Chainlink DECO Sandbox Is Now Publicly Accessible: Unlocking Privacy Innovation in Onchain Finance
We are excited to announce that the Chainlink DECO Sandbox has been opened to the public, providing access to DECO, the foundational zkTLS-oracle technology for authenticating and verifying web data in a privacy-preserving manner.
DECO Sandbox enables financial institutions and enterprises to quickly explore how to streamline user onboarding while maintaining data privacy and ensuring data provenance. Furthermore, Web3 developers can experiment with novel use cases, such as utilizing decentralized identity and Proof of Funds to allow institutional investors to participate in the DeFi economy via their offchain identities and credit histories, for example.
DECO Sandbox offers developers pre-configured use cases that showcase DECO’s capabilities and serve as frameworks for how they can run their own experiments and configure their own proofs. Developers can test scenarios such as conducting a client’s identity check without revealing their personal details, verifying a customer has sufficient funds across multiple bank accounts with data provenance from the account service providers, and conducting auditable sanctions screening with tamper-proof, time-stamped attestations of those checks.
The DECO technology is unique in that it requires no modifications at the data source and can be easily integrated into existing workflows and legacy tech stacks. DECO supports multiple methods of generating attestations about offchain data that can be consumed both onchain and offchain in a privacy-preserving manner.
Start exploring DECO Sandbox today to discover how privacy-preserving data verification can transform your operational efficiency and unlock new use cases in onchain finance and beyond.
Why Financial Markets Need Privacy-Preserving Data Verification
As the financial industry continues its digital transformation to a tokenized economy, the challenges around privacy, compliance, and onboarding become even more pronounced. Traditional identity verification methods, while familiar, are slow, prone to errors, and can add up to as much as $25,000 per client. Furthermore, the costs associated with Know Your Customer (KYC) can reach up to $30 million annually for larger institutions, taking up to 76 days on average to complete a KYC review in Japan, 84 in the United States, and 106 in Germany. These inefficiencies result from outdated manual processes and the need to comply with stringent privacy regulations like GDPR, which can result in costly data breach penalties.
By using advanced data verification solutions that align with data minimization principles, financial institutions and Web3 projects can validate information securely and reduce the risks associated with excessive data exposure. Privacy is not just a regulatory concern but a key business imperative—breaches in the financial sector can cost upwards of $375 million when involving large data sets. Reliable, privacy-preserving solutions could help institutions integrate seamlessly with legacy systems, reducing friction, minimizing manual intervention, and cutting compliance costs.
The need for efficient, privacy-preserving verification solutions is more critical than ever, as institutions must balance the need for speed in their operations with high-security standards. Institutions need solutions that not only address the current inefficiencies but are also future-proof for a tokenized world, where privacy, security, and compliance are intertwined with operational success.
Chainlink DECO: A Key Privacy Tool for Institutional Blockchain Adoption
As financial institutions continue innovating onchain, they increasingly rely on the Chainlink platform to synchronize onchain and offchain systems and to connect securely across blockchains, enabling seamless transactions and eliminating liquidity silos. In providing key infrastructure, Chainlink helps enable institutions to transact securely and seamlessly at scale with tokenized assets.
DECO is an advanced privacy-preserving data verification system that enables financial institutions, enterprises, and Web3 developers to verify sensitive information without exposing underlying data. DECO leverages zero-knowledge proofs (ZKPs) and Transport Layer Security (TLS) to help ensure privacy, provenance, and integrity. For a deeper look at DECO’s technology, check out our DECO Series and the DECO research paper.
DECO is designed to help institutions meet certain compliance and confidentiality requirements in a cost-efficient and privacy-preserving manner such as streamlining complex processes like identity checks and proof of funds. This not only introduces operational efficiencies for existing offchain processes, but it extends their user onboarding and compliance processes to onchain workflows involving tokenized assets and blockchains, ultimately helping institutions overcome key hurdles for launching in production.
Similarly, DECO empowers dApps and developers to experiment with privacy-preserving data verification for Web3 and DeFi use cases such as decentralized identity, creditworthiness, undercollateralized lending, or the validity of credentials without revealing sensitive user details. For Web3 projects, this creates opportunities to build secure, user-friendly applications that preserve the privacy of sensitive information while fostering seamless interactions across ecosystems.
