Chainlink CCIP’s Defense-In-Depth Security and the Risk Management Network
The blockchain ecosystem is highly heterogeneous. There are already hundreds of blockchains, layer-2 and layer-3 networks, sidechains, subnets, appchains, parachains, and other environments, with the ecosystem likely to continue to grow to eventually encompass thousands of chains.
To unlock the full potential and functionality of these thousands of chains, they will need to securely interoperate with the rest of the ecosystem, making secure cross-chain interoperability provided by Chainlink CCIP an immediate necessity. CCIP was designed from the ground up to provide the cross-chain market with unprecedented security that borrows software engineering principles from the aerospace industry to maximize redundancy and fault tolerance.
In this post, we outline the need for secure cross-chain interoperability and why Chainlink CCIP and its first-of-its-kind Risk Management Network is the only solution that can provide this growing market with mission-critical infrastructure.
This post is based on Chainlink Labs’ Head of R&D Lorenz Breidenbach’s SmartCon 2023 presentation:
The Importance of Cross-Chain Security
As of October 2023, $400B+ has been bridged between blockchains, while $2.6B+ has been lost to cross-chain bridge exploits. Based on these figures, there’s approximately a 1 in 150 chance that any given bridged dollar will be lost to a cross-chain bridge exploit. For the Web3 industry to reach its next phase of adoption and bring the benefits of cryptographic truth to billions of users around the world, cross-chain security needs to level up.
Cross-chain protocols are inherently complex due to a variety of factors—they involve a number of technologies, they target different heterogeneous chains, and the software engineers and security researchers designing them have to master multiple distinct fields, including distributed systems, cryptography, and smart contract engineering.
