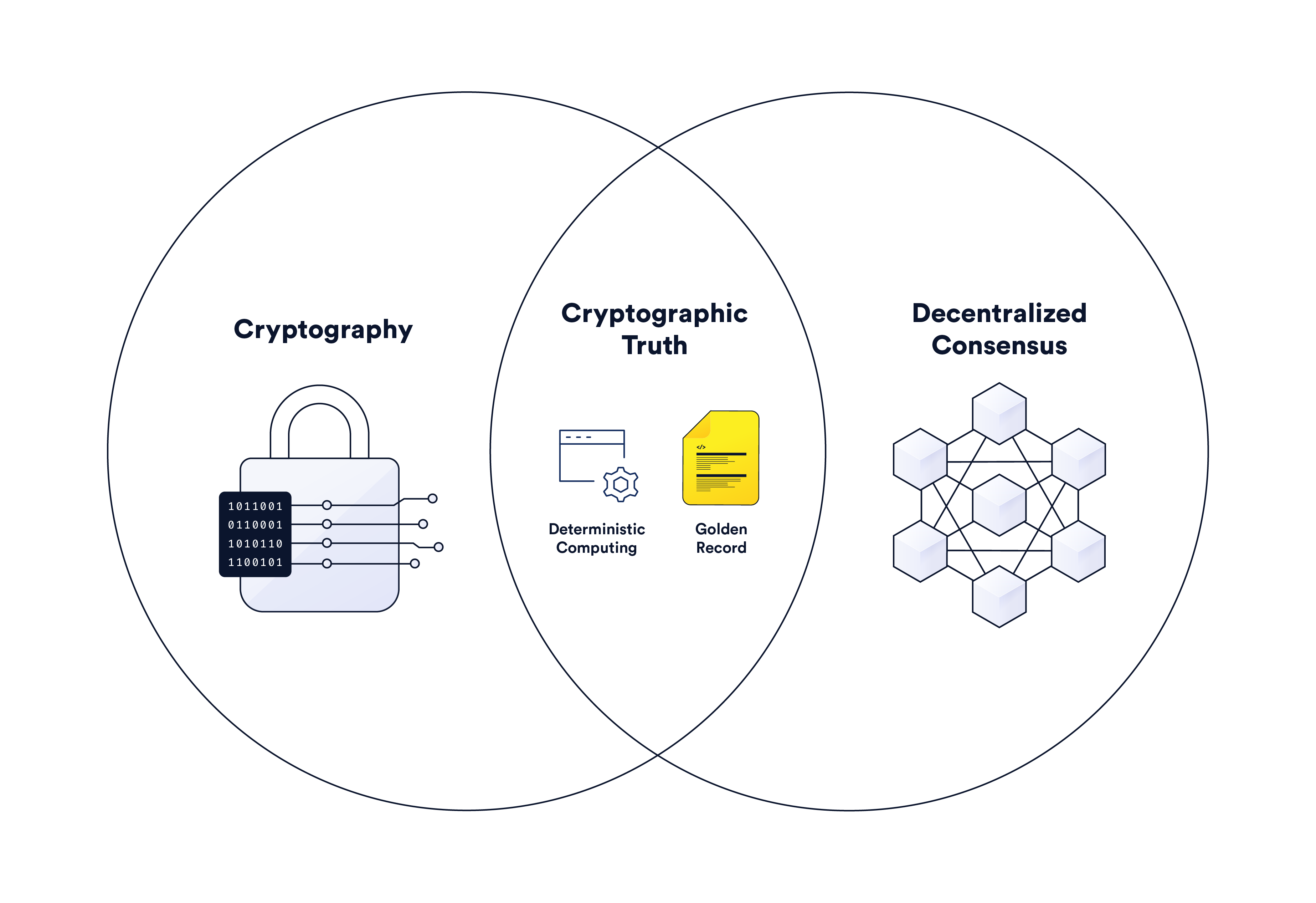
In a general sense, cryptographic truth uses cryptography and decentralized consensus within a game-theoretical setting comprised of various financial incentives to deterministically compute code and immutably store the results in a distributed ledger. Cryptographic truth enables blockchains to serve four general classes of trust-minimized functions:
- Database: Immutably store data and make it available to any user around the world; e.g. tracking the current state of business processes.
