Zero-Knowledge Proofs (ZKP)
What Is a Zero-Knowledge Proof?
While the inherent transparency of blockchains provides an advantage in many situations, there are also a number of smart contract use cases that require privacy due to various business or legal reasons, such as using proprietary data as inputs to trigger a smart contract’s execution. An increasingly common way privacy is achieved on public blockchain networks is through zero-knowledge proofs (ZKPs)—a method for one party to cryptographically prove to another that they possess knowledge about a piece of information without revealing the actual underlying information. In the context of blockchain networks, the only information revealed on-chain by a ZKP is that some piece of hidden information is valid and known by the prover with a high degree of certainty.
In this article, we explore how zero-knowledge proofs work to provide privacy guarantees, the core benefits they offer to users, and an array of blockchain use cases that leverage ZKPs. In addition, we showcase how Chainlink’s DECO technology allows for the creation of privacy-preserving oracle networks that can prove data came from a specific web server in a confidential and backwards compatible manner.
@chainlinkofficial Zero-knowledge proofs (ZKPs) are a method for one party to cryptographically prove to another that they possess knowledge about a piece of information without revealing the actual underlying information. #web3 #crypto #blockchain #Chainlink
Zero Knowledge vs. Zero Trust
“Zero knowledge” refers to the specific cryptographic method of zero-knowledge proofs, while “zero trust” is a general cyber security model used by organizations to protect their data, premises, and other resources.
The zero-trust framework assumes that every person and device, both internal and external to the network, could be a threat due to malicious behavior or simple incompetence. To mitigate threats, zero-trust systems require users and devices to be authenticated, authorized, and continuously validated before access to resources is granted.
Zero-knowledge proofs can be used as part of a zero-trust framework. For example, zero-knowledge authentication solutions can allow employees to access their organization’s network, without having to reveal personal details.
How Do Zero-Knowledge Proofs Work
At a high level, a zero-knowledge proof works by having the verifier ask the prover to perform a series of actions that can only be performed accurately if the prover knows the underlying information. If the prover is only guessing as to the result of these actions, then they will eventually be proven wrong by the verifier’s test with a high degree of probability.
Zero-knowledge proofs were first described in a 1985 MIT paper from Shafi Goldwasser and Silvio Micali called “The Knowledge Complexity of Interactive Proof-Systems”. In this paper, the authors demonstrate that it is possible for a prover to convince a verifier that a specific statement about a data point is true without disclosing any additional information about the data. ZKPs can either be interactive—where a prover convinces a specific verifier but needs to repeat this process for each individual verifier—or non-interactive—where a prover generates a proof that can be verified by anyone using the same proof.
The three fundamental characteristics that define a ZKP include:
- Completeness: If a statement is true, then an honest verifier can be convinced by an honest prover that they possess knowledge about the correct input.
- Soundness: If a statement is false, then no dishonest prover can unilaterally convince an honest verifier that they possess knowledge about the correct input.
- Zero-knowledge: If the state is true, then the verifier learns nothing more from the prover other than the statement is true.
Zero-Knowledge Proof Example
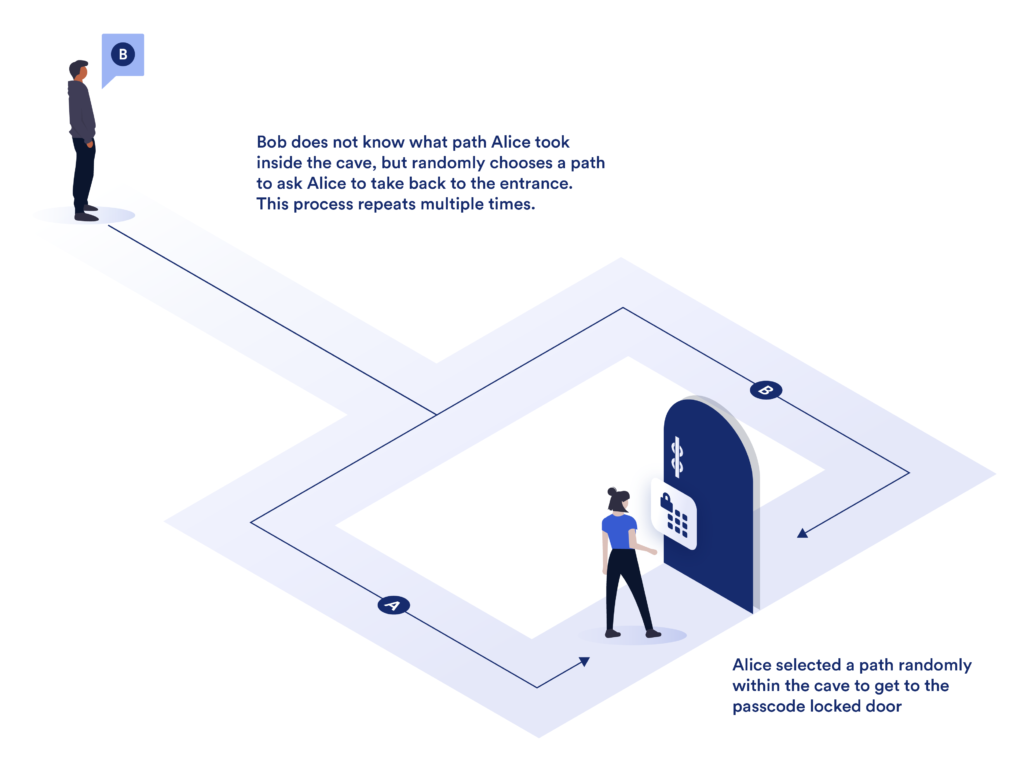
A conceptual example to intuitively understand proving data in zero-knowledge is to imagine a cave with a single entrance but two pathways (path A and B) that connect at a common door locked by a passphrase. Alice wants to prove to Bob she knows the passcode to the door but without revealing the code to Bob. To do this, Bob stands outside of the cave and Alice walks inside the cave taking one of the two paths (without Bob knowing which path was taken). Bob then asks Alice to take one of the two paths back to the entrance of the cave (chosen at random). If Alice originally chose to take path A to the door, but then Bob asks her to take path B back, the only way to complete the puzzle is for Alice to have knowledge of the passcode for the locked door. This process can be repeated multiple times to prove Alice has knowledge of the door’s passcode and did not happen to choose the right path to take initially with a high degree of probability.