Due to cross-chain infrastructure running on public blockchains on the public Internet, cross-chain protocols present one of the largest attack surfaces in the blockchain industry. If cross-chain infrastructure is vulnerable to exploits, sophisticated adversaries, including state-level actors, look to exploit the protocol and drain the value that the cross-chain protocol interacts with.
These factors directly informed the design philosophy of Chainlink CCIP, which focuses on end-to-end system security as its top priority. Putting this into practice involves minimizing complexity and single points of failure through a defense-in-depth approach and broad spectrum protection against whole classes of attacks.
Chainlink CCIP: The Level-Five Interoperability Standard
CCIP’s security model is built with the underlying design paradigms that safety is more important than liveness and end-to-end security is paramount. This approach helps ensure that—despite all the hardening, multiple independent audits, and collaboration with independent security researchers—if an exploit does happen, the defense-in-depth security architecture of CCIP can mitigate the potential extent of the compromise.
CCIP provides Web3 projects with native level-five cross-chain security so that a secure cross-chain economy can be built on solid foundations. CCIP utilizes multiple decentralized networks to secure a single cross-chain transaction, along with incorporating additional risk management systems to identify risks and take actions to prevent them, such as by implementing emergency shutdowns or imposing rate limits.
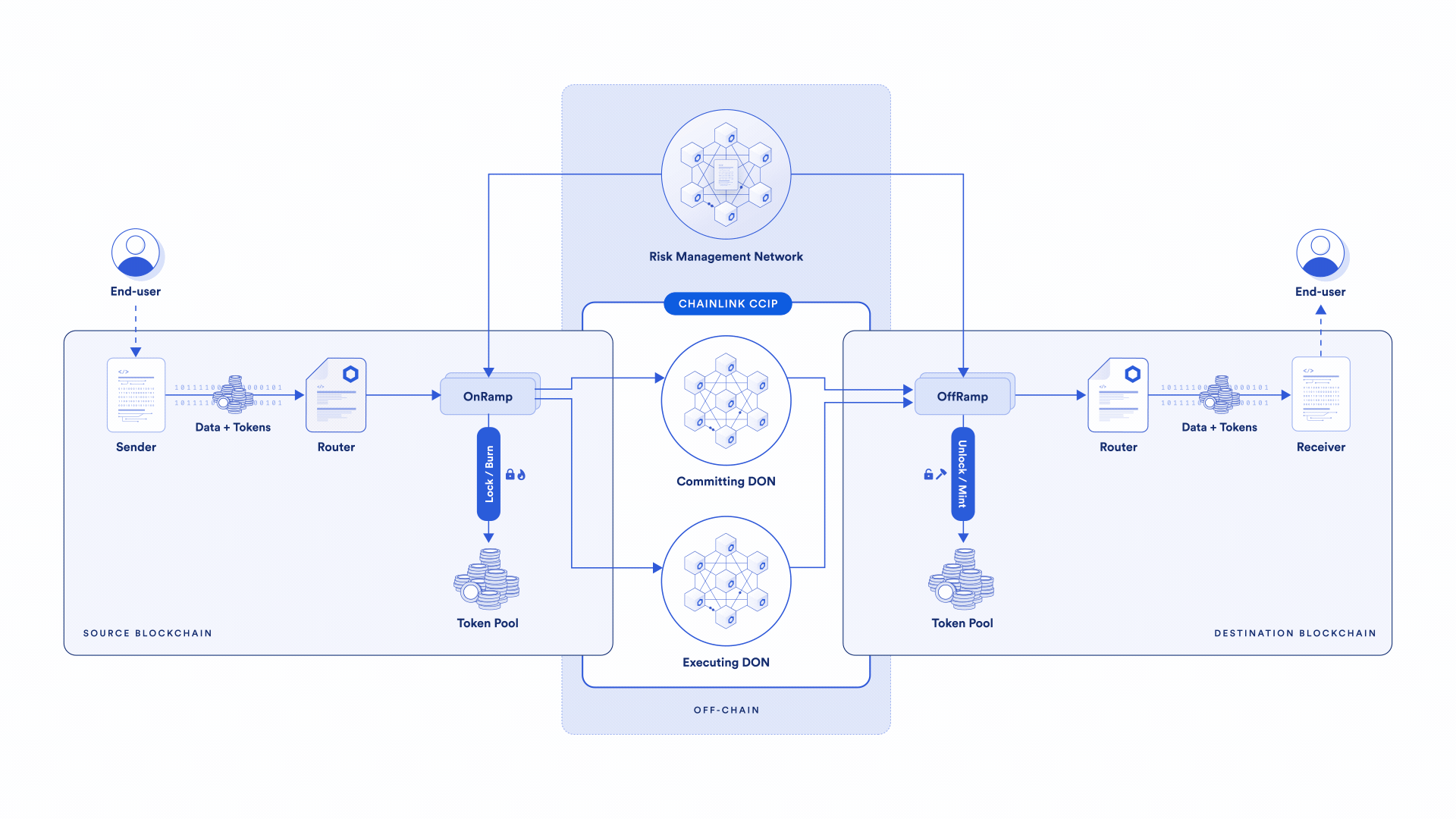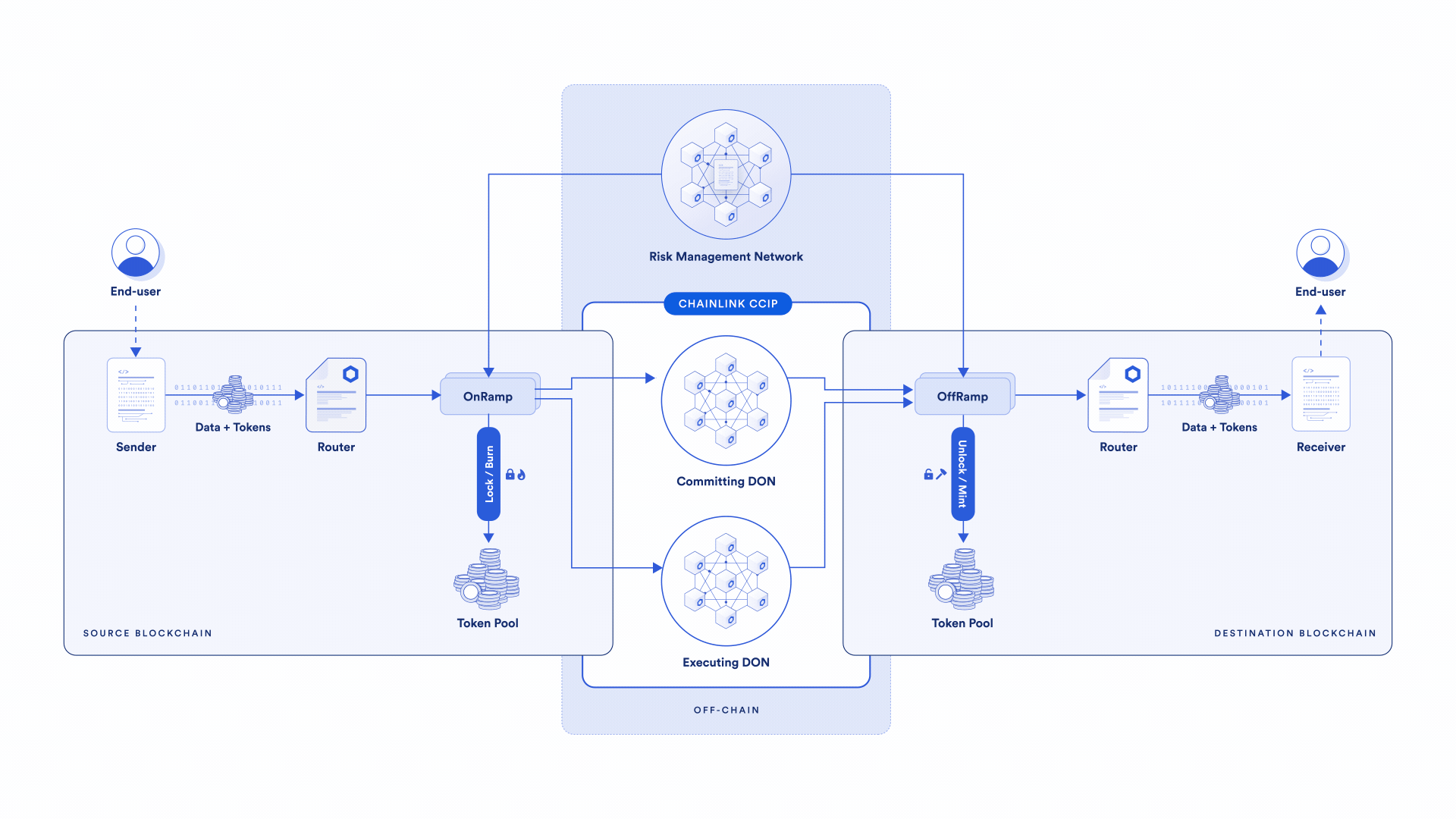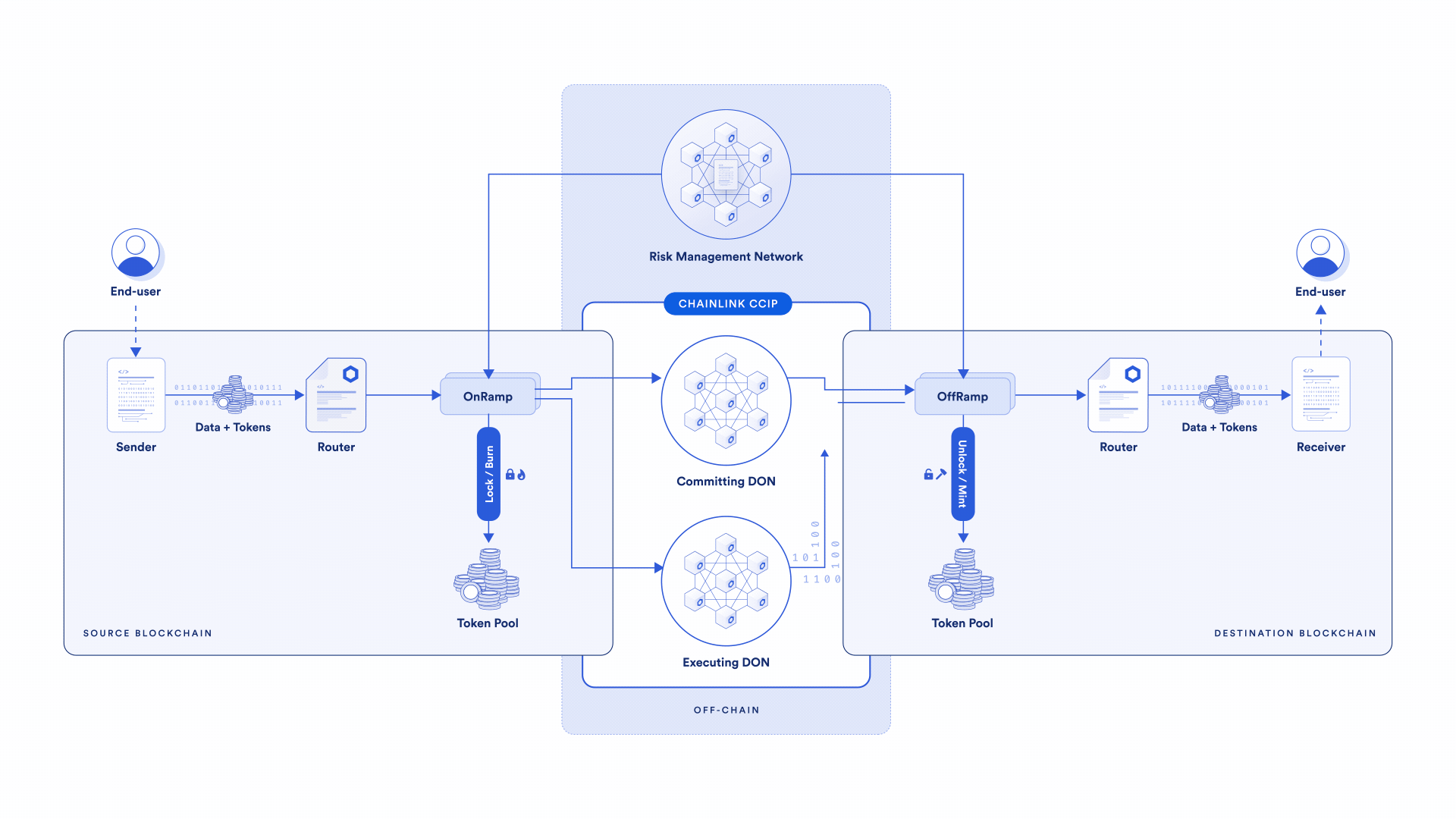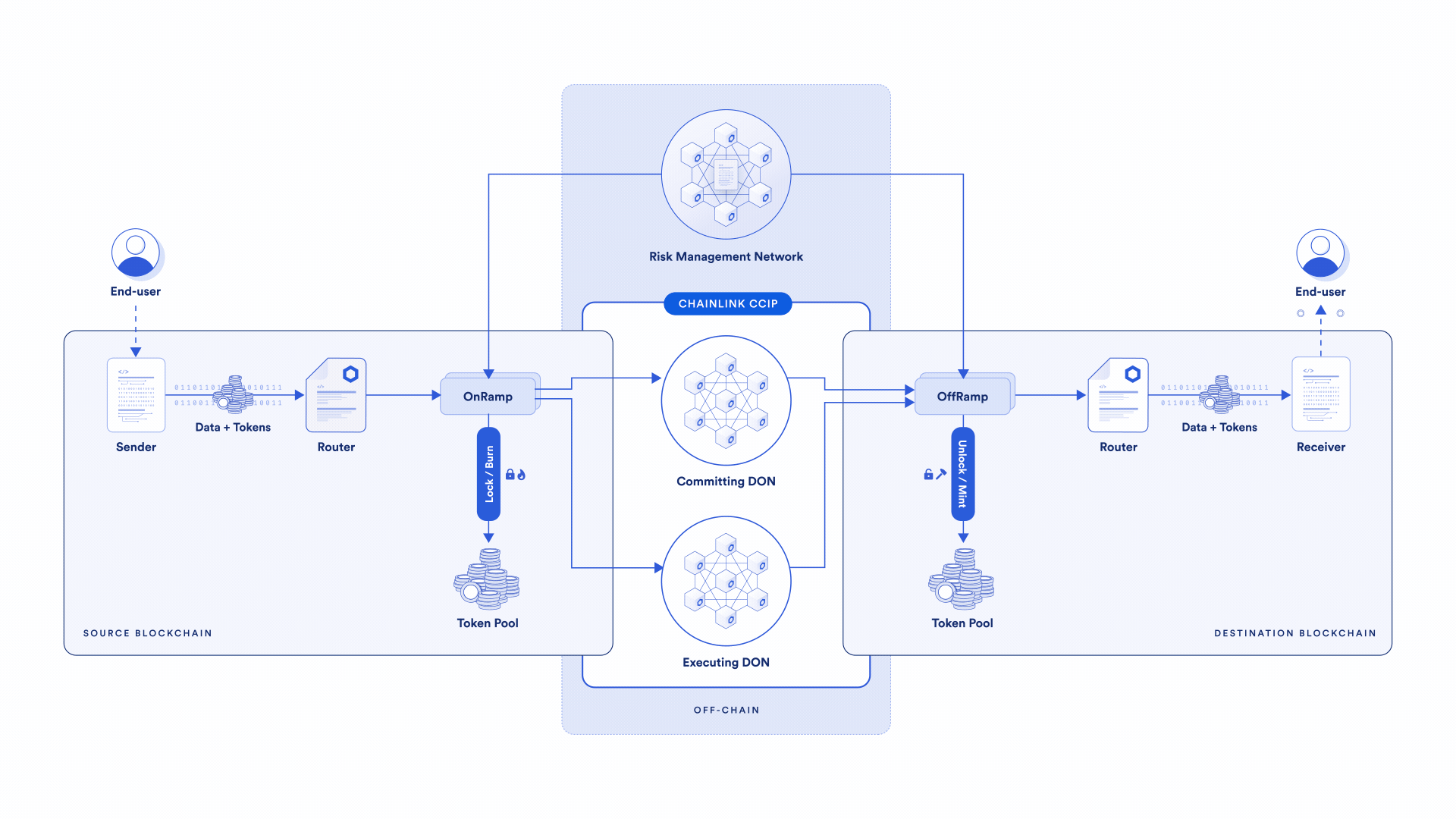
CCIP provides several key security benefits:
- Multiple independent nodes run by independent key holders.
