Definition: The verifiable web uses blockchain technology, decentralized computing, and cryptography to enforce contractual obligations, provide greater transparency into how systems work, and give users more control over their data, identities, and assets.
In early civilizations, truth was based on myth. Observations of worldly phenomena were wrapped in symbolic narratives, religious beliefs, and ancient wisdom. Over time, humanity began to value objective measurements and reasoning, birthing disciplines such as science, mathematics, and logic.
After the invention of the written word and, later, the printing press, books and documents captured the world’s information in written form, from academic literature and legal contracts to statistics and opinionated analysis. Then, in the twentieth century, phones, computers, and the Internet started a digital revolution in how information was created, distributed, and verified, with supercomputers now performing large-scale computations on complex data sets and billions of users across the globe generating, sharing, and talking about content every day in real-time.
Now, with a simple Internet connection, anyone in the world can instantly access a seemingly infinite flow of information. But while individuals are now empowered to consume and share more information than ever before, high-velocity, high-volume information scattered across a variety of applications poses extraordinary challenges: How can an everyday user make sense of such a vast, complex, and sometimes contradictory information landscape? Information warfare and advancements in AI are only compounding this problem.
Information is the basis for sound decision-making by humans, institutions, and systems, and we need a better foundation for obtaining and evaluating it. This new foundation starts by increasing people’s ability to verify the source of information, the method used to calculate it and the integrity of the systems used to do so, and the historical reputation of these sources, methods, and systems. Doing so will require the creation of a more advanced informational and digital age powered by cryptographic truth. We call this the verifiable web.

What Is the Verifiable Web?
The Web Is Flawed
In the established web model, the Internet is shared networking infrastructure that enables communication between computers via online applications. Each online application handles its own computing (executing code), storage (storing code and data used and produced), and management (updating code and maintaining a successful business) by either running it in-house or outsourcing it to a centralized company. Users of applications are then responsible for establishing a connection to the Internet in order to interact with the online application, generally by paying for a data or Internet plan.
The problem with this model is it directly or indirectly gives centralized entities— whether it’s the application or Internet Service Provider (ISP)—extensive control over online data, computing, and/or networking. This means how the application works can be arbitrarily changed at any time—a social media company quietly changing its algorithm, for example. It also means that user data and connectivity can be arbitrarily censored, omitted, or monetized for personal gain, oftentimes with little user oversight or awareness of how it’s being done. As a result, the user has to trust the application and Internet infrastructure to act in a reliable and honest manner because they have no actual guarantees—just paper promises that take time and money to fight against in court if broken (assuming the user even has access to a high-integrity legal system).
With the web extending far beyond information-sharing applications to span financial transactions, health management, election systems, supply chain tracking, and more, fixing it means fixing the nature of almost every digital interaction the modern user has. The stakes couldn’t be higher.
A Verification Layer for the Internet
The verifiable web is not a replacement for the established web but rather an extension of its capabilities. The verifiable web provides applications with a decentralized, cryptographically secure, and verifiably fair environment for running computations, storing data, governing operations, and facilitating networking across systems.
With some or all of an application’s backend infrastructure run on the verifiable web, users are able to obtain proof and guarantees about the application and its data, such as that it’s manipulation-resistant (secure), always available (reliable), permissionlessly accessible (censorship-resistant), logically sound (accurate), authenticated (genuine), private (privacy), and traceable from inception (provenance).
Instead of requiring users to trust that an online application will keep its commitments, the verifiable web provides technologically enforced guarantees that users can independently check.
By knowing how an application works and that it cannot arbitrarily change, users can make more informed decisions about whether or not to engage with it and whether to disengage at any point in the future. This is because the user is able to know its state at all times with near-complete certainty, including how it makes decisions, how rules are enforced, how data is generated, and what updates will be made.

The verifiable web is underpinned by game-theoretical design—using the science of strategy to produce desired outcomes. The verifiable web combines various technologies to create game-theoretical environments where rational participants are incentivized to produce fair outcomes (i.e., it’s deterministic), even in the presence of adversaries. Furthermore, users can inspect these environments to check if they meet their own standards of trust and fairness. In contrast, the established web relies on trust in probabilistic and unverifiable promises made by the centralized entity that owns the application or runs its backend infrastructure.