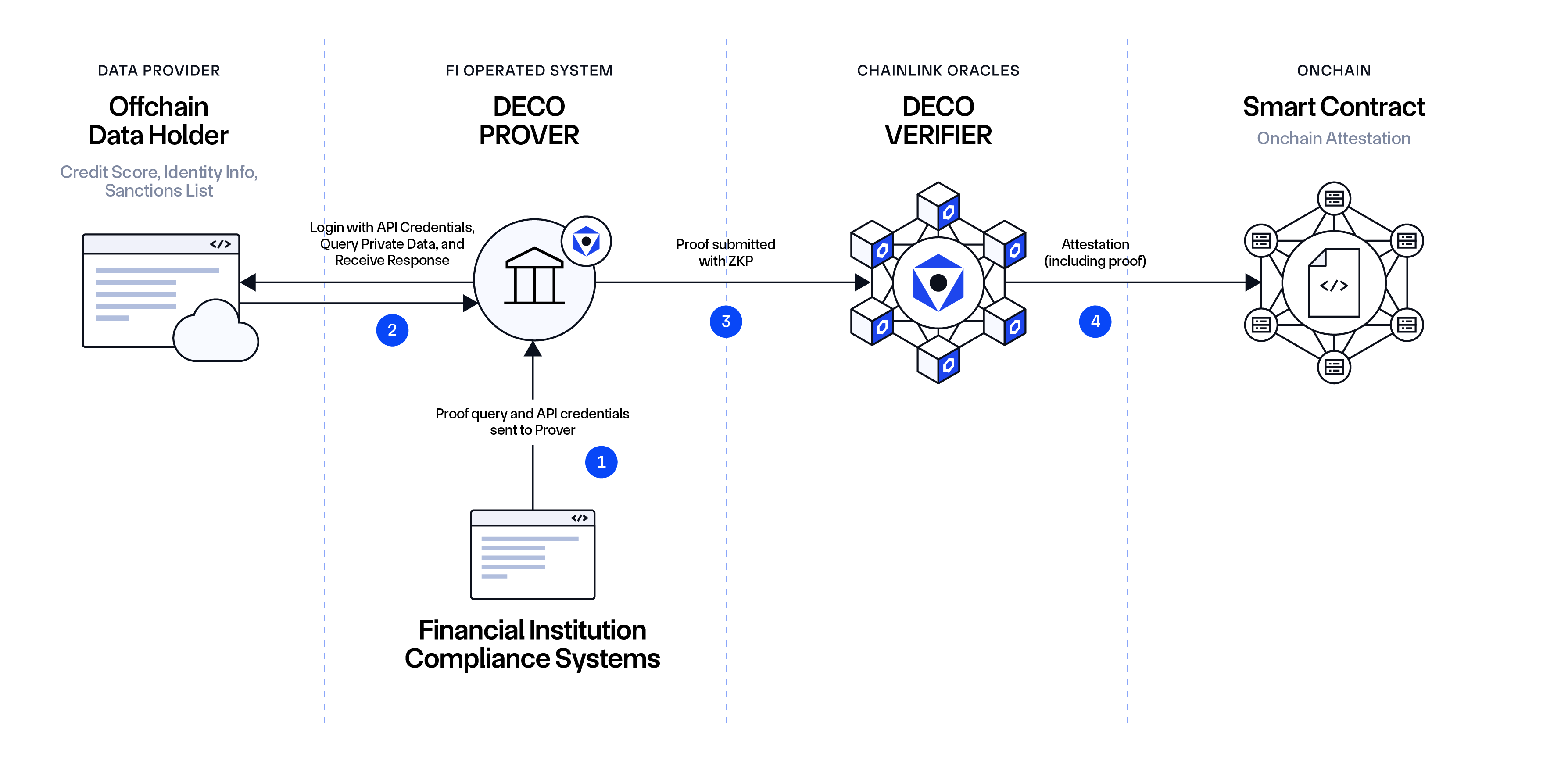
Workflow:
- Financial Institution Application submits its credentials for the Data Holder, as well as the content of the request to the DECO Prover, which is also running on the premises of the Financial Institution (FI).
- The DECO Prover retrieves the requested information from the Data Holder.
- DECO Prover selectively discloses or hides response information towards Chainlink Oracles (running DECO Verifier), along with proof of provenance. It can also prove (in zero-knowledge) that specific confidential information meets certain conditions without disclosing it.
- Chainlink Oracles run DECO Verifier to verify the received proof and create an attestation that is submitted onchain for consumption by the Smart Contract.
DECO Sandbox
DECO Sandbox allows institutions and developers to test how DECO technology can help streamline user onboarding, as well as explore how its privacy-preserving proofs can enhance data protection and help institutions meet their regulatory requirements. It also showcases how oracles and zero-knowledge proofs can drive efficiency and innovation in financial data protection with privacy-first solutions. With this hands-on environment, users can quickly explore and test privacy-preserving use cases within days.
As part of the DECO Sandbox, developers can access:
- An interactive sandbox for proof generation and verification, allowing users to prove both the provenance and authenticity of data. DECO’s provenance feature enables institutions to validate that the data they access comes from a trusted source, even when user authentication is required. Leveraging TLS, DECO offers secure and verifiable data exchanges, protecting data from tampering while maintaining confidentiality.
