Chainlink Automated Compliance Engine (ACE): Technical Overview
The Automated Compliance Engine (ACE) is a unified and modular standard to solve all onchain compliance problems and bring institutional capital onchain. Powered by the Chainlink Runtime Environment (CRE), Chainlink ACE is enabling anyone across traditional or decentralized finance to build, manage, and execute complex financial transactions across multiple jurisdictions, counterparties, digital assets, and execution environments, including public and private chains—all in a compliance-focused and privacy-preserving manner.
This blog will provide a deep dive into the technical components, services, and solution accelerators offered as part of the Chainlink ACE. For a general, non-technical overview, read the launch blog: Introducing Chainlink Automated Compliance Engine (ACE).
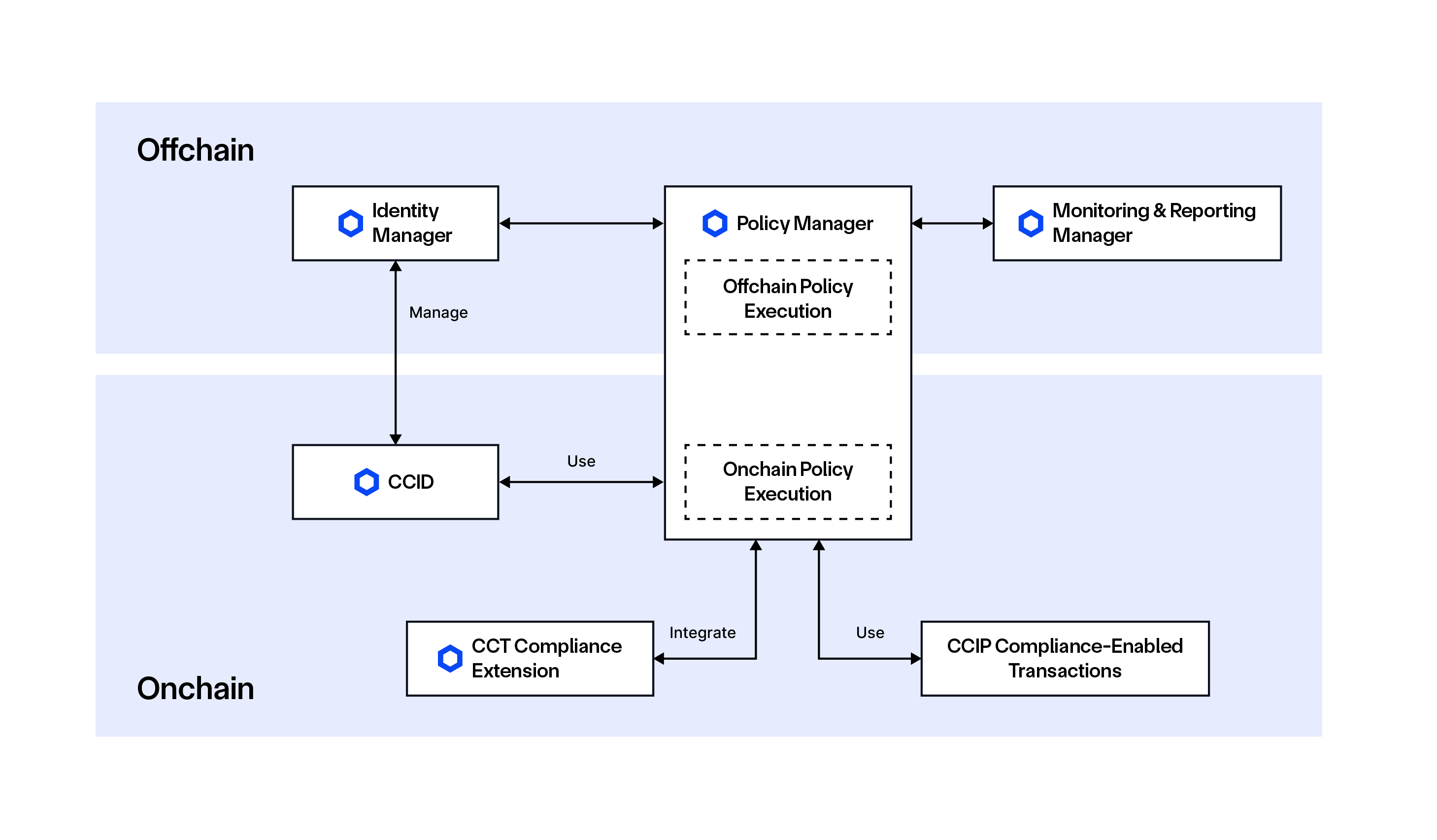
Core Components
In Chainlink ACE, components are defined as the foundational onchain primitives—typically smart contracts—that provide the base infrastructure for identity, token compliance, and policy enforcement. These components are reusable, composable, and serve as the backbone for building higher-level compliance services and integrations. There are two core components to the Automated Compliance Engine: CCID and CCT Compliance Extension.
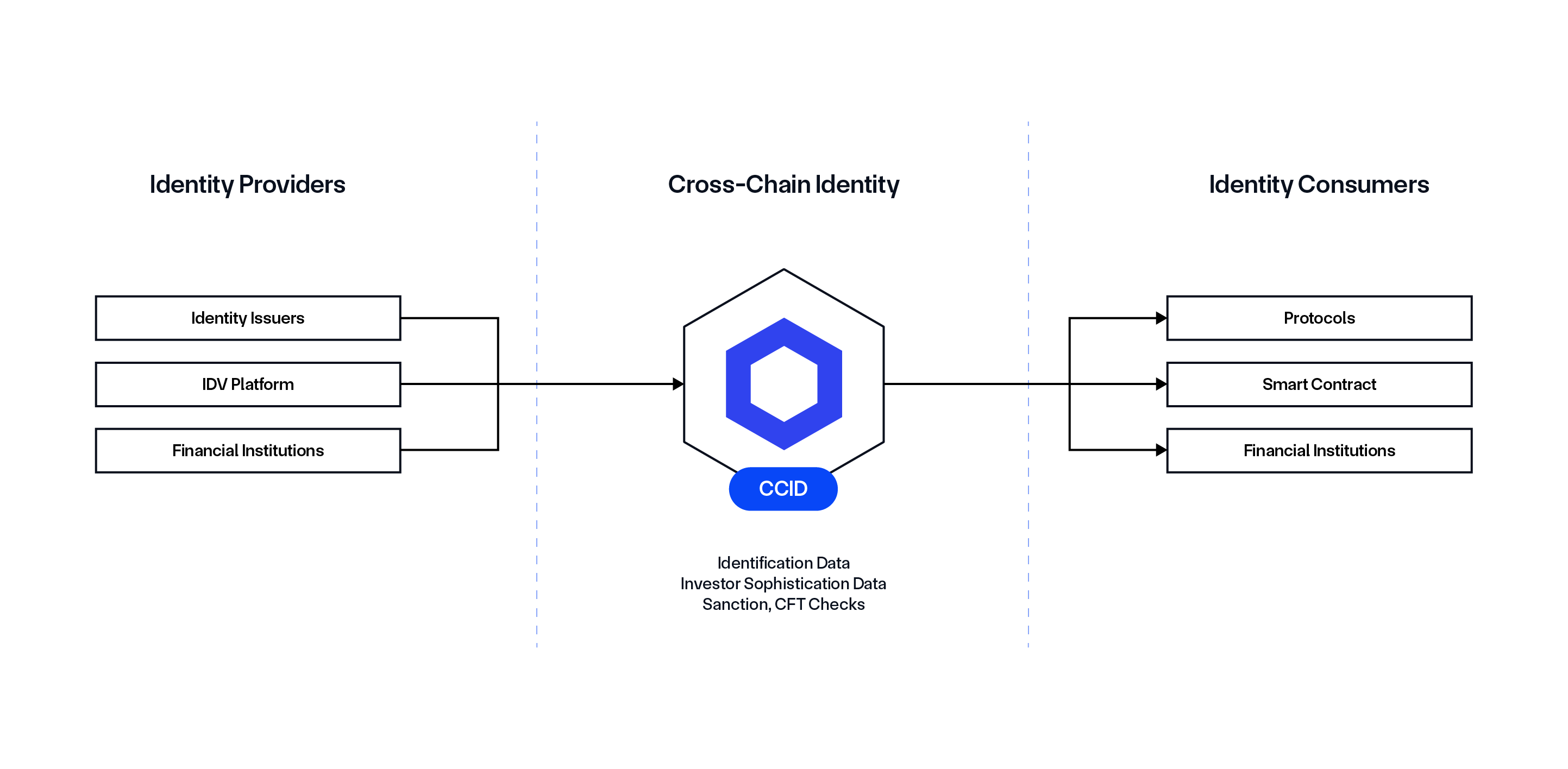
Cross-Chain Identity (CCID) Framework
CCID is a reusable identity framework for representing investor identities, attestations, and credentials across multiple blockchains by storing cryptographic proofs of verified credentials, including KYC, AML, investor sophistication status, and more, while keeping personal information (e.g., NPI/PII) stored offchain. CCID is compatible with existing identity standards, such as LEI/vLEI, ONCHAINID, and DIDS.