For example, central banks manage monetary policy based on subjective assessments while banks manage payment ledgers with relative opaqueness. While there are various reasons for doing so, it is a less predictable process that can create systemic risk. Alternatively, Bitcoin uses a game-theoretical design to incentivize a decentralized network of nodes to manage monetary policy and maintain a payment ledger according to a publicly available set of rules enshrined in the software that nodes on the network run. This provides users with verifiable proof about how the ledger is managed and how difficult it is to tamper with the ledger and alter the monetary policy, ultimately creating more predictable risk management.

Why Do We Need the Verifiable Web?
The verifiable web is what crypto is really about—it starts with fixing money and financial markets, before expanding into other industries to bring greater proof and transparency to the digital interactions that determine our lives. If trust in institutions continues to decrease, demand for technologies that provide verifiable proof about the world will only increase. Some of the areas of growing distrust that the verifiable web can help to improve include:
Financial Markets and Services
Financial markets have historically been subject to boom and bust cycles as a result of mispriced asset valuations and resulting systemic risk due to their cross-dependencies. People want better guarantees that financial markets and assets are as healthy as the official reports state, and that financial services will be honored as agreed upon. The verifiable web can be an important tool in providing a golden record across market infrastructure or forcing timely and in-full financial payments, ultimately creating more stability and reducing systemic risk.
Images and Videos
With the acceleration of AI, it’s becoming harder to distinguish between real and fake images and videos. The spread of fake content is leading to the proliferation of false narratives in society, and, as a side effect, increased skepticism in legitimate sources. The verifiable web can play a key role in authenticating the source of images and videos, such as a camera cryptographically signing a photo/video with a unique private key from an HSM hardware module and then hashing a copy onchain as a tamperproof record of who took the photo/video and when it was taken.
Information and Analysis
The acceleration of AI and information warfare has also made it hard to filter misinformation and disinformation and decide who to turn to for unbiased analysis. The verifiable web can not only help create a single, globally accessible source of truth about the origin of information, but it can also help establish methods for verifying the track record of news sources and analysts over time and incentivize sound research and analysis.
Food and Goods
As society has become more educated, it has also become more interested in the source and quality of food and goods. However, it can be difficult to verify the true origin of a good or that it’s authentic, hasn’t been diluted, and is backed by a manufacturer with a reliable track record. The verifiable web can help users track and rate food and goods from inception to the storefront with more certainty.
Contracts and Legal Systems
Having verifiable proof that a contract will be honored is critical to running a reliable business or purchasing a product (e.g., warranties). Unfortunately, contracts are not always strictly enforced, especially when one side has a clear economic and political advantage over their counterparty. The verifiable web can level the playing field by replacing clauses in digital contracts with technologically enforced guarantees via smart contracts and oracle networks. This can help improve trust between people, businesses, and institutions globally, particularly by making the levers that can dictate the outcome of contracts impossible for any party to tamper with.
Social Participation and Consensus
Obtaining a realistic view of what the public thinks helps institutions and society at large make better decisions. AI, bot farms, and closed-source algorithms make it hard to know whether social consensus derived from online debates, surveys, elections, viewership, and more is real or manipulated. Thus, it’s important for the verifiable web to bring authentication and verifiability to how social consensus is created and gathered, such as by open-sourcing algorithms used in information collection and leveraging manipulation-resistant and privacy-preserving verification systems to prove someone is a unique human without revealing their identity.
Technologies That Define How the Verifiable Web Works
Below is a list of technologies/technological movements that combine to create the verifiable web. New technologies are also likely to emerge as consumers demand more and more verifiable proof and guarantees about their everyday lives.
Open-Source Software
Open-source software is software for which the code that defines how it runs is verifiable by anyone. This allows stakeholders using or affected by the software to inspect it before deciding to adopt or update it. As more people independently verify it, the software becomes more secure and trusted to consistently operate in a specific way.