After this process is completed, Bob has a high degree of confidence that Alice knows the door’s passcode without revealing the passcode to Bob. While only a conceptual example, ZKPs deploy this same strategy but using cryptography to prove knowledge about a data point without revealing the data point. With this cave example, there is an input, a path, and an output. In computing there are similar systems, circuits, which take some input, pass the input signal through a path of electrical gates and generate an output. Zero-knowledge proofs leverage circuits like these to prove statements.
Imagine a computational circuit that outputs a value on a curve, for a given input. If a user is able to consistently provide the correct answer to a point on the curve, one can be assured the user possesses some knowledge about the curve since it becomes increasingly improbable to guess the correct answer with each successive challenge round. One can think of the circuit like the path that Alice walks in the cave, if she is able to traverse the circuit with her input, she proves she holds some knowledge, the “passcode” to the circuit, with a high degree of probability. Being able to prove knowledge about a data point without revealing any additional information besides knowledge of data provides a number of key benefits, especially within the context of blockchain networks.
Types of Zero-Knowledge Proofs
There are various implementations of ZKPs, with each having its own trade-offs of proof size, prover time, verification time, and more. They include:
zk-SNARKs
SNARKs, which stands for “succinct non-interactive argument of knowledge”, are small in size and easy to verify. They generate a cryptographic proof using elliptical curves, which is more gas-efficient than the hashing function method used by STARKS.
zk-STARKs
STARK stands for “scalable transparent argument of knowledge”. STARK-based proofs require minimal interaction between the prover and the verifier, making them much faster than SNARKs.
PLONK
Standing for “permutations over Lagrange-bases for oecumenical noninteractive arguments of knowledge,” PLONKs use a universal trusted setup that can be used with any program and can include a large number of participants.
Bulletproofs
Bulletproofs are short non-interactive zero-knowledge proofs that require no trusted setup. They are designed to enable private transactions for cryptocurrencies.
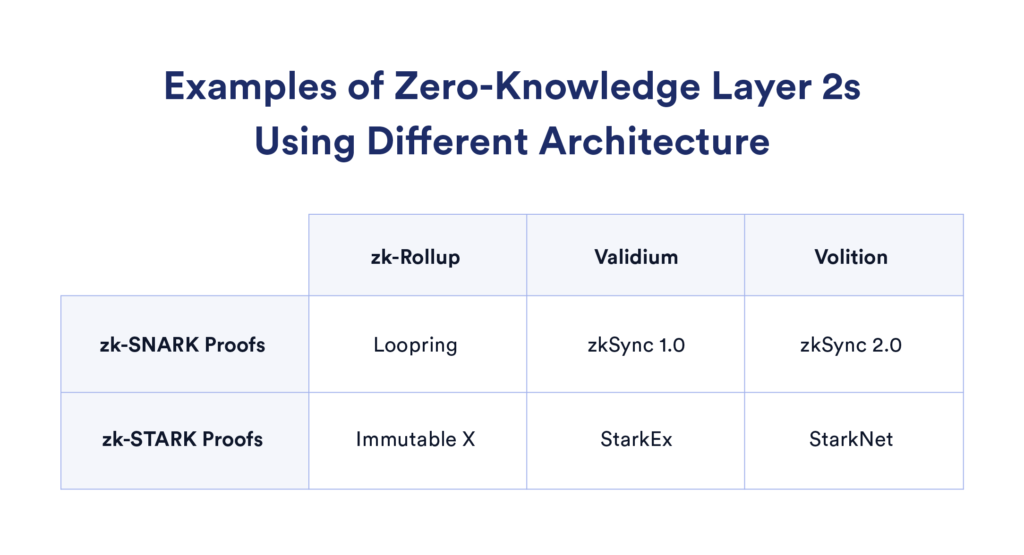
There are already a number of zero-knowledge projects using these technologies, including StarkNet, zkSync, and Loopring.