- Pre-configured examples such as identity checks, proof of funds, and sanctions screening.
- Configuration tools for flexible trial setups in custom use cases, including:
- HTTPS Requests: Configure the HTTPS request(s) that DECO will execute.
- Zero-Knowledge Assertions: Set up assertions to be computed in zero knowledge over the request and response messages.
- Selective Disclosure: Reveal non-sensitive parts of the request/response payloads, optimizing protocol performance.
- Public Field Assertions: Attest to assertions to public fields from the data source’s response after authentication.
- Templating: Use templates to improve configuration portability.
- Attestation: Upon successful testing, download the resulting attestation or post it to a testnet.
Key DECO Sandbox Use Cases
Identity Check: Privacy-Preserving Verification of User Identity
While financial institutions have robust processes for verifying customer identities, ensuring both privacy and compliance can sometimes lead to delays due to the manual handling of sensitive documents. As such, there is a growing need for more efficient, privacy-preserving methods to help meet rising regulatory demands such as KYC and AML.
Financial institutions, Web3 projects, and enterprises can verify a user’s identity without publicly exposing sensitive information or having to store it internally by using DECO for identity checks.
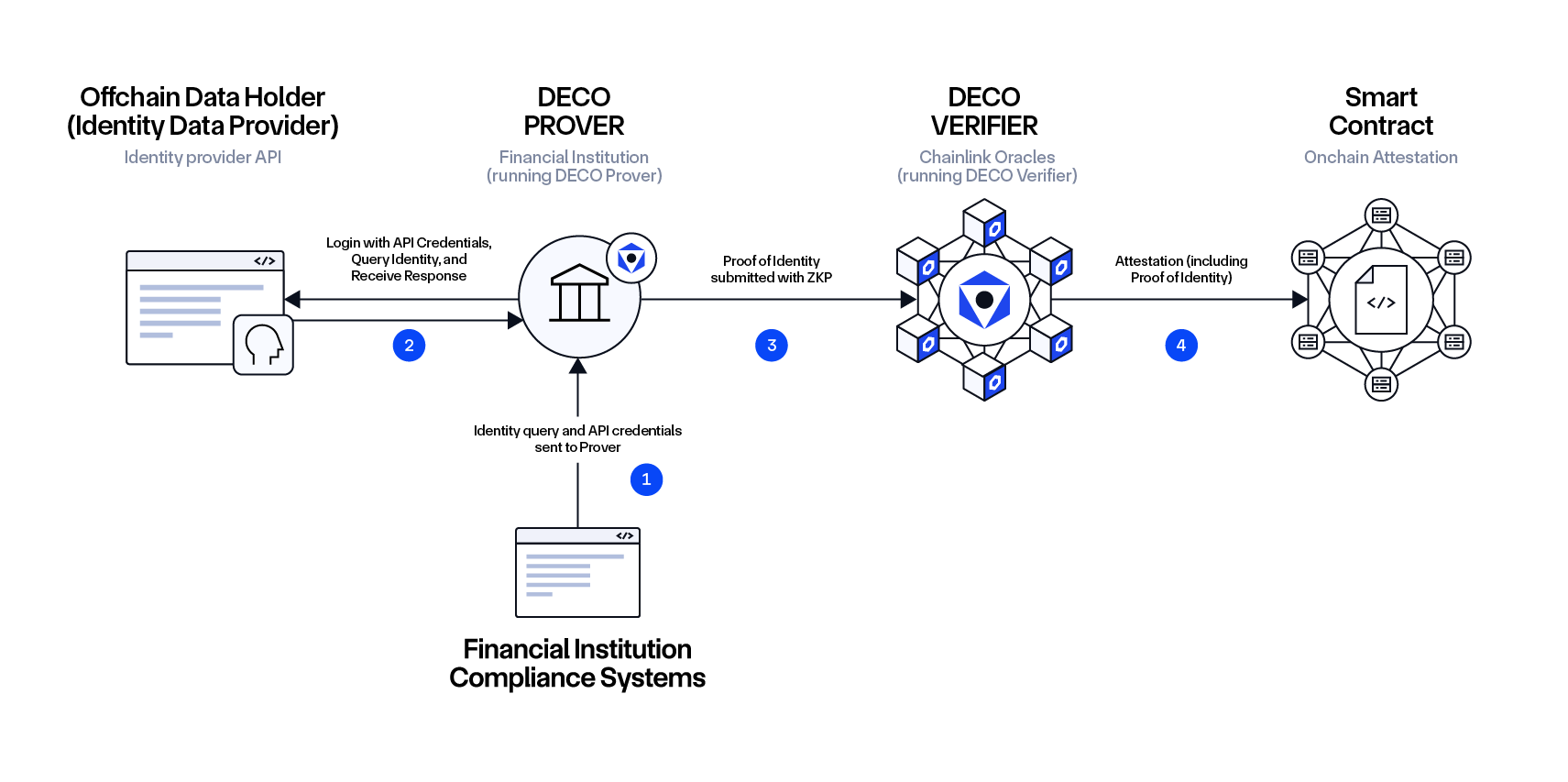
Workflow:
- The Financial Institution’s legacy application hands its API credentials and the customer’s identity query to the DECO Prover, which is operated by the Financial Institution.