- Three decentralized networks all executing and verifying every cross-chain transaction.
- Separation of responsibilities, with distinct sets of node operators, and with no nodes shared between the transactional DONs and the Risk Management Network.
- Increased decentralization with two separate code bases across two different implementations, written in two different languages to create a previously unseen diversity of software clients in the cross-chain world.
- A trusted computing base of only about 10,000 lines of code—a manageable size for such safety-critical infrastructure as CCIP.
- Never-before-seen level of risk management that can be rapidly adapted to any new risks or attacks that appear for cross-chain messaging.
If you’d like to learn more about how CCIP’s security sets a new standard in cross-chain interoperability, read The Five Levels of Cross-Chain Security.
The Unique Security Features of CCIP
Risk Management Network
The Risk Management Network is a separate, independent network that continuously monitors and validates the behavior of the primary CCIP network, providing an additional layer of security by independently verifying cross-chain operations. The Risk Management Network is built in a different programming language than the CCIP primary system (Rust rather than Go) and is developed by a different development team inside Chainlink Labs.
The Risk Management Network applies a software engineering principle introduced in the 1980s called N-version programming (NVP) that has been used to increase redundancy and fault tolerance in safety-critical infrastructure in the aerospace industry.
NVP involves having multiple independent implementations of a system running in parallel and comparing their outputs to ensure that they match. If the outputs match, the system is running as intended. However, if there’s a discrepancy in the outputs provided by the different implementations, appropriate measures can be taken to mitigate the extent of potential damage.
In the aerospace industry, mission-critical systems must operate continuously without interruption. However, as mentioned above, in case of system malfunctions, CCIP prioritizes safety over continuous operation. This design choice allows CCIP to be automatically paused in order to minimize the trusted computing base.