Prior to CCID, users had to pass KYC every time they onboarded to a platform. With CCID, KYC can be completed once, with all accumulated credentials and attestations collected and stored via CCID. This enables them to be reused as a reliable proof of KYC across different platforms that accept those identity credentials.
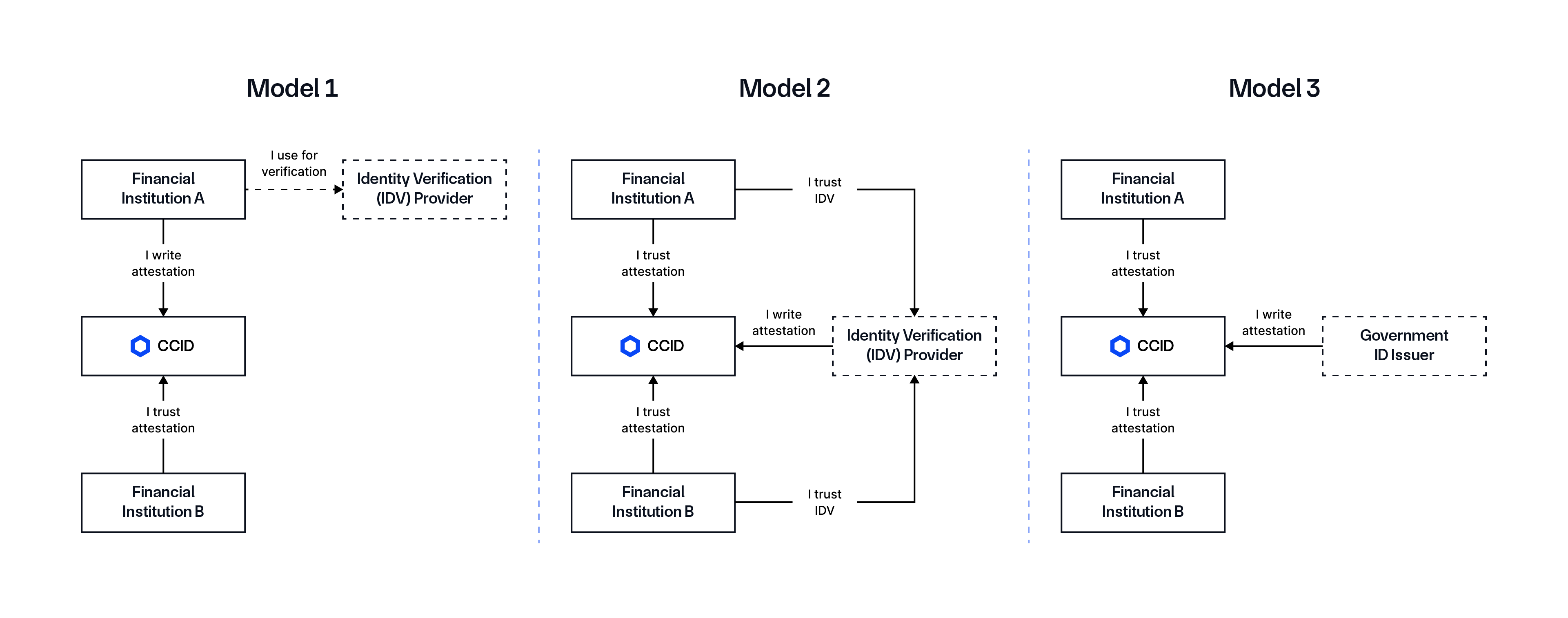
CCID supports multiple trust models, including:
- Model 1: Asset issuers provide attestations, and other asset issuers and ecosystem members trust them.
- Model 2: Identity verification (IDV) platforms provide attestations, and asset issuers and other ecosystem members trust them.
- Model 3: Governments serve as the primary identity issuer, while various financial institutions and IDVs verify and attest to the identity with different credentials and attestations.
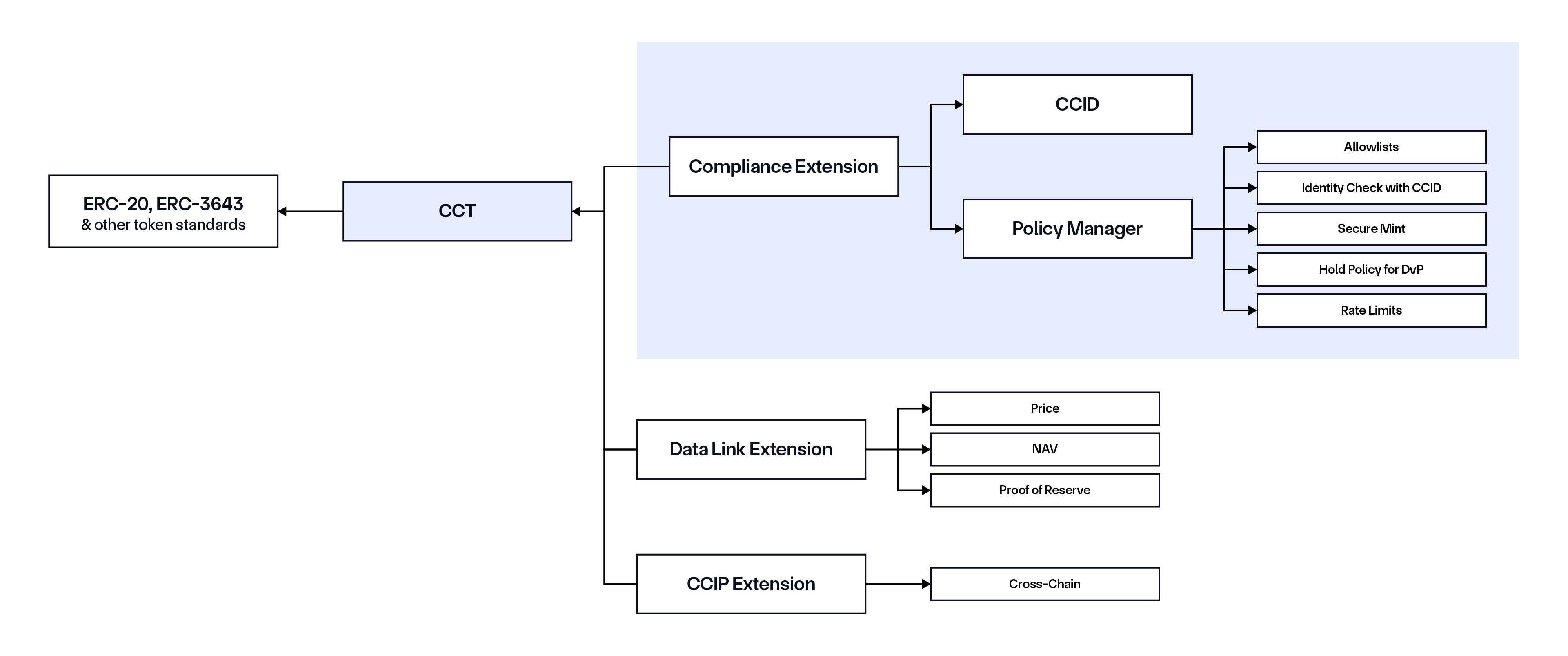
CCT Compliance Extension
CCT (Cross-Chain Token) is currently recognized as a token standard that enables token developers to make new and existing tokens cross-chain enabled via the Cross-Chain Interoperability Protocol (CCIP). CCT supports self-serve deployments, full control and ownership for developers, enhanced programmability, and zero-slippage transfers—all backed by CCIP’s industry-standard defense-in-depth security. Notably, CCTs are token logic agnostic, meaning token developers can deploy pre-audited token pool contracts to turn any ERC-20-compatible token into a CCT or deploy their own custom token pool contracts for bespoke token use cases.
With this launch, CCT is evolving into a universal connector to a variety of Chainlink services. The CCT Compliance Extension is a lightweight interface that enables any token to support compliance functionality by integrating it with the Automated Compliance Engine. It functions as a connector between smart contracts and CCID and the Policy Manager. On the other hand, the CCIP Extension enables cross-chain transferability via CCIP, while the Data Link extension enables the token to be enriched with critical asset data (e.g., pricing, NAV, proof of reserves) via the Chainlink data standard. CCT extensions can be easily applied across existing token standards, including ERC-20, ERC-3643, and more.
Core Services
Services are defined as offchain components running on the CRE that help manage onchain interactions and configurations of Chainlink ACE. There are currently three services that are part of the Automated Compliance Engine: Policy Manager, Identity Manager, and Monitoring & Reporting Manager.