- Ledger: Immutably keep track of changes over time so that anyone can verify the history of certain processes; e.g., changes in asset ownership or the code underpinning applications.
- Compute: Execute application logic (i.e. smart contracts) in a tamper-proof and hyper-reliable manner; e.g., transferring money or settling a parametric contract.
- Validate: Verify the correctness of actions performed off-chain; e.g., checking the validity of off-chain computation executed by oracles or layer-2 rollups.
Blockchains can be relied upon to perform such functions because they are operated by a decentralized network of nodes that maintain a transparent distributed ledger using open-source software and built-in rewards/penalties to incentivize honest behavior. However, blockchains can only form consensus around actions that are verifiable using data already created by or stored in the blockchain’s ledger. For example, a blockchain uses ledger account balances and public/private key cryptography to verify token transfers.
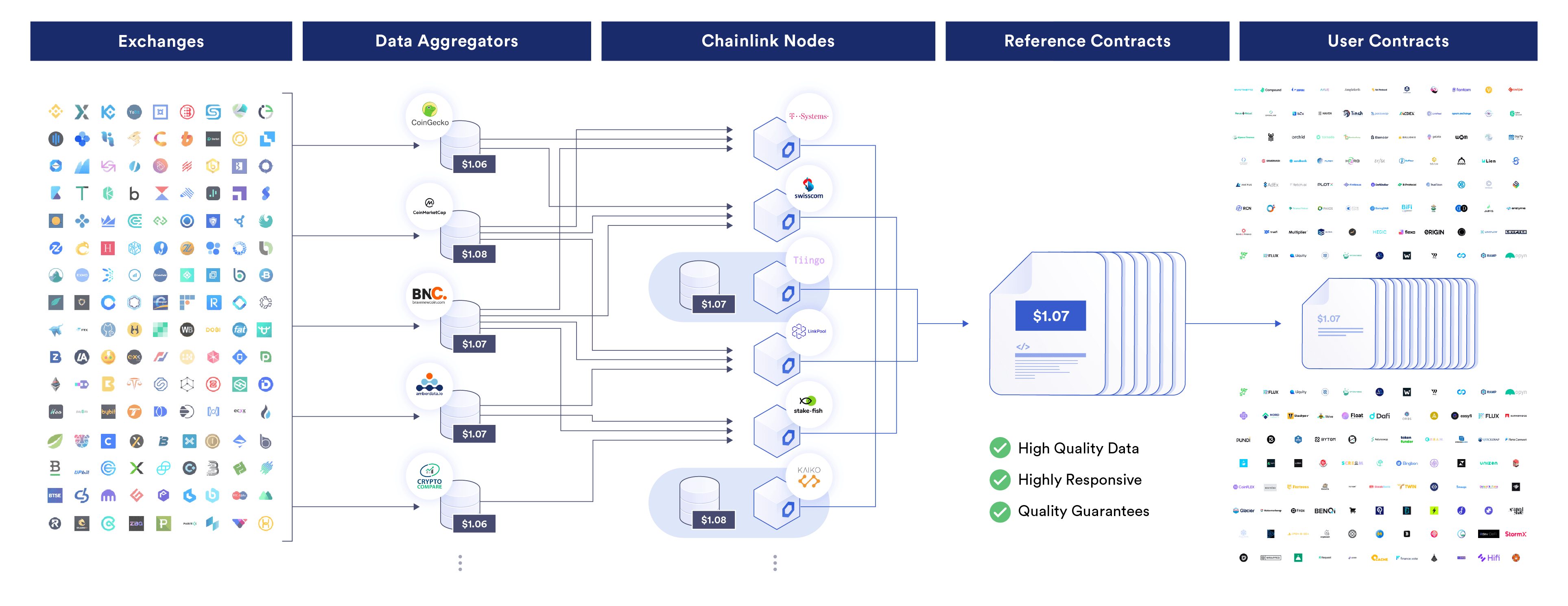
Oracles are entities that form consensus regarding external data and events using decentralized off-chain computation. Oracle computation is then verified to have been executed correctly by blockchain consensus. For example, Chainlink Price Feeds is a decentralized oracle service that delivers aggregated financial market data to blockchains. Blockchains are used to verify that a sufficient number of specific oracle nodes have submitted a price (i.e. 21 out of 31) by checking each oracle’s signature and automatically taking a median price—ensuring each valid oracle update has a sufficient level of decentralization, Sybil resistance, and the correct aggregation methodology.
