Unlocking Web3 Identity: Blockchains, Credentials, and Oracles
The first wave of Web3 innovation has primarily focused on representing something of value as a blockchain-based token (i.e. tokenization) and using tokens in smart contract applications (i.e. dApps). The result is an ever-increasing amount of utility, governance, and asset-backed tokens, along with dApps to use, exchange, lend, and earn tokens based on various business and social interactions.
Web3 offers many benefits to society, such as lowering the barrier to capital creation, increasing the transparency and cryptographic guarantees of applications, and providing people with permissionless access to financial services. However, despite its success, Web3 is in danger of becoming hyper-financialized—a state where those with the most money yield an extraordinary amount of influence over the ecosystem’s development, governance, mindshare, and other key elements. In its current state, Web3 is also limited to use cases in which users don’t need to know anything about one another beyond their on-chain address.
To unlock a plethora of new use cases, Web3 needs a tech stack that enables interactions based on end users’ financial and social capital. With this in place, on-chain relationships could be expanded beyond intermediated exchange—personal connections, culture, reputation, identity, and trust could facilitate interactions between people.
Incorporating social capital into Web3 requires an on-chain identity layer that can be used to extend on-chain addresses beyond just account balances to also include unique character traits, social affiliations, historical reputations, and more. Combining these identity-based elements can enable Web3 users to have “souls,” as articulated by authors E. Glen Weyl, Puja Ohlhaver, and Vitalik Buterin in their research paper Decentralized Society: Finding Web3’s Soul.
The following blog will explore Web3 identity in a broad sense, focusing on how blockchains, credentials, and oracles can combine to create a feature-rich on-chain identity layer that satisfies a variety of use case requirements and user trust assumptions.
Why Web3 Needs an Identity Layer
Web3 is centered around generating trust-minimization—a near guarantee that an interaction will happen exactly as understood by its participants. Trust-minimization is why blockchains use decentralization, financial incentives, and cryptography to generate strong assurances for users that their computations will be correct, timely, censorship-resistant, and tamperproof. This blockchain-based method of executing code and storing data in a trust-minimized manner can be referred to as cryptographic truth.
Cryptographic truth is largely created through game theory—the ability to incentivize rational actions by the majority of nodes in a decentralized network using rewards to incentivize desired behavior and penalties to disincentivize undesired behavior. For example, most blockchain game theory assumes that if a network is transparent, sufficiently decentralized, and properly incentivized, an attack is highly unlikely to succeed given that the attacker has to pre-commit financial resources to mount an attack (e.g. computing resources in proof-of-work networks and financial stake in proof-of-stake networks), which are likely to be wasted/confiscated as a result of their malicious action. The end goal of this game-theoretical design is enabling deterministic software—i.e., x input will always lead to y output.
The problem is that designing frameworks to facilitate social or economic interactions for end users is not always as simple as creating a set of financial incentives. For starters, generating trust minimization in certain use cases might require putting in place penalties for undesired behavior that are too stringent for users compared to the potential rewards they may earn from the application—what if an accident or misunderstanding happens that results in a penalty? There are also a wide variety of interactions that users want to engage in without the influence of financial factors, or at least without the risk of large amounts of capital being able to easily co-opt the interaction (e.g. governance, public goods, and social clubs).
Web3 protocols may also face challenges with legal compliance, the verification of off-chain actions, or the settlement of disputes—particularly when users are pseudonymous entities. While pseudonymity is a desired feature for certain use cases (e.g. it enables censorship resistance), many other use cases can’t exist without knowing certain personal information about end users.
These problems point to the need for an on-chain identity layer for Web3 that can be used to prove social dynamics and make privacy-preserving identity assertions to blockchain-based applications, such as historical reputation, KYC/AML, personality, and various other human elements while still preserving some or all of the blockchain’s trust-minimized guarantees. Identity solutions enable users and applications to know who users are beyond their address’ account balance and transaction history, fostering on-chain interactions based on various types of social capital.
For example, a money market could offer lower lending rates to users with a good credit history, a DAO could bootstrap its membership with users that show solidarity for a specific cause, or an enterprise could perform KYC/KYB on a counterparty prior to engaging in a business relationship. Ultimately, the addition of an identity layer will open up a whole crop of applications not currently possible with the existing Web3 tech stack.