Policy Manager
The Policy Manager is a customizable rules engine that enables users to define, manage, and enforce compliance policies directly within smart contracts. The Policy Manager has both an onchain part, which is a set of smart contracts, and an offchain part to facilitate both onchain and offchain policy execution. Policy enforcement can be implemented to satisfy regulatory requirements (e.g., investor sophistication certification) or internal business rules (e.g., transaction limits, collateral requirements). Ultimately, policy enforcement is critical for managing operational, financial, legal, and reputational risks with regulated tokenized and digital assets.
During the policy lifecycle, each policy needs to be:
- Defined—An asset issuer needs a place to write and configure the policy, which should happen in an offchain environment as code, pseudo-code, or another form of configuration.
- Executed—Before a transaction occurs, the policy must be executed onchain or offchain, wherein the transaction data is aggregated and a deterministic decision on policy verification is provided.
- Enforced—In traditional finance, execution and enforcement typically happen together. However, in decentralized environments, enforcement may occur separately. A final proof is generated onchain verifying that the policy was successfully executed and that the onchain transaction was either approved or denied.
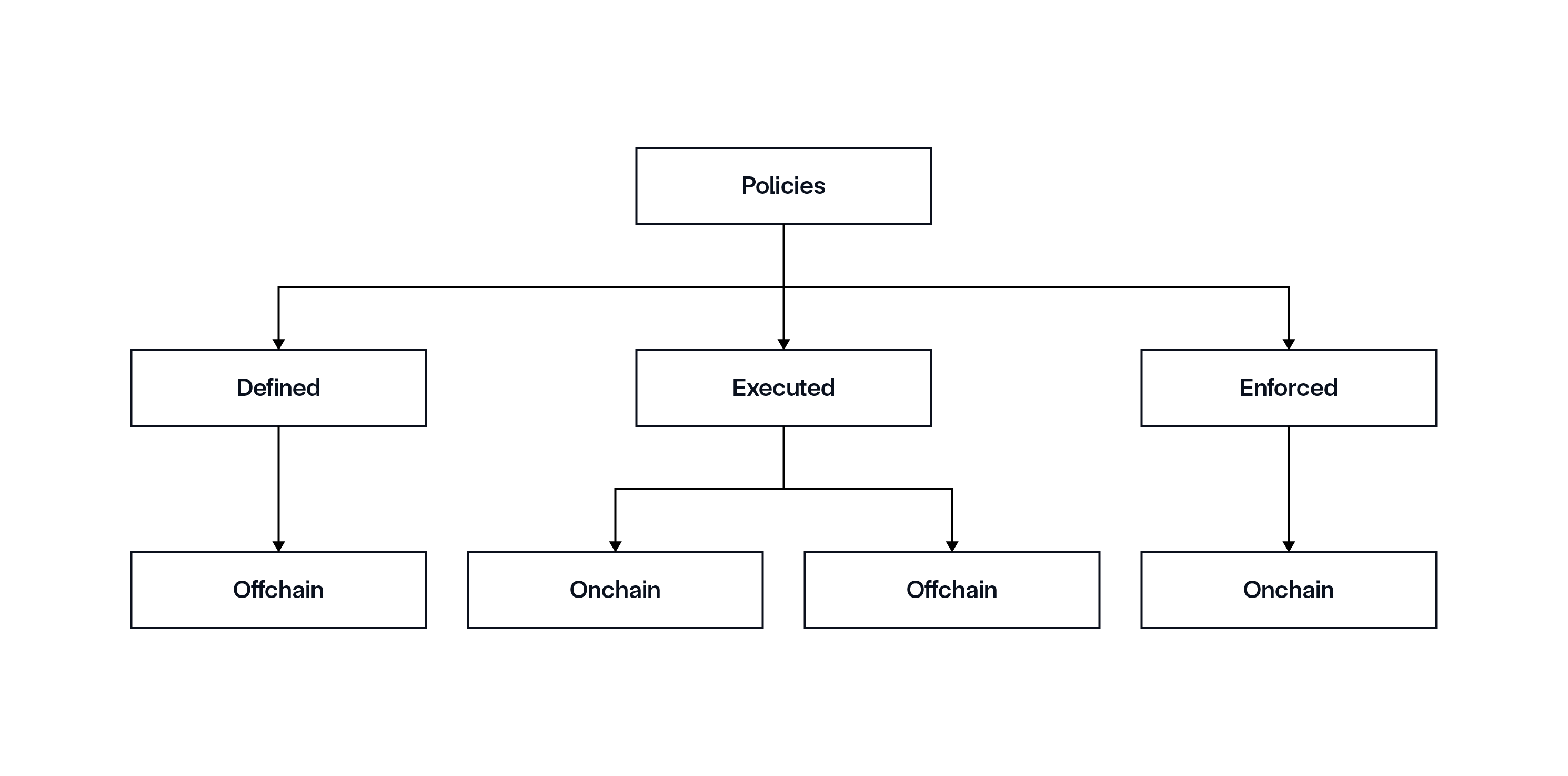
Onchain policy execution offers heightened reliability as it’s embedded directly into smart contracts, fully executed onchain, and independent of any third party. However, onchain execution means policies are executed in a public environment, which may pose concerns for financial institutions that require these policy details to be kept private. Onchain execution also requires onchain data. However, if this data is sensitive data due to regulatory compliance or internal constraints, it may limit access to such data since it cannot always be stored onchain. Furthermore, processing large volumes of data and computation onchain can often be slow and expensive.
While some institutions, asset classes, and policies will require onchain execution and others can only function offchain, a hybrid model in which—depending on the business case—some policies for the same asset are executed onchain while others remain offchain can be useful. However, actual enforcement always remains onchain.
Policy enforcement can be at the asset-level, where it is embedded directly into smart contract logic, ensuring that unauthorized actors cannot access the asset. Policy enforcement can also be at the protocol level, where they are enforced within the smart contracts governing broader transactional or operational workflows (e.g., digital transfer agency (DTA) contracts). These contracts can orchestrate multiple steps across different assets or counterparties, enforcing compliance at key stages of a process rather than solely at the asset itself. If irregularities arise in either method, asset issuers can immediately detect them and take action—whether by modifying requirements or halting all activities until an investigation is completed and compliance rules are updated.
Different types of eligibility requirements and policies can be set up for regulated tokenized assets and transactions, depending on their nature and sensitivity. For example, policies can govern access to digital assets through eligibility checks on accreditation, jurisdiction, and subscription status. Users appearing on sanctions lists, fraud lists, or deny lists can also be restricted from interacting with compliant digital assets. The Policy Manager comes with an extensive library of policy templates. It also allows developers to build fully custom policies (writing them in Solidity) and then make them available in CRE workflows.
Out-of-the-box policies offered for the Policy Manager include:
- Allow/Deny List
- Negative Credentials Checker
- Role-Based Access Control (RBAC)
- Volume Rate Limit
- Time Limit
- Secure Mint
- Pause
- Balance Limit
- Max Total Holders
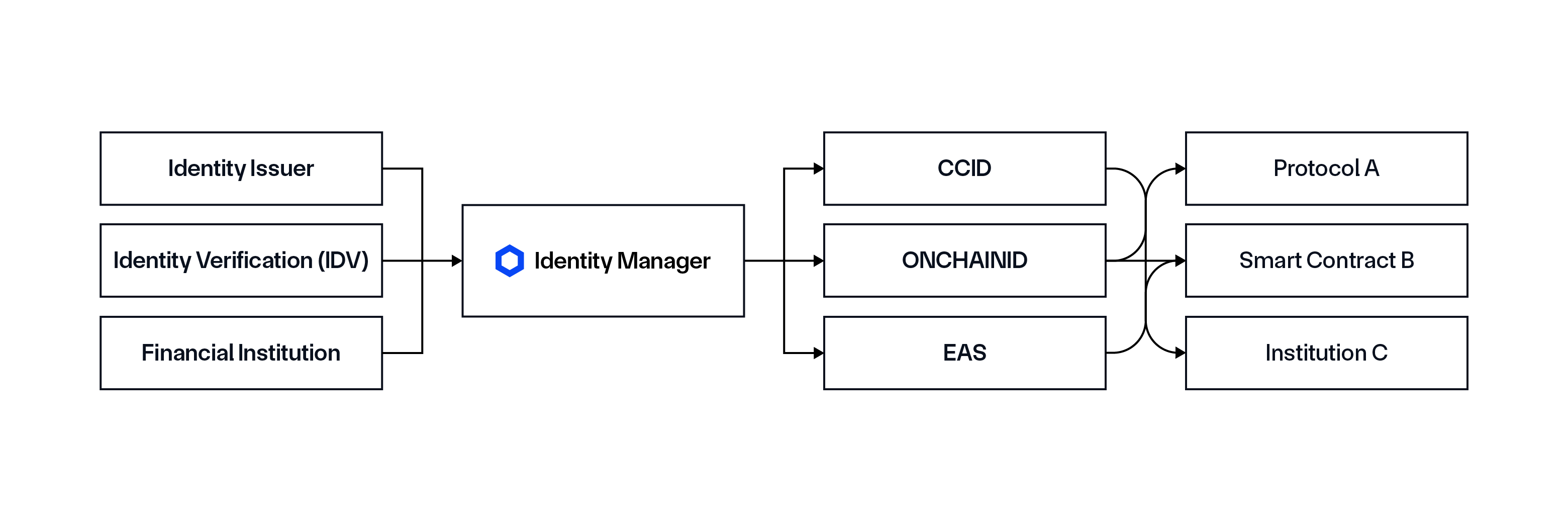
Identity Manager
The Identity Manager is middleware that links real-world identity sources to various onchain formats. The Identity Manager enables the registration, distribution, synchronization, and lifecycle management of identity credentials across networks without storing non-public information (NPI) or personally identifiable information (PII) onchain. It supports multiple onchain formats, including Chainlink’s CCID and other existing standards, such as ONCHAINID, Ethereum Attestation Service (EAS), and others in the future.