- The DECO Prover interacts with the Identity Data Provider to query private data about the customer.
- The DECO Prover proves the correctness and provenance of selected claims about the customer to a set of Chainlink Oracle nodes running the DECO Verifier (e.g., that the customer is at least 18 years old).
- The Chainlink Oracles provide a time-stamped attestation that is submitted to an onchain smart contract (e.g., an institutional lending protocol).
- The smart contract verifies the claims about the customer based on the attestation, ensuring the process is secure and privacy-preserving.
Institution Proof of Funds: Privacy-Preserving Attestation of Liquidity
Financial institutions often need to provide verifiable evidence of their liquidity to meet regulatory requirements, manage counterparty risk, or conduct internal stress tests and audits. While current methods for generating proofs of funds are robust, they typically involve sharing sensitive financial data. Chainlink DECO enables institutions to create secure, privacy-preserving proofs of their financial standing without disclosing specific account details (e.g., balances), allowing institutions to maintain control over their data.
The following example demonstrates how Chainlink DECO enables financial institutions to securely and privately prove their liquidity when interacting with blockchain-based financial applications. It illustrates how institutions can generate attestation proofs of their financial standing that can be utilized by onchain financial applications, such as lending protocols, without disclosing sensitive data.
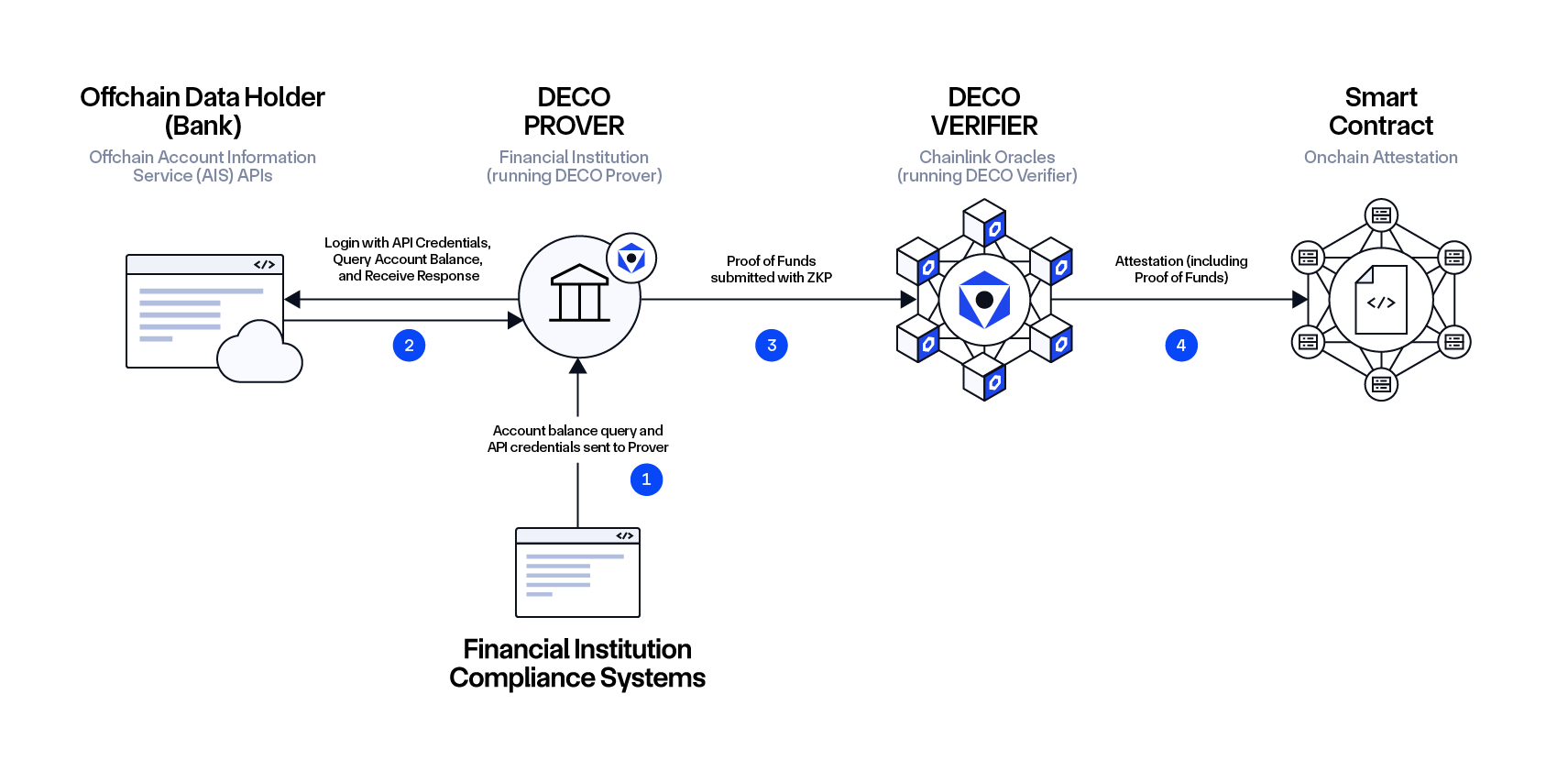
Workflow:
- The institution submits API credentials and the proof of funds query to the DECO Prover, which retrieves aggregate balance data from the Financial Institution’s internal systems and their banks (e.g., the Financial Institution is a bank or a fund that holds liquidity positions in other banks).