Benefits of Zero-Knowledge Proofs
The primary benefit of zero-knowledge proofs is the ability to leverage privacy-preserving datasets within transparent systems such as public blockchain networks like Ethereum. While blockchains are designed to be highly transparent, where anyone running their own blockchain node can see and download all data stored on the ledger, the addition of ZKP technology allows users and businesses alike to leverage their private datasets in the execution of smart contracts without revealing the underlying data.
Ensuring privacy within blockchain networks is crucial to traditional institutions such as supply chain companies, enterprises, and banks that want to interact with and launch smart contracts but need to keep their trade secrets confidential to stay competitive. Additionally, such institutions are often required by law to safeguard their client’s Personally Identifiable Information (PII) and comply with regulations such as the Europe Union’s General Data Protection Regulation (GDPR) and the United States’ Health Insurance Portability and Accountability Act (HIPAA).
While permissioned blockchain networks have emerged as a means of preserving transaction privacy for institutions from the public’s eye, ZKPs allows institutions to securely interact with public blockchain networks—which often benefit from a large network effect of users around the world—without giving up control of sensitive and proprietary datasets. As a result, ZKP technology is successfully opening up a wide range of institutional use cases for public blockchain networks that were previously inaccessible, incentivizing innovation and creating a more efficient global economy.
Zero-Knowledge Proof Use Cases
Zero-knowledge proofs unlock exciting use cases across Web3, enhancing security, protecting user privacy, and supporting scaling with layer 2s.
Private Transactions
ZKPs have been used by blockchains such as Zcash to allow users to create privacy-preserving transactions that keep the monetary amount, sender, and receiver addresses private.
Verifiable Computations
Decentralized oracle networks, which provide smart contracts with access to off-chain data and computation, can also leverage ZKPs to prove some fact about an off-chain data point, without revealing the underlying data on-chain.
Highly Scalable and Secure Layer 2s
Verifiable computations through methods such as zk-Rollups, Validiums, and Volitions enable highly secure and scalable layer 2s. Using layer 1s such as Ethereum as a settlement layer, they can provide dApps and users with faster and more efficient transactions.
Decentralized Identity and Authentication
ZKPs can underpin identity management systems that enable users to validate their identity, while protecting their personal information. For example, a ZKP-based identity solution could enable a person to verify that they’re a citizen of a country without having to provide their passport details.
Preserving Privacy With DECO
An implementation of a zero-knowledge proof-based oracle solution in development is DECO, a privacy-preserving oracle protocol within the Chainlink Network’s suite of secure off-chain computations. By extending HTTPS/TLS, the most common protocol used to transfer data over the Internet, DECO guarantees that data remains private and tamper-proof during its delivery from various private and premium data sources. DECO works with modern TLS versions, requires no trusted hardware, and operates in a backwards-compatible manner requiring no server-side modifications. As a result, DECO-enabled Chainlink oracle nodes can prove facts about data sourced from trusted servers without revealing the data on-chain, while also proving the source of the data since the TLS chain of custody is maintained.
With ZKPs like DECO, a wide range of smart contract use cases are made possible including undercollateralized loans, where borrowers generate high-assurance credentials attesting to their creditworthiness in a privacy-preserving manner. Specifically, borrowers can generate these credentials based on records from authoritative online sources, such as established institutions, without exposing potentially sensitive data such as their name, location, or exact credit score value (only that it exceeds a predefined threshold).
DECO can also be used to power the creation of decentralized identity (DID) protocols such as CanDID, where users can obtain and manage their own credentials, rather than relying on a centralized third party. Such credentials are signed by entities called issuers that can authoritatively associate claims with users such as citizenship, occupation, college degrees, and more. DECO allows any existing web server to become an issuer and provides key-sharing management to back up accounts, as well as a privacy-preserving form of Sybil resistance based on definitive unique identifiers such as Social Security Numbers (SSNs).
Lastly, ZKP solutions like DECO benefit not only the users, but also enable traditional institutions and data providers to monetize their proprietary and sensitive datasets in a confidential manner. Instead of posting the data directly on-chain, only attestations derived from ZKPs proving facts about the data need to be published. This opens up new markets for data providers, who can monetize existing datasets and increase their revenue while ensuring zero data leakage. When combined with Chainlink Mixicles, privacy is extended beyond the input data executing an agreement to also include the terms of the agreement itself.
Conclusion
By combining the inherently transparent nature of blockchain networks with the privacy-preserving design of zero-knowledge proofs, enterprises and institutions can benefit from the best of both worlds: They can keep their internal datasets private while still leveraging them in the reliable execution environments of smart contract applications.
Read the Chainlink 2.0 Whitepaper for a deeper dive into the role of decentralized oracle networks in confidentiality-preserving smart contract systems and sign up for the official Chainlink newsletter for the latest updates about the Chainlink Network.