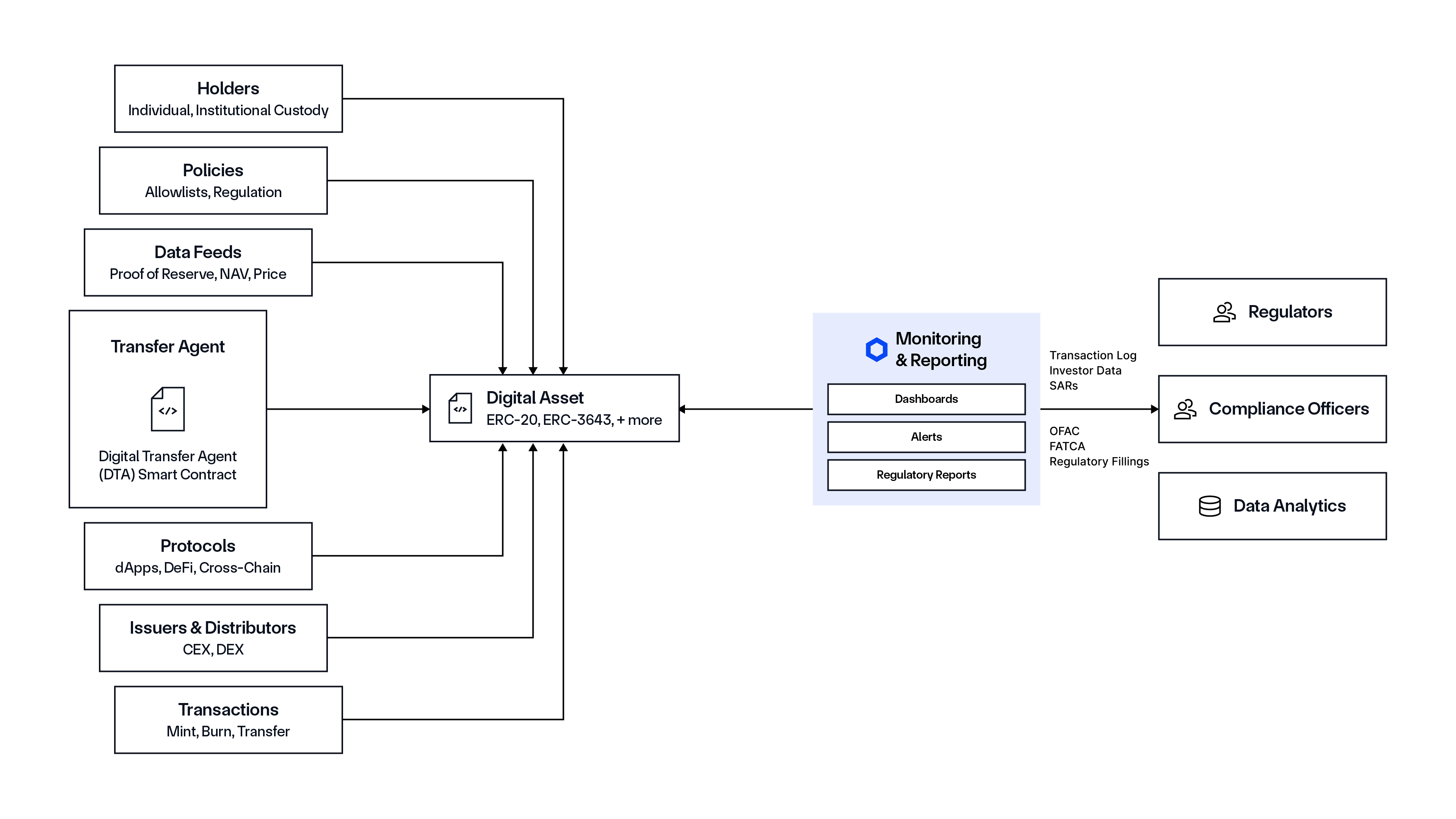
Monitoring and Reporting Manager
The Monitoring and Reporting Manager provides the ability to observe infrastructure, smart contracts, and third-party integrations to detect non-compliance, anomalies, and system failures—facilitating real-time alerts, proactive risk mitigation, and strengthened operational resilience. It also offers extensive reporting capabilities that deliver both technical and procedural evidence to support regulatory compliance, simplifying the asset issuer’s journey of obtaining and maintaining required licenses and approvals.
Some of the features supported include:
- Automated alerts for policy violations or anomalies
- Integration with Security Operations Center (SOC) dashboards and logging tools
- Policy-driven reaction automation (e.g., pause smart contracts, deny transactions)
- SLA/uptime metrics and audit logs for internal reviews.
Once the system is configured and monitored, it will generate and export compliance proof for internal purposes or regulatory requests, such as by maintaining an auditable log of all transactions and providing evidence explaining why each transaction was allowed or denied. However, it should be noted that financial institutions keep control of the reporting, so it’s at their discretion.
Solution Accelerators and Tools
The Automated Compliance Engine comes with several solution accelerators and tools purpose-built for developers, empowering them to launch proof of concepts in weeks rather than months.
- Compliance Sandbox: A sandbox that enables developers to validate the Automated Compliance Engine, giving customers a hands-on way to explore Chainlink’s CCID and Policy Manager.
- Onchain Policy Accelerators: Prebuilt policy modules (e.g., Allow/Deny Lists, Volume Limits, Secure Mint), along with 12 audited and ready-to-use templates for common policies.
- Developer Tooling: A dedicated SDK, API, CLI, and admin UI.

Use Cases Unlocked By Chainlink ACE
Let’s examine a few example workflows to understand how the various Chainlink ACE components and services work together to unlock compliance-focused digital assets and transactions.
Reusable Digital Identities for Digital Finance
Problem: Asset issuers want to issue and operate compliant digital assets and tokenized assets on public blockchain networks while also complying with local and global KYC/AML requirements in a manner that maintains privacy of sensitive information. Currently, there are no standardized mechanisms for exchanging identity information on a blockchain between the asset issuer and digital asset platforms. Each issuer onboards investors from scratch, leading to higher costs.
Solution: Leverage CCID and GLEIF’s vLEI to create a reusable, globally recognized form of digital identity. The Identity Manager adds an additional layer of trust by verifying the data provided by GLEIF before it is recorded onchain. It keeps identity data up to date across various networks and can even facilitate real-time, pre-transaction identity verification before a transaction occurs.