- The DECO Prover queries, retrieves, and processes the financial data, generating a zero-knowledge proof (ZKP) about the sum of the account balances without exposing individual account details.
- The DECO Verifier, via Chainlink Oracles, verifies the proof, ensuring the institution meets the required financial conditions without compromising privacy.
- The verified attestation is placed onchain for consumption by decentralized financial applications, enabling participation in DeFi while maintaining compliance.
Client Proof of Funds: Privacy-Preserving Verification of Sufficient Funds
Verifying that clients have sufficient funds for transactions is a critical aspect of financial operations. However, the need to protect sensitive financial data and ensure privacy often results in time-consuming processes.
DECO allows institutions to verify sufficient funds using ZKPs without requiring their customers to expose detailed account information. This helps streamline compliance checks, driving faster verification processes without compromising data security or privacy.
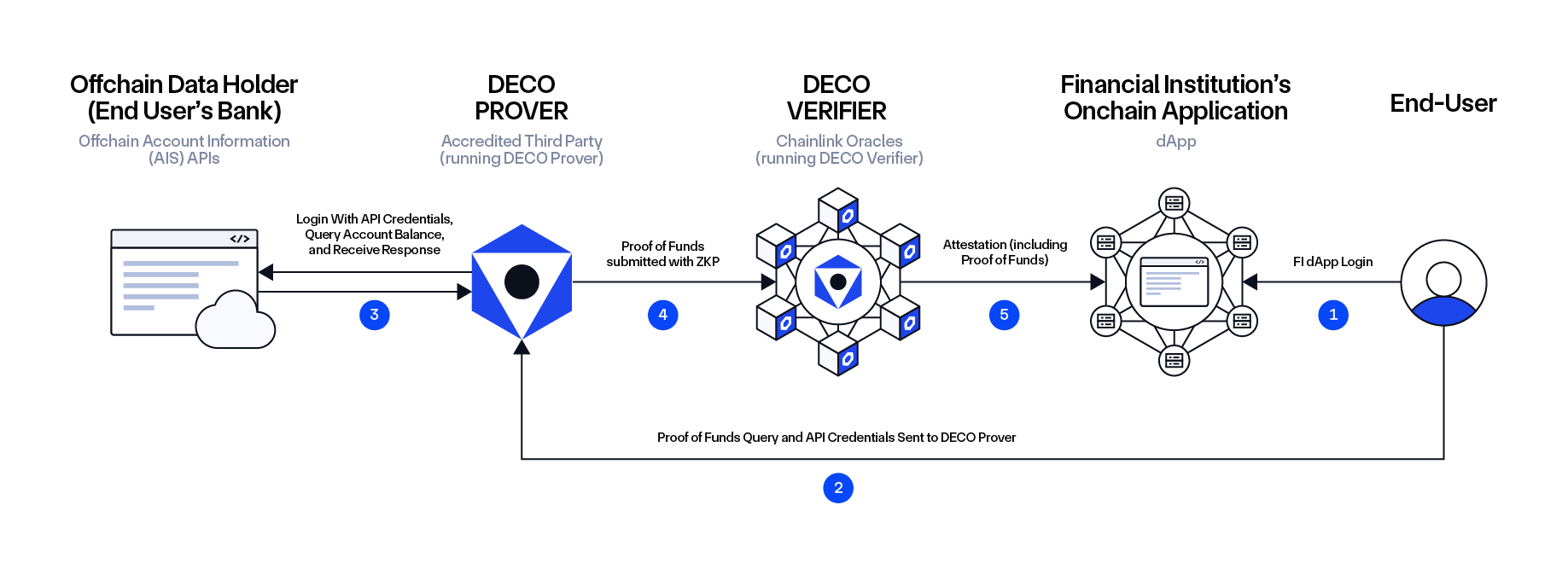
Workflow:
- The user (prover) authenticates in the Financial Institution’s onchain application to initiate a financial service request (e.g., borrowing), which requires a creditworthiness check.