Examples: Linux Operating System, Mozilla Firefox, and Apache Web Server
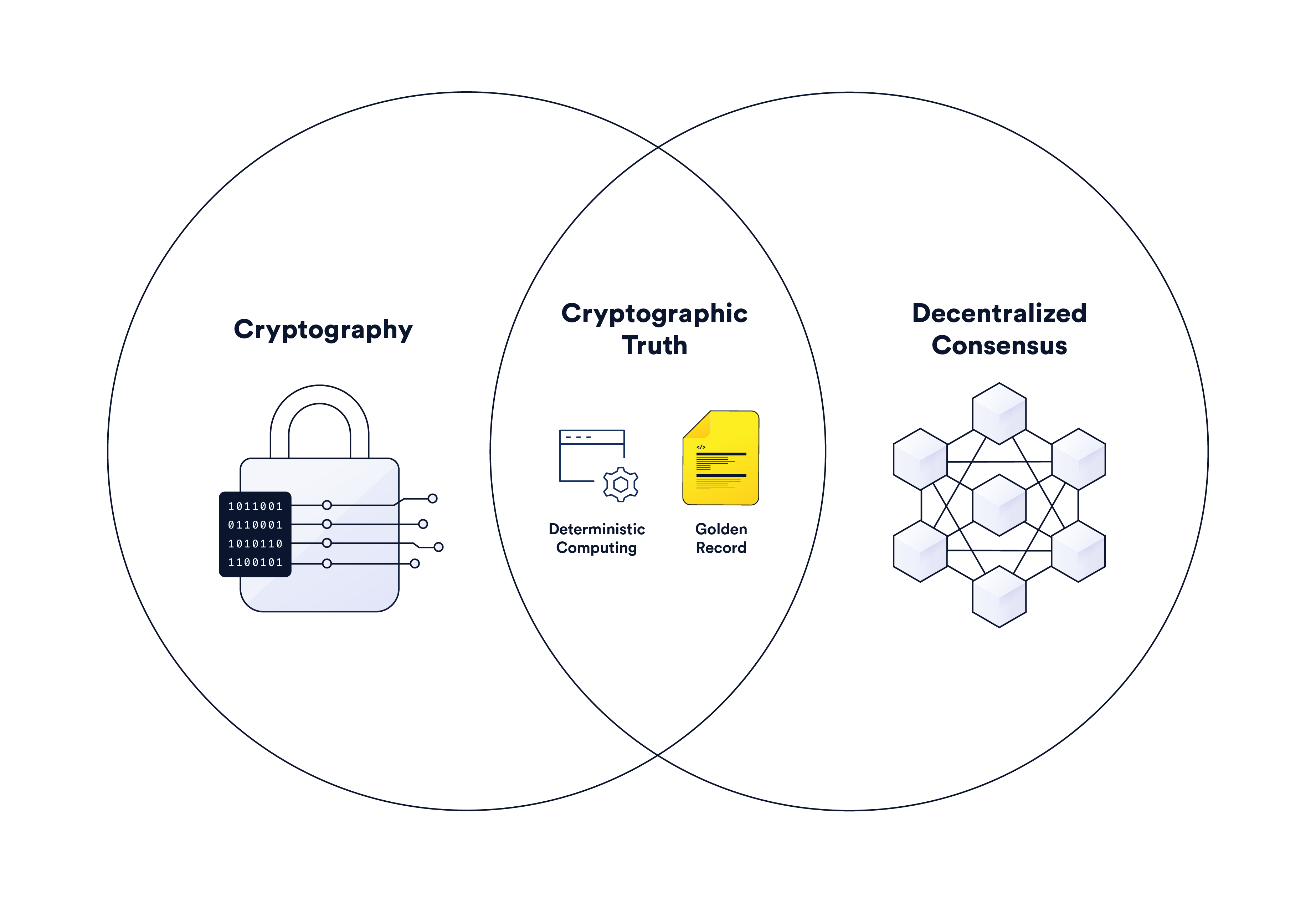
Cryptography
Cryptography involves the use of verifiable mathematical techniques to secure communication in the presence of adversarial behavior. In a general sense, cryptography is used to conceal and authenticate information by scrambling it with a cipher, which cannot be cracked in any practical sense (e.g., it would require a prohibitive amount of time and investment), even with the most advanced computing technologies. Cryptography is already widely used across the modern Internet to ensure that users are able to interact with each other without worrying about imposters or middlemen intercepting their communications.