Below are three different trust models that can be applied to reusable identities:
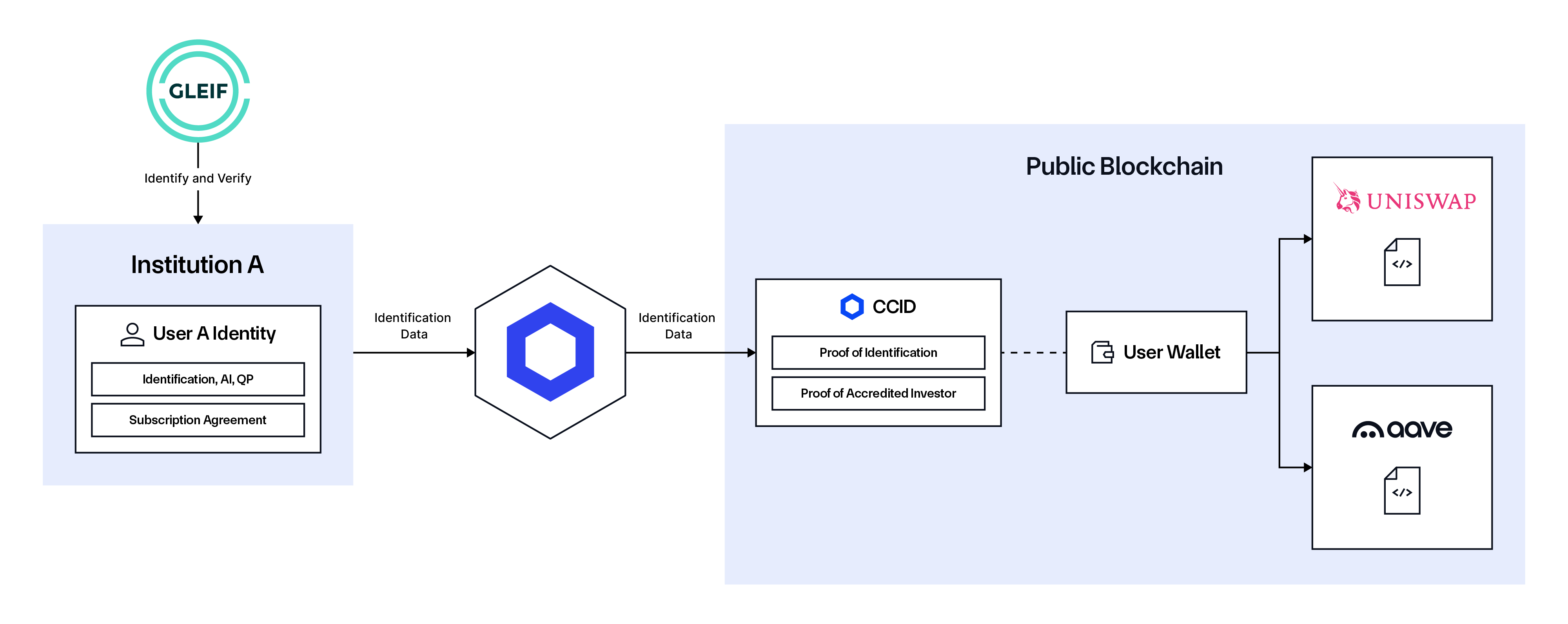
Model 1: Financial institutions rely on identity information from each other. For example, if Institution A trusts Institution B’s verification, Institution A allows investors who have completed KYC with Institution B to operate with their digital assets.

Model 2: An Identity Verification (IDV) solution like Persona becomes a trusted identity issuer, and other institutions rely on their data onchain.
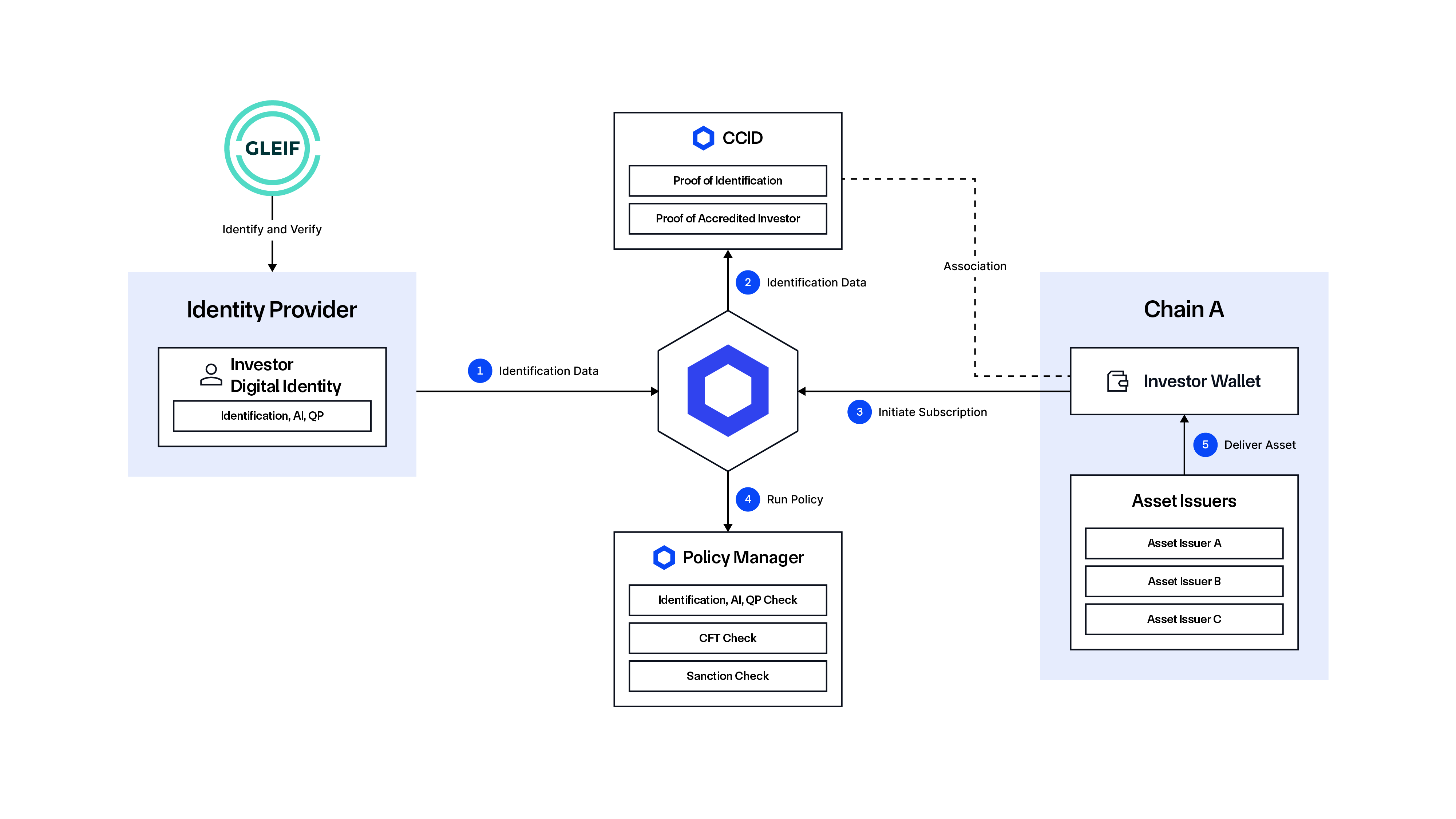
Model 3: A single organization creates digital identities for their employees and customers, and then limits interactions to only between these entities and only with permissioned protocols and financial instruments on public blockchains.
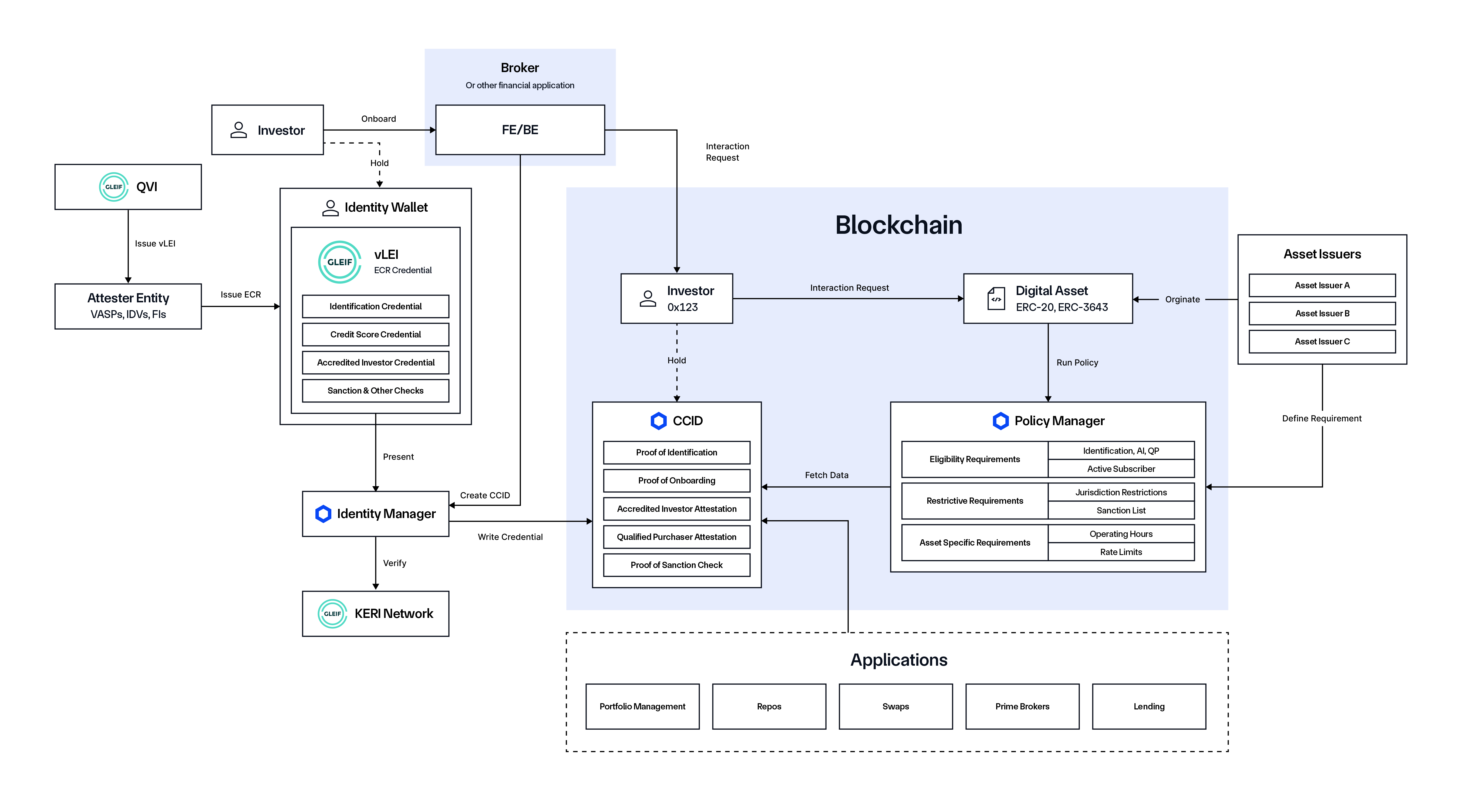
To see how reusable identities—no matter the trust model used—can be leveraged in onchain workflows to support compliance for digital assets, we put together a detailed example workflow below that utilizes GLEIF and various components and services of Chainlink ACE.