- The user submits their API credentials and proof of funds query to the DECO Prover.
- The DECO Prover queries, retrieves, and processes the financial data, generating a zero-knowledge proof (ZKP) of total balances without exposing individual account details. This allows the verifier to verify the authenticity of the received report without seeing its contents.
- The prover and the verifier participate in a ZK protocol that (i) parses the account balances, (ii) computes their sums, and (iii) compares the sum against a predefined threshold. The verifier learns only the result of the final step, but not the individual balances or their sum.
- If the proof is successful, the verifier generates an attestation, which is shared with the institution to verify the user’s financial standing, ensuring privacy and security at every step.
Sanctions Screening: Privacy-Preserving Verification for Financial Institutions, Web3 Projects, and Corporates
Sanctions screening processes are typically well-established in financial institutions, but they can still pose challenges, particularly in managing the complexities of staying up-to-date with dynamic sanctions lists like OFAC’s. These processes often require extensive data handling, ongoing monitoring, and detailed record-keeping to meet compliance standards and pass audits. Ensuring the accuracy of these records while maintaining operational efficiency can be resource-intensive.
DECO helps automate sanctions checks by allowing institutions, Web3 projects, and corporates to privately verify whether an entity is on OFAC sanctions lists. Using DECO, institutions can also record a time-stamped, onchain attestation, simplifying record-keeping for audit and compliance purposes while maintaining the privacy of sensitive data.
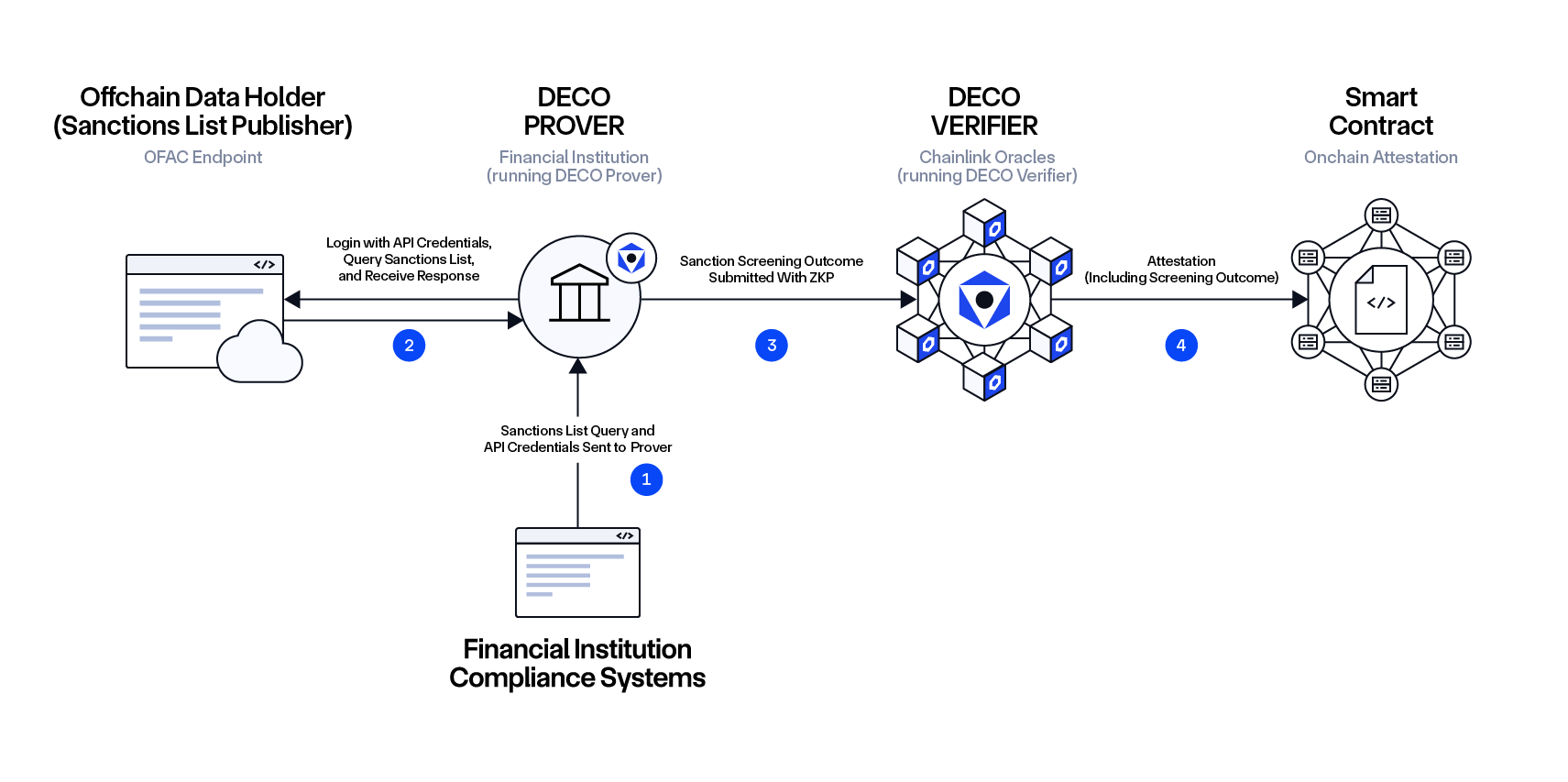
Workflow:
- The Financial Institution’s legacy application hands its API credential for the Sanctions List Publisher and the name of the entity to be checked to the DECO Prover, which also runs on the Financial Institution’s premises.