Examples: One-Way Hash Functions, Public/Private Key Encryption, and Zero-Knowledge Proofs
Blockchains and Smart Contracts
Blockchains are distributed ledgers that provide verifiable proof that the tracking of asset ownership is accurate and tamperproof, and that the ability to move assets between users is permissionless and always available. Furthermore, the smart contract applications running on blockchains provide verifiable proof that their code will execute exactly as it is stored onchain. This enables businesses to transact and governance processes to be managed in a distributed manner that is transparent and resistant to manipulation by a single entity.
Blockchains make use of a multitude of technological primitives, most notably cryptography, consensus protocols, and financial incentives. As an overview, blockchains use financial rewards and penalties to incentivize a decentralized network of independent nodes to come to an honest consensus about the validity of submitted transactions and to keep the ledger updated and available. Blockchains also use cryptography to authenticate transactions, ensuring they are unique to a specific user. The combination of cryptography and decentralized consensus makes it very difficult to tamper with the network, resulting in a form of cryptographic truth.
Examples: Bitcoin, Aave, and ENS
Oracles
Oracles leverage similar primitives of cryptography, consensus protocols, and financial incentives, but for the purpose of creating cryptographic truth around any type of data, computation, or connection between systems. Whereas blockchains are only concerned with verifying the ownership and transfer of tokens or updating smart contracts, oracles can be applied to creating truth and guarantees about anything, such as calculating the fair price of an asset, generating a tamperproof and unbiased random number, or ensuring that an automated task will be completed at a specific time or that value will be securely transferred between systems when a specific event occurs. Oracles can expand cryptographic truth to the verification of almost anything.
Examples: Chainlink Data Streams, Functions, and Cross-Chain Interoperability Protocol (CCIP)
Trusted Hardware
Trusted hardware is hardware where the software running inside cannot be tampered with or even observed by either a third party or the hardware operator. Trusted execution environments (TEEs) often generate cryptographic attestations, which give users verifiable proof that the software running inside executed exactly as expected. Although the area still requires more research and development, trusted hardware is an extension of other types of hardware like secure enclaves and hardware security modules (HSMs), which provide a protected environment for storing information or executing code.
Examples: Intel SGX, ARM TrustZone, and Keystone
Biometrics
Authenticating that information came from a specific person or company is critical proof for facilitating certain processes. Biometrics provide a way of authenticating that an action was taken by a specific person by verifying a physical feature unique to them. For example, phones use a person’s fingerprint as verifiable proof that they belong to the owner.
Examples: Fingerprint, Iris Recognition, Facial Recognition
Reputation Systems
While truths or proofs may not always be obtainable in real-time, they can be demonstrated over time through the use of reputation systems. Reputation systems are methods of tracking the historical performance of an entity or process, such as a system’s uptime, the accuracy of a data provider, the correctness of an analyst’s predictions, or the reliability of a user in a help forum. The integrity of reputation systems is further verifiable when they cryptographically sign data that they’re tracking onchain, where it cannot be deleted or altered in the future.
Examples: eBay, Stack Exchange, and Ethereum Beacon Chain Validator Rankings
Artificial Intelligence
As machine learning algorithms and data collection techniques become more advanced, so too does the ability to analyze complex datasets and come to conclusions with a statistically high degree of confidence.
One example of this is a project in development by Green World called AIRS, which aims to use satellite remote sensing data with smart contracts to successfully reward stewards of targeted regenerative agriculture. Chainlink oracles are tasked with gathering ground-truthing and satellite data, analyzing it within trusted execution environments for high-trust quantitative metrics, and relaying it to a blockchain to trigger automated payments to stewards. AIRS rewards to stakeholders can take the form of cryptocurrency—readily convertible into local currency—or digital financial instruments tailored to meet the needs of local communities.
A Trust Anchor for Society
The verifiable web is a much-needed trust anchor for society, whereby vulnerable human decision-making is replaced by unbiased software that enforces honest outcomes and provides verifiable proof of how it arrived at such outcomes. This new superpower enables builders to create applications that are undeniably fair, provably accessible to anyone in the world, and verifiably secure against manipulation. The possibilities are endless, and this paradigm shift couldn’t come at a more pressing time, with society needing verifiable truth about how the world works more than ever.
Chainlink is the decentralized computing platform helping power the verifiable web. From startups to leading financial institutions, builders worldwide use Chainlink to power verifiable applications and high-integrity markets. Learn more by visiting https://chain.link/.