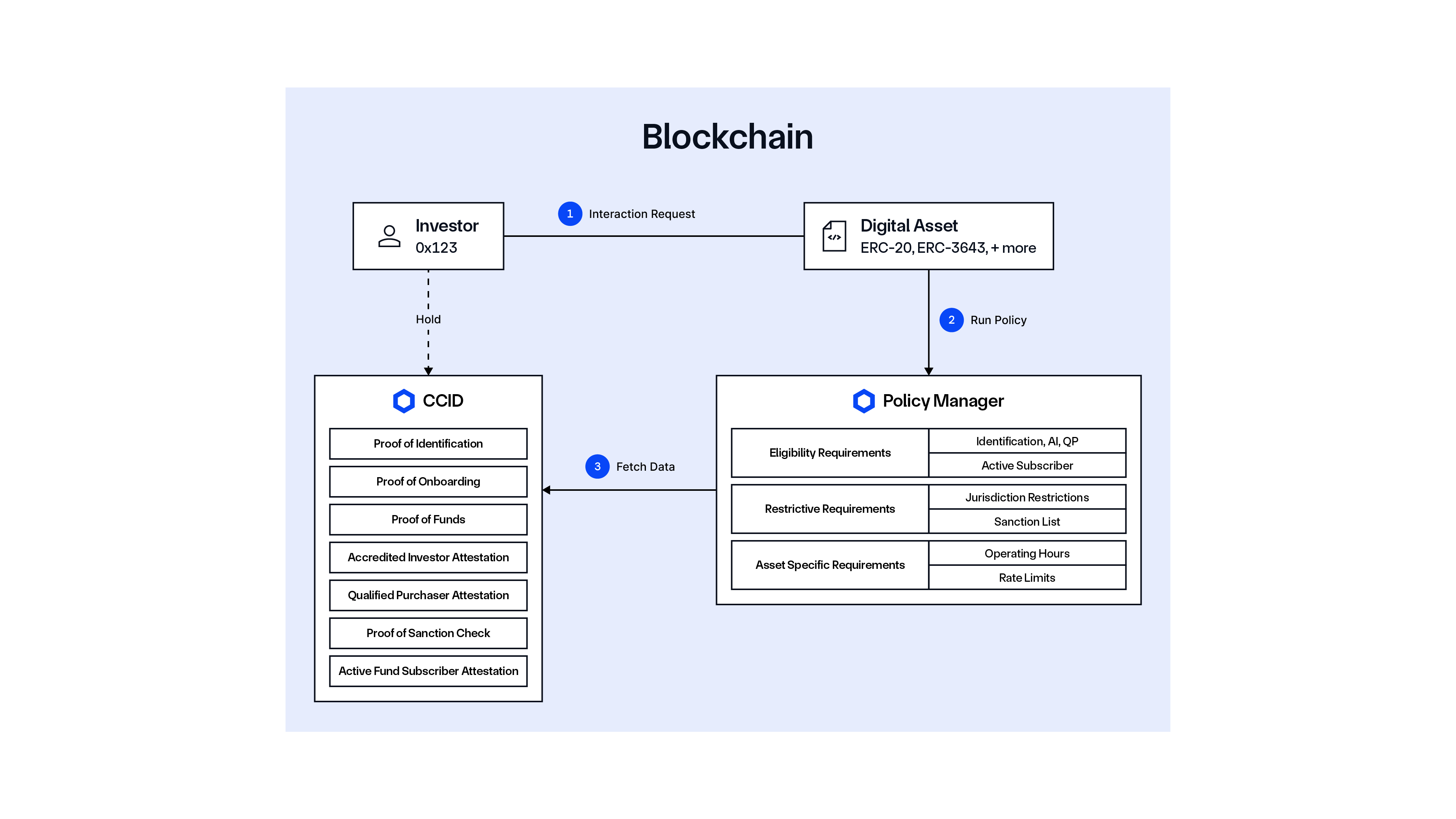
Prior to the process, the Asset Issuer must originate the Digital Asset and define the eligibility requirements for interacting with it.
- A Qualified vLEI Issuer (QVI) issues a vLEI to the Trusted Attester.
- Trusted Attesters—e.g., Virtual Asset Service Providers (VASPs), Identity Verifiers (IDVs)—issue Engagement Context Role (ECR) credentials to the Investor.
- Investor onboards with a Broker (or any application used to interact with the blockchain) and connects their identity wallet, presenting the ECR.
- Broker calls the Identity Manager to verify the vLEI and initiate creation of the CCID.
- Identity Manager reads data from the vLEI.
- Identity Manager verifies the data using the Key Event Receipt Infrastructure (KERI) witness network and parses it.
- Identity Manager writes the verified credentials to the CCID.
- Investor (via the Broker interface) initiates a digital asset subscription process, triggering an onchain interaction request.
- Investor Wallet interacts with the Digital Asset smart contract.
- Digital Asset contract calls the Policy Manager to check transaction eligibility based on predefined requirements.
- Policy Manager fetches data from the CCID and makes an eligibility decision, where the transaction is either approved or rejected by the Policy Manager.
CCIP Compliance-Focused Transactions
Problem: Moving regulated assets between public and private blockchains, DeFi protocols, and platforms is challenging due to the need to reliably verify and maintain holder identity at any stage of the asset lifecycle.
Solution: Combine Chainlink ACE with Chainlink’s Cross-Chain Interoperability Protocol (CCIP), which is the global standard for moving data and value across blockchains. Combining these Chainlink standards for cross-chain and compliance enables regulated tokenized assets to be brought onto public chains under tightly defined constraints, such as for their use as a settlement token for a wide range of onchain workflows.