- The DECO Prover queries the Sanctions List Publisher to perform the check and verify whether the entity appears on any sanctions list.
- The DECO Prover proves to the Chainlink Oracle nodes, running the DECO Verifier, that the check was performed correctly with a valid source.
- The Chainlink Oracles submit a time-stamped attestation of the verification onchain to a smart contract, providing verifiable evidence that the check was completed at a specific time.
- The Financial Institution can reference the recorded attestation, supporting its compliance with sanctions regulations without exposing sensitive information.
Explore Your Own Use Case
DECO Sandbox encourages institutions and developers to experiment with proof generation and verification by customizing trials and exploring different use cases and verification scenarios.
Use this Question Wizard to help you identify a use case candidate to trial and see how DECO can address your institution’s needs securely and efficiently.
- Is your onboarding process slowed down by manual data handling and verification?
- Does your organization face challenges in proving the authenticity of the data provided by customers or sourced from third parties?
- Does your process involve verifying sensitive data from clients or counterparties?
- Is your organization repeatedly performing the same verification checks across different departments or entities?
- Does your process require periodic or recurring checks where changes in client circumstances are often missed?
- Are you relying on multiple external data sources or third-party verification services?
- Would you like to enhance your ability to prove to regulators that your institution has performed specific compliance checks?
- Is your institution facing challenges in identifying overexposure risks across multiple counterparties or financial instruments?
- Do your clients or partners hesitate to share sensitive financial or personal information due to concerns about data breaches or misuse?
If you said yes to any of these questions, start exploring the DECO Sandbox today to see how it can transform your compliance and onboarding processes. With DECO, institutions can improve operational efficiency, reduce compliance burdens, and maintain customer trust—all while proving the authenticity of their data. Furthermore, Web3 developers can experiment with completely new onchain use cases that leverage sensitive data in a privacy-preserving manner.
Enhancing Onchain Golden Records With DECO and Other Chainlink Privacy Solutions
Chainlink’s Onchain Golden Record (OGR) concept is designed to unlock the full potential of tokenized assets, where all the data, functionality, and connections needed to facilitate automated, real-time transactions are directly embedded in the token’s smart contract and move with the asset as it’s transferred across the multi-chain economy. The OGR serves as a single source of truth about the history and key properties of the asset, which is referenceable by all market participants, as well as drives scalable markets since all asset servicing requirements are attached to the asset.
DECO enhances OGRs with identity verification and other privacy-preserving data capabilities, unlocking a new paradigm to onchain identity. Instead of needing a referenceable list of addresses stored in a smart contract that must be consistently maintained, identity verification based on existing web data can be directly embedded in the asset and remain with the asset as it travels cross-chain. This ensures users have to meet the identity requirements associated with that asset no matter where the asset resides in the multi-chain economy. Such a design is not only more practical given it leverages established API infrastructure without requiring modifications, but it’s also more scalable as there is no need for ongoing list maintenance.