In the following section, we describe three key defense-in-depth measures implemented by CCIP that provide unprecedented security and broad protection for cross-chain interoperability.
Rate Limiting
Rate limiting provides the ability to cap the amount of value over a given time period that flows in and out of CCIP at the smart contract level. This is possible due to CCIP’s value-aware approach: Messages in the CCIP system explicitly list the tokens and the amount of tokens included in token transfer messages so that the CCIP logic is aware of the value being transferred and can take appropriate measures depending on this amount.
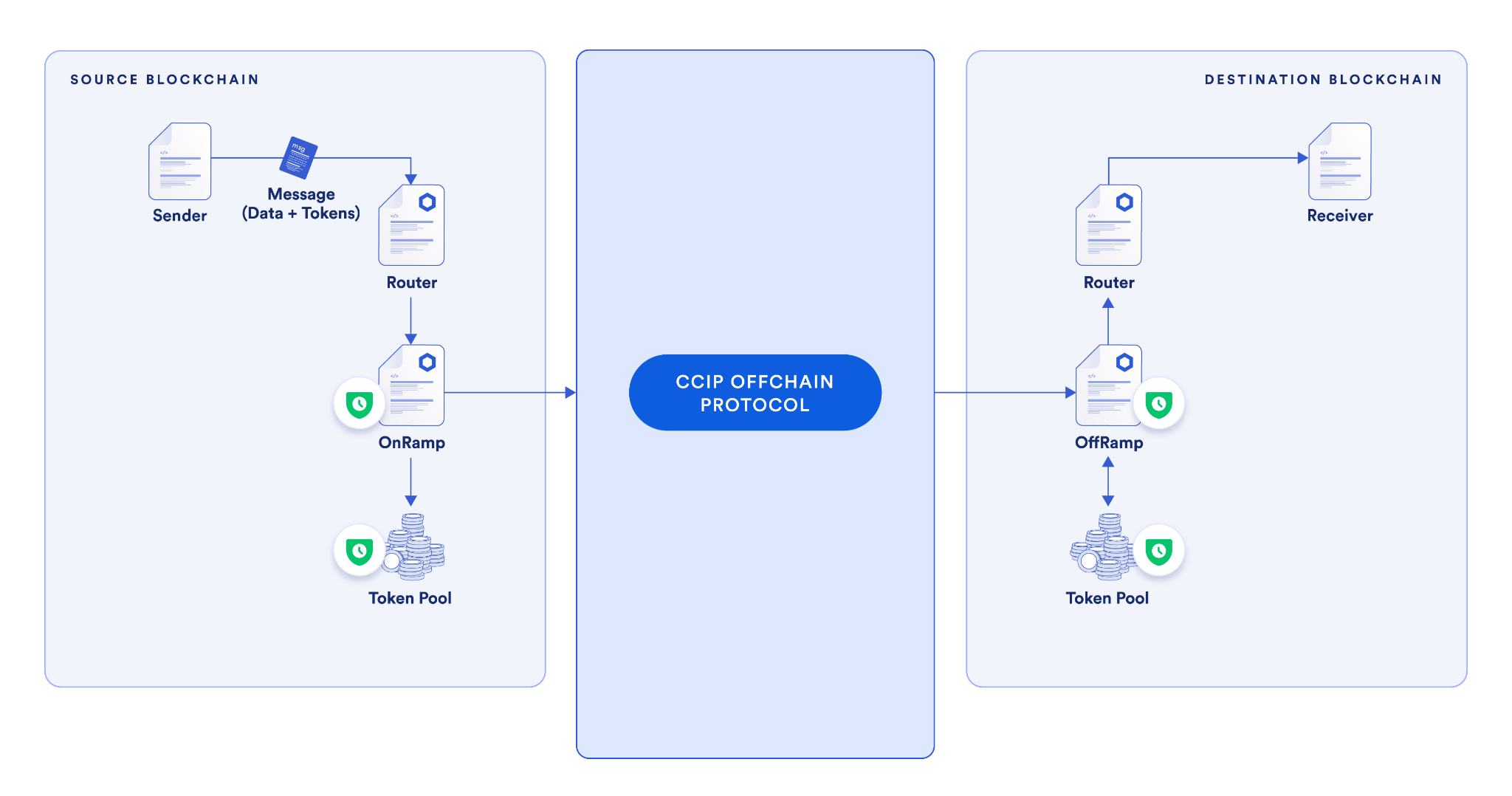
In token pools, the amount of tokens that can be locked/burned or minted within a specific time frame can be limited, and this is configurable per token and source/destination blockchain. For OnRamps and OffRamps, the amount of aggregate value that flows through a particular source and destination chain can be limited. These rate-limiting mechanisms add an extra layer of security and help ensure that even if the cross-chain protocol helps secure a large amount of value, only a specified portion of that value can move at a time, limiting the potential impact of an attack.
Secondary Approval
Implemented in the Risk Management Network and codified in the CCIP smart contracts, secondary approval (or “blessing”) involves a second confirmation by the Risk Management Network before any message becomes executable. The Risk Management Network independently constructs its own cryptographic commitment to the message and sends that to the Risk Management Contract on the destination chain for that approval to be stored.
This means that the Risk Management Network has to explicitly approve any message before it can be executed. Any cross-chain message flowing through CCIP is independently approved by both the primary system’s Committing DON and the Risk Management Network—only then does the cross-chain message become executable by the Executing DON.