Furthermore, Chainlink VRF is an oracle service that generates verifiable randomness and delivers it to blockchains. The blockchain is used to check a cryptographic proof submitted by the oracle prior to acceptance of the random number, which proves that the random number was generated in a tamper-proof and unpredictable manner based on a given seed value and the oracle’s private key. The result of these oracle services is decentralized finance (DeFi) applications being able to automate sound actions based on current market prices and NFT projects and blockchain gaming apps being able to support provably fair randomness in NFT mints and in-game mechanics.
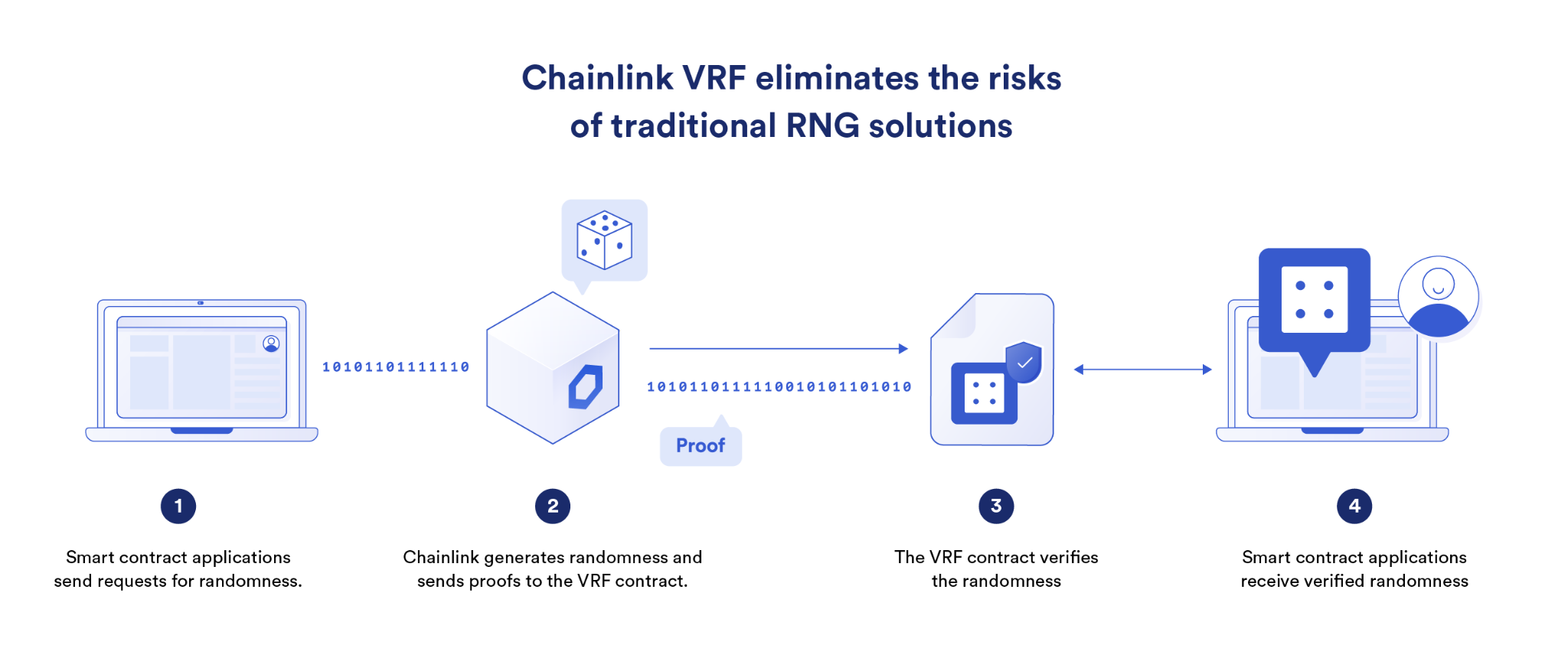
Combining the on-chain consensus of blockchains with the off-chain consensus of decentralized oracle networks (DONs), cryptographic truth can be leveraged within a wide variety of Web2 and Web3 applications to generate a complex array of trust-minimized applications and services.