The Technology Behind Web3 Identity Solutions
In order to better understand identity, let’s first classify three general types:
- Official identity—official qualifications, achievements, or facts about a person’s background that are legally recognized in a specific jurisdiction.
- Social identity—unofficial attributes, achievements, or statements about a person based on attestations from others.
- Self identity—attributes, achievements, or statements one makes about oneself.
How these types of identities are used in Web3 will depend upon the particular beliefs and business needs of a developer, user, or decentralized community. For instance, enterprises are likely to prefer official identities that retain privacy given that’s how their existing processes function. However, some Web3-native applications may prefer a transparent social identity solution where the consensus of a decentralized community can attest to information about on-chain users. Each type of identity has its own strengths and weaknesses that need to be considered before implementation.
Identity solutions for Web3 are underpinned by three general primitives that can be used in isolation or mixed and matched to serve different needs.
Blockchains: Identity Database
Blockchains are public databases where users could technically store data immutably and make it accessible to anyone in the world and easily reusable across applications. However, storing raw personally identifiable information (PII) on public blockchains comes with serious privacy concerns given their public and transparent nature.
Fortunately, there are a few alternatives for accessing identity-related data and assertions on a blockchain while preserving privacy. A user could store on a blockchain the hash of PII data that resides in an off-chain database, or tokenize PII data or claims about it as tokens on a blockchain. Alternatively, external entities (i.e. oracles) can verify off-chain identity information about users, and then post an attestation about the information on-chain for smart contracts to reference during execution (i.e. a yes or no attestation of the claim that Alice > 21 years old).
Credentials: Identity Data and Attestations
Credentials are claims about a person’s qualifications, achievements, personal qualities, or really any aspect of a person’s background. Identity solutions use credentials to verify that someone is qualified to perform some specific action, such as a driver’s license giving someone the right to operate an automobile or a work certification proving someone is qualified to work in a specific industry.
Since Web3 is inherently about facilitating digital relationships, the ability to access digital credentials is necessary for building Web3 identity solutions. Two of the most common features in Web3 identity are verifiable credentials (VCs) and decentralized identifiers (DID). VCs are tamper-proof statements about a user that are cryptographically signed by the issuer. A verifier can then authenticate the credential through DIDs, such as by using public/private key pairs on blockchains to verify that the hashed credential belongs to the specific user.
There are also ways of tokenizing identity data or attestations. For instance, Soulbound tokens (SBTs) are non-transferable non-fungible tokens (NFTs) that represent commitments, credentials, memberships, affiliations, or statements about their owner. SBTs can be issued to a user by other users or by an institution, or a user can issue an SBT to themselves. SBTs may represent all kinds of information, such as a diploma issued by a university or a statement the user wants to be held publicly accountable to. While the non-transferable nature of SBTs makes them highly reliable as unique identifiers to an on-chain address, they are inherently transparent, making them difficult to use when privacy is required. POAPs are another type of tokenized identity solution, where organizers of an event issue NFTs to attendees as a kind of proof of attendance.
The combination of tokenized and non-tokenized credentials that remain within the control of users generally refer to the design space of decentralized identity or self-sovereign identity (SSI). The idea is that users own and manage their credentials and can share them with applications how and when they desire.
Oracles: Attestors and Relayers of Credentials
Oracles are entities that relay and attest to data about a user’s identity on-chain that was originally stored or generated off-chain. Oracles can be used to relay raw data directly from an off-chain API or between disparate blockchains. Oracles can also compute upon raw data before posting it on-chain or triggering the creation of a token mapped to certain PII data stored off-chain.
One of the most exciting use cases is for an oracle to witness a user pulling information about themselves, such as a diploma from a university or legal credentials from a government site, and attest to the provenance of that information. Users do not need to expose their private information to oracles either; they can prove the interaction through zero-knowledge claims. Essentially, this allows oracles to attest to the validity of users’ real-world identity information while still ensuring it remains private.
Web3 Identity Solutions Empower New Use Cases
Below are seven distinct on-chain identity solutions that unlock new use cases across Web3. The solutions make use of on-chain data, credentials, and/or oracles to verify specific elements of a user’s identity needed to facilitate specific types of economic or social interactions.