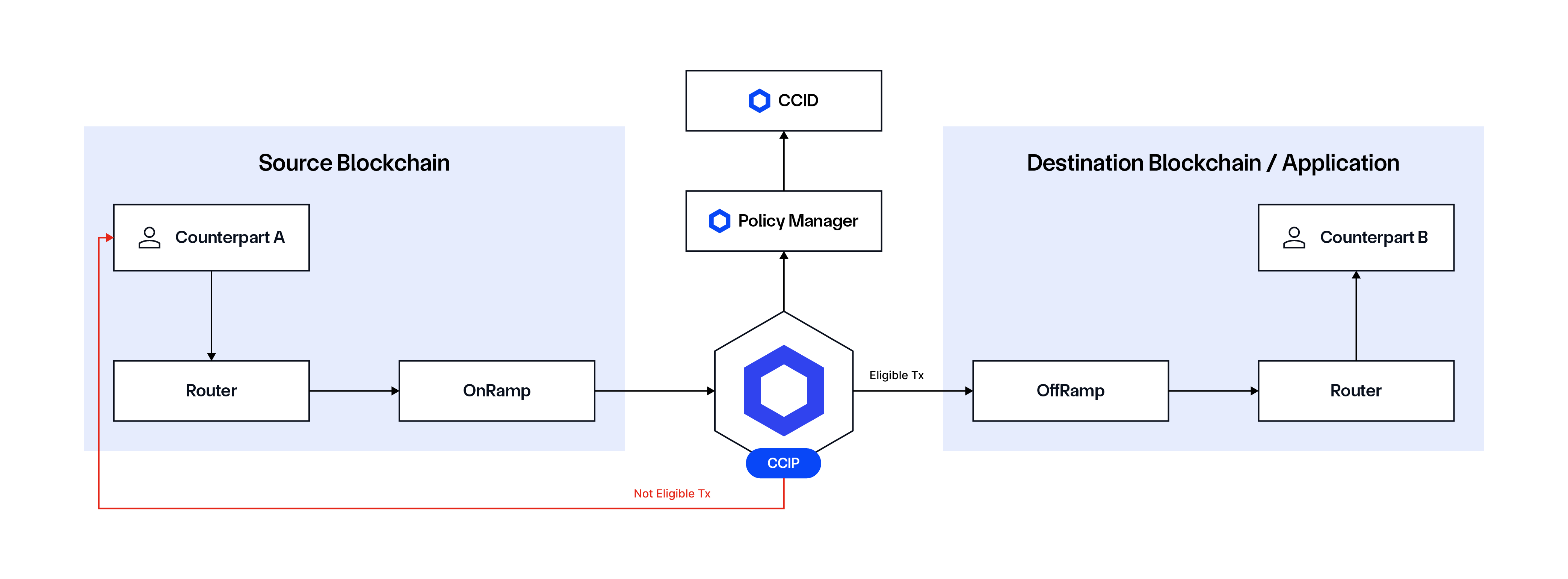
Compliance-focused Tokenized Fund Subscription DvP
Problem: The subscription process for tokenized funds often requires that asset issuers validate investors’ identities, verify their eligibility, and enforce compliance with jurisdictional and investment-specific rules. Asset issuers may also need to enforce these compliance requirements within complex cross-chain transactions. For example, in a Delivery versus Payment (DvP) scenario, payments must be executed on one network while asset delivery occurs on another, necessitating cross-chain policy and identity checks. On the other side, investors want the flexibility to move their assets across different networks as needed without relying on third parties to authorize every transaction.
Solution: Use CCID to link offchain credentials (e.g., identification, onboarding, accredited investor check) to CCIDs for seamless onchain validation while leveraging the Policy Manager to enforce subscription policies (e.g., jurisdictional restrictions, investment limits). Developers can also leverage the Data Link extension to integrate external data feeds (e.g., NAV, Proof of Reserve, and sanctions lists) into subscription workflows for real-time compliance. Combined, these can make tokenized funds more secure, scalable, and efficient by streamlining the subscription process.
Additionally, developers can employ the Policy Manager to define policy structures and enforce policies onchain while the Identity Manager is used to maintain identity information for system participants. CCIP can verify policies on both the source and destination chains, determining transaction eligibility before execution. Once configured, the system operates 24/7 without relying on third parties, with all compliance enforcement happening at the blockchain layer.
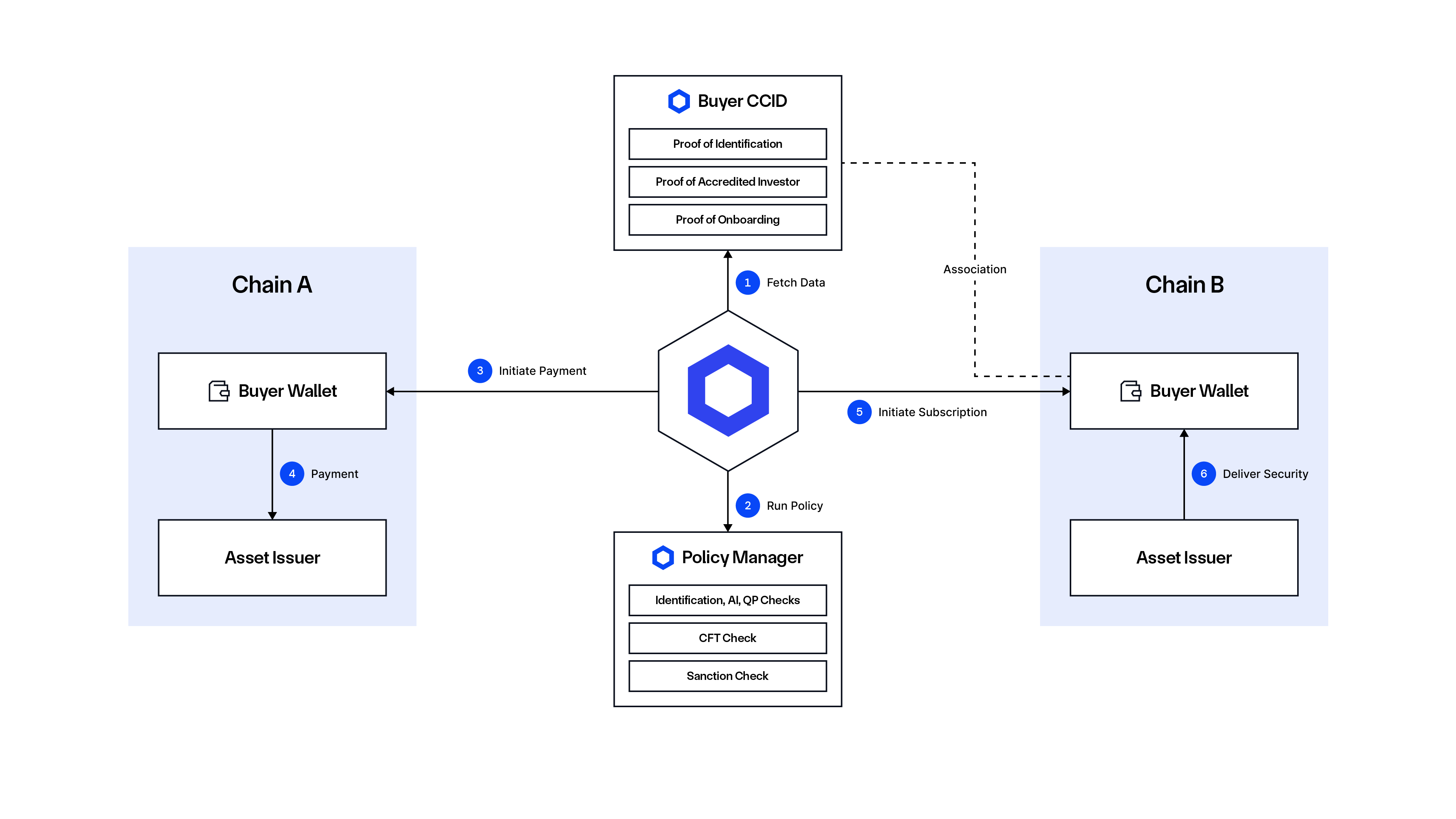
Workflow:
Prior to the process, the Asset Issuer defines the eligibility requirements for interacting with the tokenized fund.
- Buyer’s KYC data and public wallet address are fetched by the Policy Manager.
- The Buyer’s identity information is verified within the Policy Manager—AML, CFT, and sanctions checks are performed using the partner’s ecosystem. The Eligibility Allowlist is retrieved from the Asset Issuer.
- Policy Manager verifies the transaction against predefined compliance rules, such as eligibility, sanctions, jurisdictional limits, and transaction rate limits.
- Upon successful verification, the Buyer’s payment to the Asset Issuer on Chain A is processed securely and compliantly.
- The Asset Issuer on Chain B delivers the purchased asset to the Buyer’s compliant wallet address, completing the regulated transaction.
Pre-Transaction Eligibility Allowlists & Advanced Checks
Problem: Asset issuers and distributors, market makers, and exchanges want to create and distribute digital assets on public networks while complying with local and global regulations. However, they lack standardized mechanisms and controls to prove compliance to regulators. As a result, they resort to geo-blocking, permissioned protocols, and manual, expensive, error-prone processes.
Digital asset transactions face unique challenges, particularly when it comes to restricting access to authorized users or entities based on specific compliance or eligibility requirements. Traditional systems often lack the flexibility to enforce granular permissions onchain dynamically, creating risks of unauthorized access, non-compliance with regulatory standards, and inefficiencies in manually managing access controls. There are also data compliance challenges, such as integrating and managing external compliance data sources (e.g., jurisdictional restrictions or denylist registries) dynamically within smart contracts.
Solution: Chainlink ACE improves onchain financial instruments by providing a more secure, scalable, and efficient way to manage permissioned access. It achieves this by leveraging:
- Cross-Chain Identity: Enables the creation of identity registries that link onchain identities (via CCIDs) to offchain credentials, such as KYC/AML, accredited investor, or active fund subscriber status.
- Policy Enforcement: Allows for granular, real-time enforcement of eligibility requirements for accessing tokenized assets or smart contract methods
- Granular Permissioning Mechanisms: Smart contract functions can be restricted by dynamically enforced policies, such as allowlists, denylists, and jurisdiction-based restrictions, so only authorized users can interact with them.
- Offchain Verification With CCIDs: Participants’ credentials are verified offchain by trusted entities and securely mapped to CCIDs, which are then validated onchain for compliance.