How to Use Cryptographic Truth To Build Trust-Minimized Applications and Services
Cryptographic truth can be leveraged by applications to provide their users with more objective guarantees, ultimately moving them further toward the trustless end of the spectrum. Below are just a few of the many ways to trust-minimize an application:
- Transparent ledger: Make all account balances in the financial ecosystem transparent for anyone to view, empowering anyone to calculate objective financial metrics and determine the systemic risk that exists between applications.
Decentralized Finance (DeFi) is a parallel financial system built on blockchains where users can know objective metrics such as the total value locked (TVL), the liquidity of individual applications, large token transfers, and dependencies between on-chain protocols.
- Open-source code: Set the code underpinning software logic as open-source, enabling users to verify how the application actually works on the backend.
Smart contracts deployed on public blockchains can be audited by anyone, and are often paired with bug bounties to further harden application code via a collaborative feedback process.
- Tamper-proof applications: Tamper-proof the execution of application logic, removing the potential for arbitrary censorship, unfair influence, or unilateral actions that go against the pre-agreed-upon terms and conditions.
Etherisc, Acre Africa, and Chainlink collaborated to launch a parametric weather insurance application on the Ethereum blockchain that helped 17,000 Kenyan farmers hedge against the harmful effects of climate change by automating insurance payouts due to low rainfall during the growing season.
- Trust-minimized data feed: Reduce the ability of any entity to manipulate data or turn off a data feed, creating unstoppable and decentralized data feeds that don’t rely upon a single source of truth or single entity to maintain them.
Chainlink Price Feeds are decentralized oracle networks (DONs) that aggregate price data from across cryptocurrency and traditional markets to generate a single trust-minimized price used to settle financial applications across lending, derivatives, foreign exchange, and more.
- Decentralized money: Create a monetary policy that is set and issued based on a decentralized protocol as opposed to a central bank, as well as transactive in a censorship-resistant manner.
Bitcoin is a new form of blockchain-based money that has its own payment network, predefined issuance schedule, and a capped supply of 21 million Bitcoin tokens, which is made highly resistant to influence or censorship by a central administrator or small group of actors.