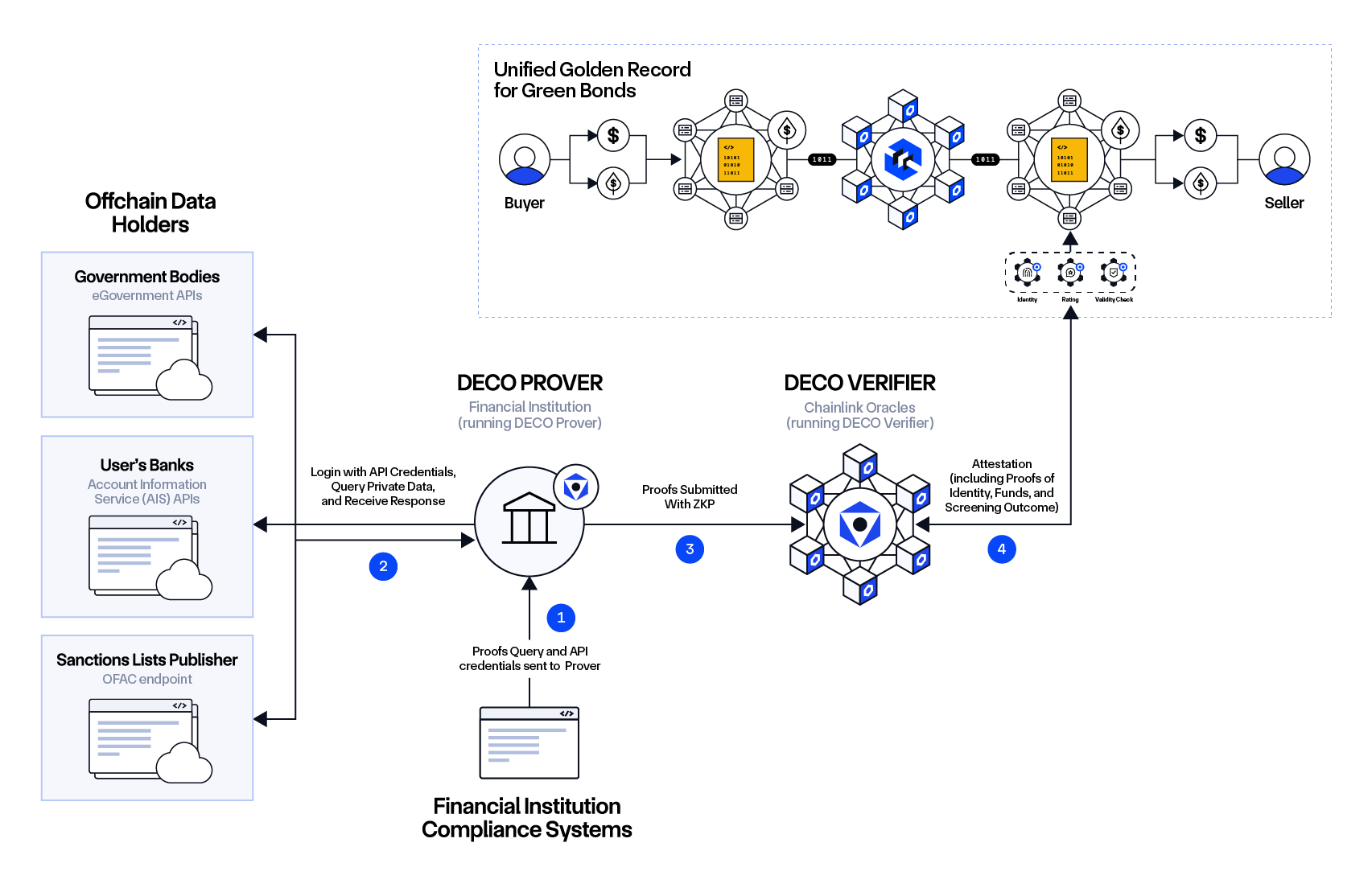
DECO is part of a suite of privacy solutions that solve different privacy concerns for institutions and Web3 developers:
- Privacy for data entering and leaving blockchains: The Blockchain Privacy Manager enables institutions to integrate the public Chainlink Platform and their existing systems with private blockchain networks while limiting onchain data exposure.
- Privacy for cross-chain transactions: CCIP Private Transactions leverages the Blockchain Privacy Manager and a novel onchain encryption/decryption protocol to enable institutions to transact across multiple private blockchains using the public CCIP network, while keeping the transaction details fully confidential.
- Privacy for onchain data: DECO enables statements about offchain data to be shared onchain without revealing the underlying data.
If you are interested in Chainlink Privacy solutions, read our blog about The Chainlink Platform Privacy Suite.
—
Disclaimer: This post is for informational purposes only and contains statements about the future, including anticipated product features, development, and timelines for the rollout of these features. These statements are only predictions and reflect current beliefs and expectations with respect to future events; they are based on assumptions and are subject to risk, uncertainties, and changes at any time. There can be no assurance that actual results will not differ materially from those expressed in these statements, although we believe them to be based on reasonable assumptions. All statements are valid only as of the date first posted. These statements may not reflect future developments due to user feedback or later events, and we may not update this post in response.