Proof of Legal Identity—You Are x Person
Identity information such as legal name, date of birth, and area of residence is especially important when companies or projects need to abide by certain jurisdictional requirements or want to follow up with a user after a dispute or breach of contract.
There are a few ways to prove someone’s legal identity. One way is for an official credential issuer (e.g. a government or bank) to issue a verifiable credential. The problem, however, is that most credential issuers don’t currently have an interest in creating new processes around issuing VCs or are ready to make the technology investment to change their current IT systems.
A more practical approach is to use DECO—a privacy-preserving oracle protocol currently under development that leverages zero-knowledge proof technology to enable users to prove statements about themselves to applications without revealing that information to the public or even the oracle itself. DECO is able to connect to existing APIs, even when they require end-user authentication, and does not require any change by the API data provider.
Burrata participated in a DECO proof of concept with Chainlink to enable Web3 users to prove their Web2 identity to applications using off-chain API data providers within the Burrata partnership system. With the support of DECO, the proof of concept demonstrated that Burrata can be connected to an identity platform and a document signing service without any private data revealed on-chain, to the application, or to the oracle—only the privacy-preserving claims about them. At SmartCon 2022, Burrata demonstrated a prototype through a cabin rental proof of concept where users could rent a cottage if they verified their identity and signed a temporary rental agreement.
Proof of Social Identity—You Own x Online Account
Many applications may want to leverage existing social identities (e.g. Facebook, Twitter) within Web3-related services. Thus, it can be important for security reasons for the user to authenticate his/her social identity that controls a specific web3 address prior to other users interacting with them.
PhotoChromic is a project that successfully completed a proof of concept using DECO to prove the authentic relationship between a verified Web3 individual and their particular Twitter or Discord social handle without exposing the underlying PII. Photochromic effectively creates a bridge between a user’s Web2 and Web3 identities, enabling the user to enrich their wallet with social attributes—an added factor of authentication and portability for their identity, represented as an NFT. This ultimately consolidates a user’s on-chain and off-chain identity and enables applications to remove the friction of repeated KYC onboarding. Applications would only need to provide utility and token-gated access to select users based on certain criteria without needing to know their real-world identity or even their exact social media handle.
Proof of Creation—You Created x
Many use cases don’t need KYC but do require a method of proving provenance, whether of a statement or a work of art. By being able to tie words or objects back to the initial creator, users can prove the authenticity of their art or luxury goods or verify if videos and statements that people claim someone made are in fact true.
One way to develop a proof-of-creation mechanism would be by issuing SBTs. As outlined in the aforementioned research paper Decentralized Society: Finding Web3’s Soul, an artist could issue an NFT from their Soul (address), allowing people to verify it came from a specific artist. An artist may also issue a statement as a linked SBT stored in their Soul to attest to the NFT’s membership of a collection, as well as to vouch for a scarcity limit. Furthermore, photographers could issue SBT-based photos and videos from their Souls to avoid deep fakes while social commentators could make statement-based SBTs about finance, politics, and other hot-button issues as a way to build a reputation based on their historical track record of accuracy and ethics.
These concepts roughly play into the notion of a Ledger of Record—a concept articulated by Balaji Srinivasan. A Ledger of Record would use a decentralized protocol to cryptographically sign data feeds on-chain, encompassing social media feeds, data APIs, event streams, newsletters, RSS feeds, and more. The Ledger of Record concept is designed to act as a single source of truth regarding the source of official information.
Proof of Funds—You Have x Amount of Money
Another area of importance is proving someone has a certain amount of assets that can’t be accounted for on the blockchain itself because they’re stored off-chain or on a different blockchain. Proof of funds is important for calculating risk during financial interactions, as the more funds a user has, the more reliable they generally are as a counterparty.