- Decentralized governance: Upgrade the code underpinning applications or manage the operations of an application using a consensus of tokenholders and/or other key ecosystem participants, reducing centralized decision-making processes.
Aave is a decentralized money market protocol that uses a decentralized autonomous organization (DAO) made up of AAVE token holders who decide as a group on parameter changes to its money markets and whether or not new software upgrades should be implemented.
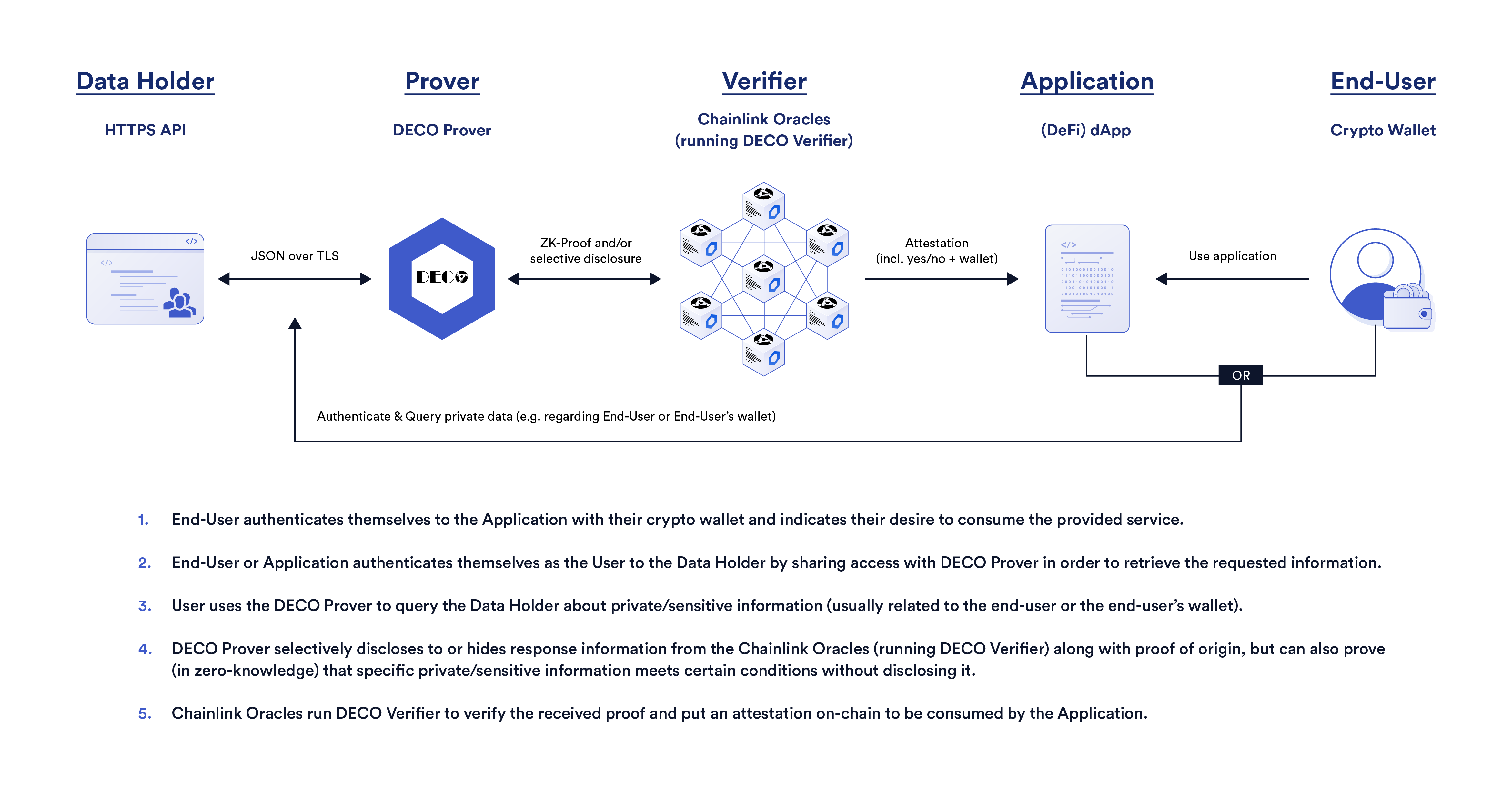
- Decentralized identity (DID): Prove statements about yourself to a third party without exposing your personal information or at least limit how a third party can reshare it, lessening the impact of data breaches and preventing opaque usage of consumer data by putting it back in the users’ hands.
Chainlink DECO can enable users to prove statements to applications without giving their personal information to it. For example, they can prove that they live in a certain jurisdiction without revealing their address to the application.
Trust-Minimization: A Growing, Inevitable Force in Society
While the innovation and adoption of Web3 may not always align with projections, the underlying concept of trust-minimized applications and services powered by cryptographic truth is sound and is already gaining traction. We all know society has a trust problem, and now we have the technology to actually do something impactful to solve it. It’s up to users, developers, entrepreneurs, and forward-looking companies to start building and adopting trust-minimized protocols and products with real long-term viability.
This is the competitive landscape of the future and the battle is already underway. Ignoring it will only empower your competitors, who will eventually use trust-minimization to their advantage by showcasing the superiority of the guarantees they provide to users. Are users really going to choose a trusted-only product over a trusted trust-minimized product when both have a similar cost and user experience yet the latter offers the user more guarantees that it’s as truthful as advertised? Truth is ultimately more reliable than trust, so there will be no backtracking once society gets a taste of applications and services that are trust-minimized yet still competitive across all other metrics. The time to build a world powered by truth is now.
To learn more about Chainlink, visit the Chainlink website and follow the official Chainlink Twitter to keep up with the latest Chainlink news and announcements.