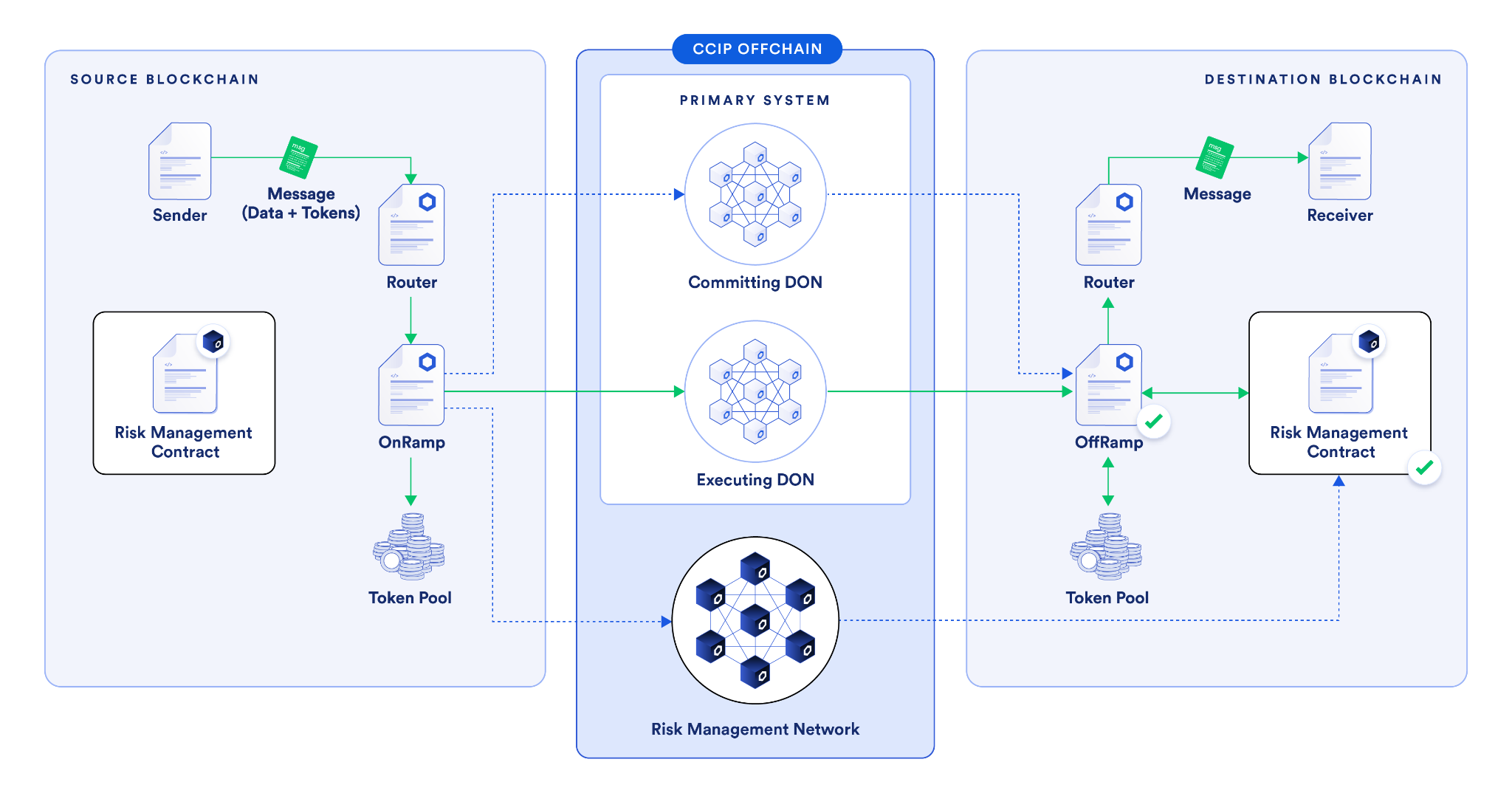
The use of secondary approval serves as an effective security safeguard. Even if the primary system experiences critical vulnerabilities, such as a key compromise, node operator collusion, software supply chain vulnerability, or other smart contract bugs, CCIP provides broad spectrum defense against all of these issues.
Additionally, as the Risk Management Network is an independent system, it’s extremely unlikely that it would be affected by the same issue as the CCIP primary system. This approach is exemplary of how CCIP practices defense-in-depth and multiple layers of protection through advanced risk management techniques.
If you’d like to learn more about the features of the Risk Management Network, check out the CCIP documentation.
Anomaly Detection
The Risk Management Network continuously monitors all blockchains connected to the CCIP system. If it identifies any anomalous activity, such as a false message or irregular token flow going from a token pool to an adversarial address, it can immediately pause cross-chain activity.
In such cases, the Risk Management Network would be able to detect the anomaly and send a “curse” transaction to all Risk Management Contracts on all blockchains that CCIP is active on and immediately halt cross-chain activity to provide time for security experts to investigate the issue and if required deploy a mitigation.