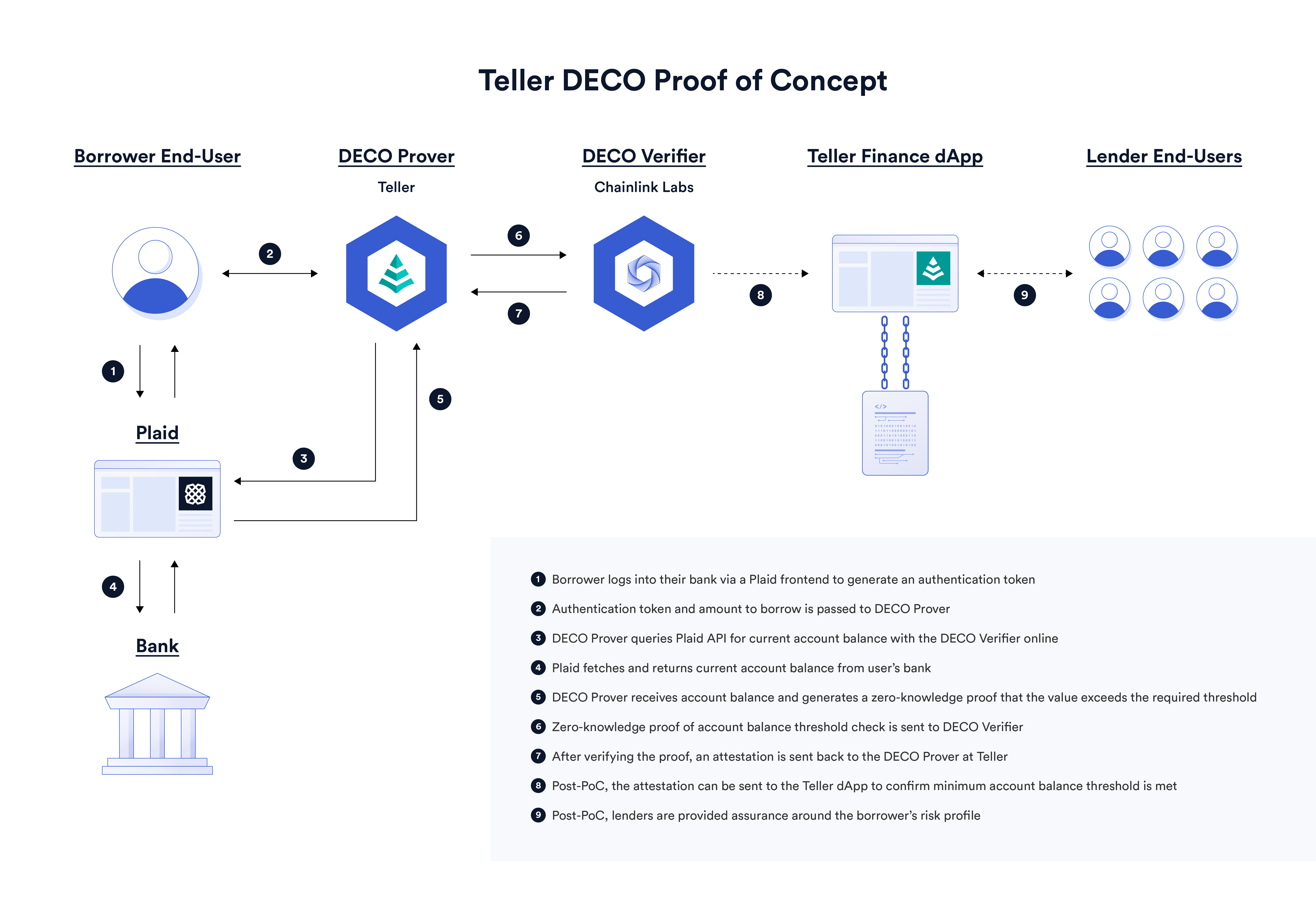
Teller is a DeFi protocol marketplace for digital asset lending that supports undercollateralized loans. Teller used the DECO protocol in a proof of concept to prove that the sum of a user’s off-chain bank accounts had a balance exceeding a dynamic threshold specified by the requested loan amount. If the sum of a user’s account balances exceeds the threshold, then their risk profile as a borrower would be reduced, allowing for significantly lower collateral requirements for loans. For example, if a borrower requested a loan of \$5,000, then the user would have to prove that they held at least \$5,000 in their bank account as a testament to their ability to repay the loan.
To learn more, check out How DECO Enables Undercollateralized DeFi Lending: A Proof of Concept With Teller.