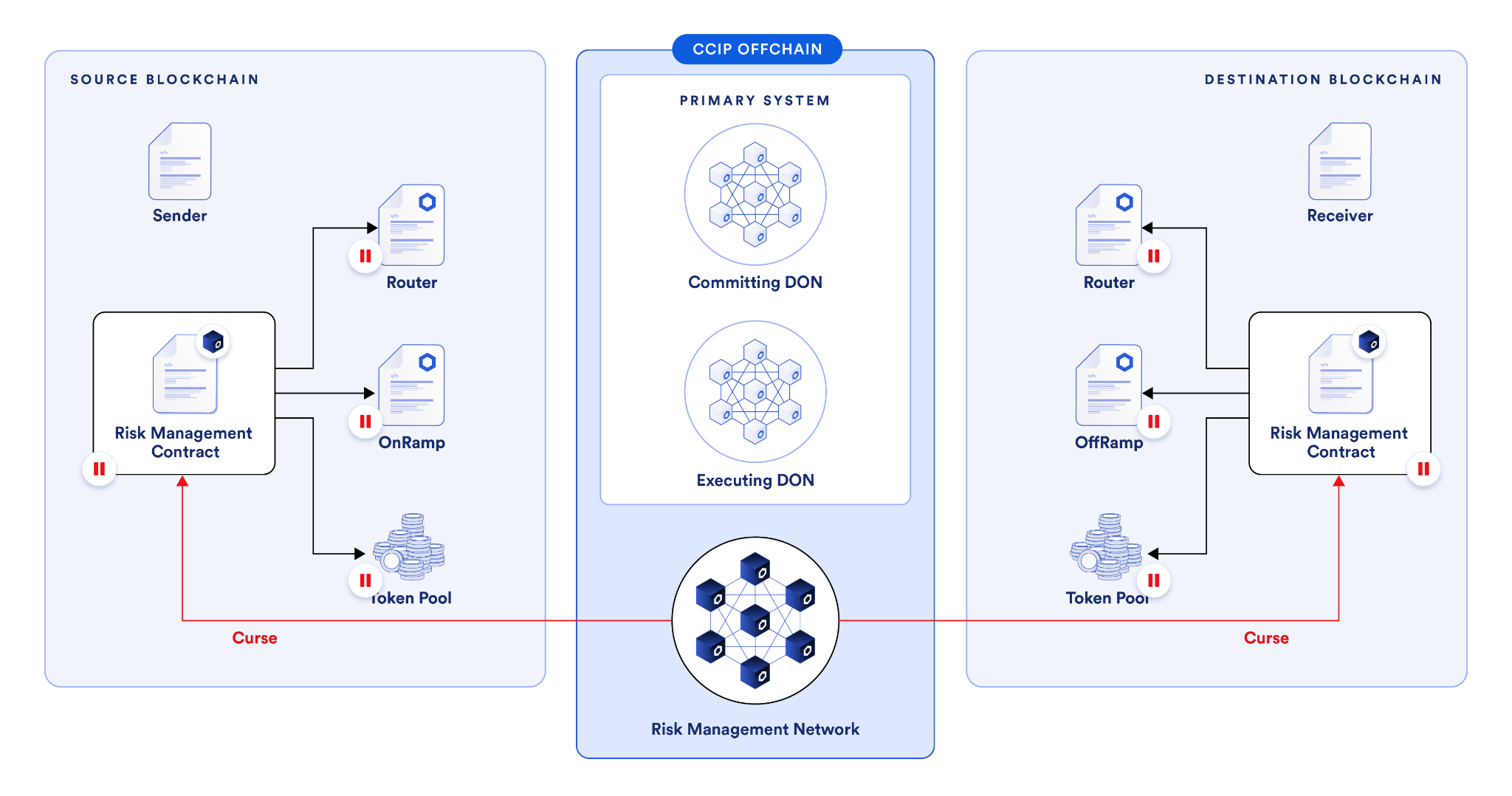
Combined with rate limiting, anomaly detection forms a robust, multi-layered defense framework. An adversary can only have one opportunity before the anomaly is detected and the system is halted, and the extent of that attack can also be restricted since rate limiting caps the amount the attacker can extract.
Solving the Cross-Chain Security Problem
Just as Chainlink solved the oracle problem by bringing Chainlink Price Feeds to market in 2019 to provide secure and reliable market data to the DeFi space, Chainlink CCIP is now solving the cross-chain security problem by providing industry-standard security and reliability to a wide variety of cross-chain use cases.
Zoom in. pic.twitter.com/5NLkYipvoI
— Chainlink (@chainlink) February 11, 2024
This is why leading DeFi projects such as Aave, Synthetix, and many more are using Chainlink CCIP to create cross-chain Web3 applications, and why Swift and more than a dozen large banks and financial institutions demonstrated how financial institutions can utilize CCIP to facilitate cross-chain transactions across public and private blockchains using their existing infrastructure stack.
If you’d like to take a deeper look at the Risk Management Network, explore the source code on GitHub.
If you want to learn more about CCIP’s underlying architecture and code and start building highly secure and reliable cross-chain use cases, check out the CCIP developer documentation.