Proof of Social Reputation—You Have a Social Reputation of x
An emerging area of identity is social reputation—using a decentralized community to attest to certain actions or characteristics of an individual, to give one example. Social reputation is also extractable from a user’s on-chain transaction history or their collection of SBTs.
For instance, a lending protocol could lower a user’s collateral requirements because their on-chain transaction history shows a track record of paying back loans. Weyl, Ohlhaver, and Buterin point out in their research paper how this could take the form of a user staking an SBT (i.e. reputation) to secure a better loan. Once repaid, the SBT could be burned or replaced with a new SBT representing proof of payment. If not repaid, an SBT could be automatically issued to signal the user’s loan default—akin to a negative review. It’s worth noting though that the permissionless issuance of SBTs can be problematic in the scope of negative reviews, as it can lead to doxxing, bullying, and censorship risks.
The paper also discusses how social reputation from SBTs can play a role in bootstrapping a Web3 community, particularly through issuing tokens to Souls with certain characteristics. For instance, a DAO that wants to attract a strong developer community could airdrop tokens to developers who hold three out of the last five conference attendance SBTs or hold other tokens reflecting attendance, like POAPs. Airdrops could also be weighted based on a particular combination of SBTs, such as a non-profit for planting trees issuing governance tokens to Souls who hold a mix of environmental action SBTs, gardening SBTs, and carbon sequestration tokens.
Proof of Personhood—You Are x
There are many applications that could be greatly enhanced by knowing just one fact about a user—are they a real (i.e. not a robot) and unique (i.e. can’t be duplicated) human being? A non-transferable and non-reusable proof of personhood is a powerful tool in building a variety of applications so long as it can conceal users’ personal information. For instance, social media platforms could use proof of personhood to eliminate bots from spamming users with unwanted information or malicious links, as well as prevent inauthentic social consensus due to the creation of Sybil accounts.
DAOs could leverage proof of personhood as a form of Sybil resistance to prevent one user from gaining large amounts of power due to owning many separate accounts. One way to potentially do this is by performing computation on a Soul’s collection of SBTs, with a certain number of reputable SBTs—particularly if issued by a diverse set of institutions/Souls—increasing the likelihood that the person is real and not a bot. However, Sybil resistance is a notoriously challenging design space since validating the uniqueness of a single person’s credentials requires a database to reference for duplicates.
Proof of Interaction—You Interacted With x
A variety of further use cases become possible when applications can prove users interacted with something in a specific way. Proof of interaction is especially valuable in marketing campaigns, with users incentivized to take specific actions to earn rewards. Certain interactions may even trigger the issuance of SBTs, such as earning social good SBTs for donating to a charitable cause or performing community service. These triggers could also be used for recurring actions, such as triggering airdrops per interaction for a generalized x-to-earn model.
Clique used DECO in a proof of concept to demonstrate a proof-of-fandom solution, which enables users to prove that they had interacted with a particular artist or creator’s tweet or that they were following a particular content creator on Twitter—all without revealing their own Twitter handle to the application to preserve their privacy. This serves as proof that they’re a fan of a particular creator, earning the user various crypto/NFT rewards, reputation, or privileges. In addition to this, Clique was also able to achieve higher quality data through the use of DECO, helping ensure the authenticity of users’ followers and impressions generated.
The Next Evolution of Web3
Identity is undoubtedly a critical element in the expansion of Web3 applications and services. There will, of course, be challenges with implementing identity on blockchains, whether it’s protecting user privacy, preventing cheating and gatekeeping during credential issuance, or balancing the desire for immutability with the ability for people to improve their standing. Despite these challenges, Web3 identity offers unprecedented value to users as it allows applications to know details about them, but only those the user wants to make accessible. It even allows users to prove details about themselves without ever divulging the information itself, as seen through the power of the DECO technology.
It’s through these innovations that social capital can become an integral part of on-chain interactions, helping prevent Web3 from becoming hyper-financialized, as well as enabling a wide variety of new use cases and onboarding new players into the space, such as enterprises and established institutions. Ultimately, identity solutions will enable the trust-minimization brought about by Web3 to become ingrained into our everyday lives, giving users better guarantees around the privacy, transparency, and ownership of their sensitive data.