There are two ways this can work. The simple option is by referencing an allowlist of eligible wallets.
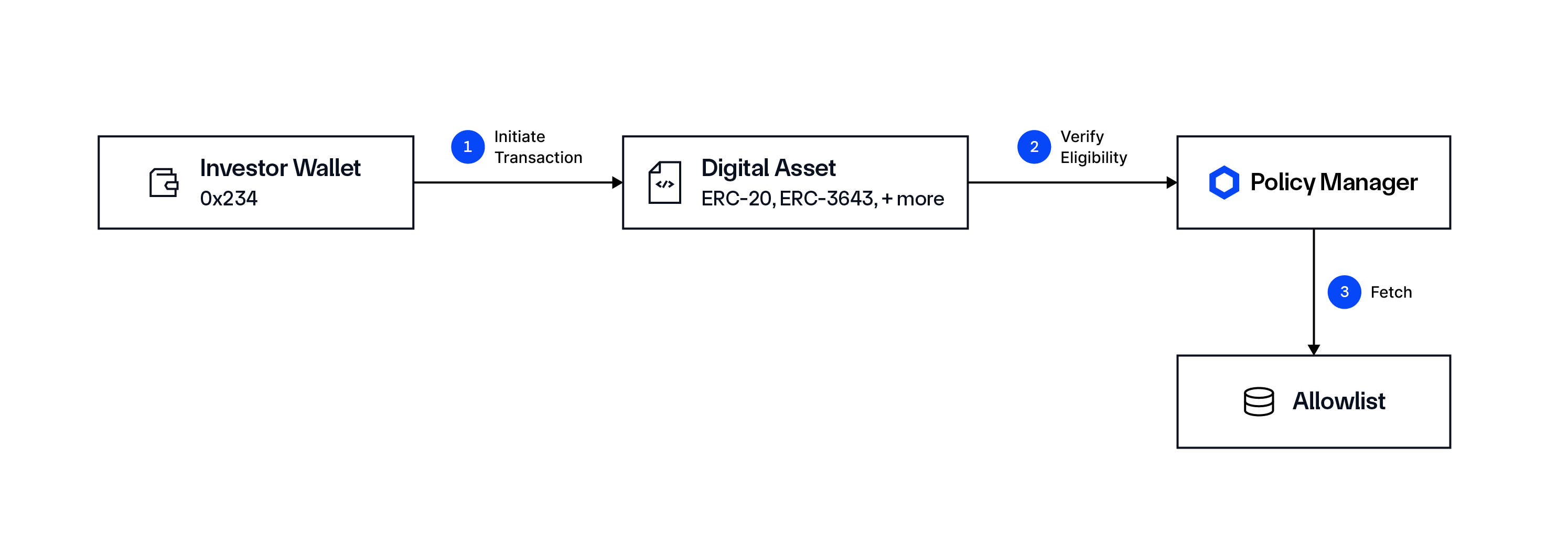
The more advanced option is checking the transaction initiator wallet for a valid identification, CFT, sanctions, jurisdictional, and/or accreditation prior to allowing the transaction. These allowlist policies can be embedded into the digital asset itself or applied on top of the protocol that wants to stay compliant.

Regulated Liquidity and Lending Pools for Institutional DeFi
Problem: Financial institutions (such as brokers) want to provide their customers access to DeFi protocols—including decentralized exchanges, lending and derivatives platforms, and cross-chain bridges—with assets originally acquired through their platforms. To achieve this, they must:
- Securely bridge regulated assets to public (often permissionless) blockchain networks.
- Ensure these tokenized assets remain fully composable and interoperable within the broader DeFi ecosystem.
- Guarantee user access is restricted based on verified identity profiles, attestations, and eligibility criteria.
Simultaneously, institutions must adhere to internal/external policies and regulatory requirements, particularly around onboarding procedures, KYC, AML, and sanctions compliance. This complex compliance landscape often leads institutions to limit asset interactions exclusively to approved and trusted DeFi protocols and platforms, maintain segregated liquidity pools that are restricted to verified institutional users, and only allow institutional users to transact amongst verified peers.
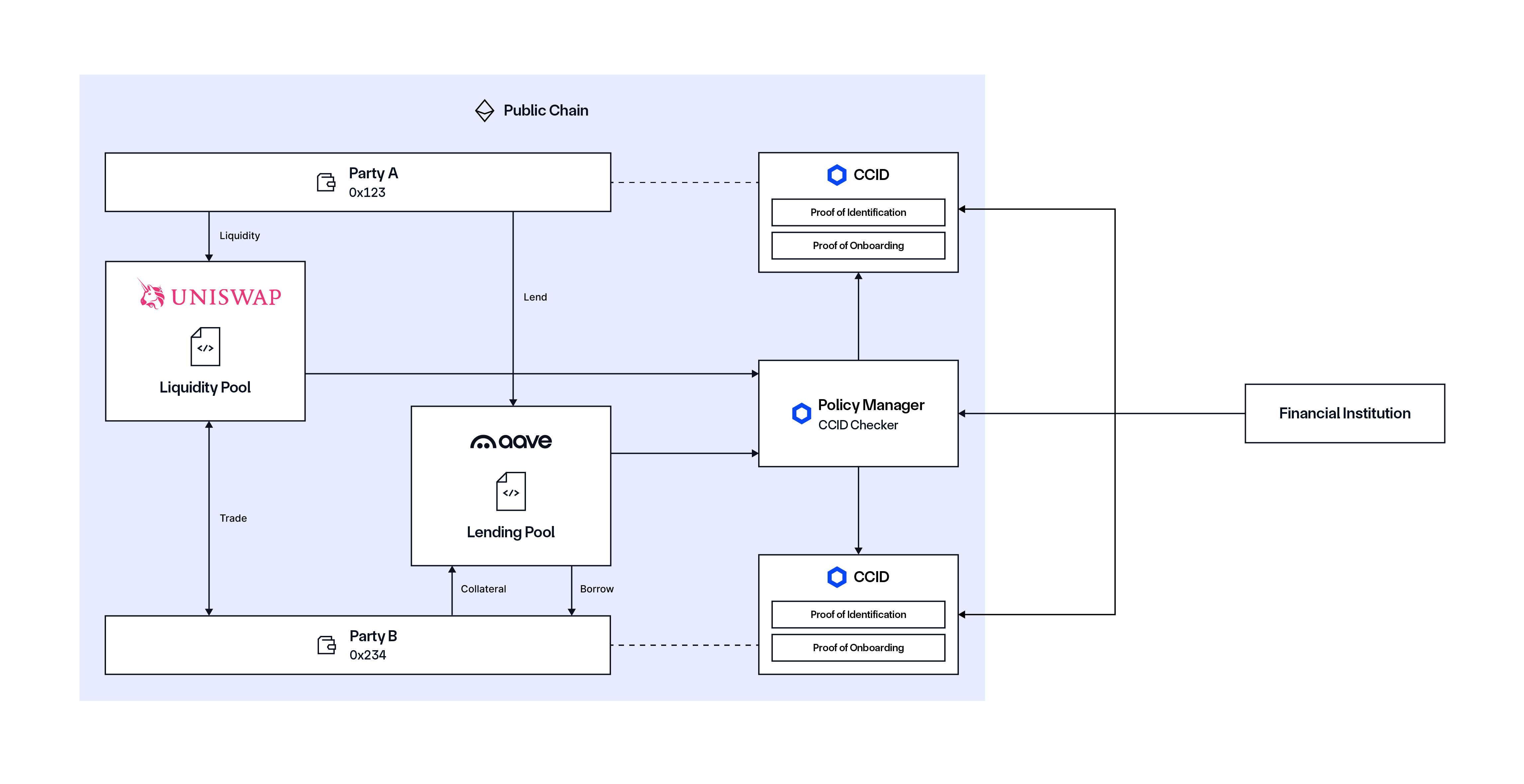
Solution: Chainlink ACE addresses these challenges through two core components. CCID enables institutions to uniquely identify and authenticate their users within the organizational context on public networks. It also allows them to issue verifiable, reusable credentials linked to individual user identities, ensuring streamlined, privacy-preserving compliance checks. Then, the Policy Manager can be used to enforce rules to ensure regulated assets can only be transacted within predefined institutional boundaries. It can also be used to verify user identity credentials and ensure eligibility for each transaction, as well as to protect access to specific DeFi protocols by automatically enforcing institutional policies and regulatory rules, effectively preventing unauthorized asset movements and non-compliant interactions.
This compliance framework provides robust protection, ensuring institutional users access only authorized DeFi services. The diagram below illustrates the regulated transaction flow for lending platforms and DEXs, highlighting how this structured compliance mechanism can safeguard DeFi interactions.
A Compliance Solution For All Stakeholders in Digital Asset Transactions
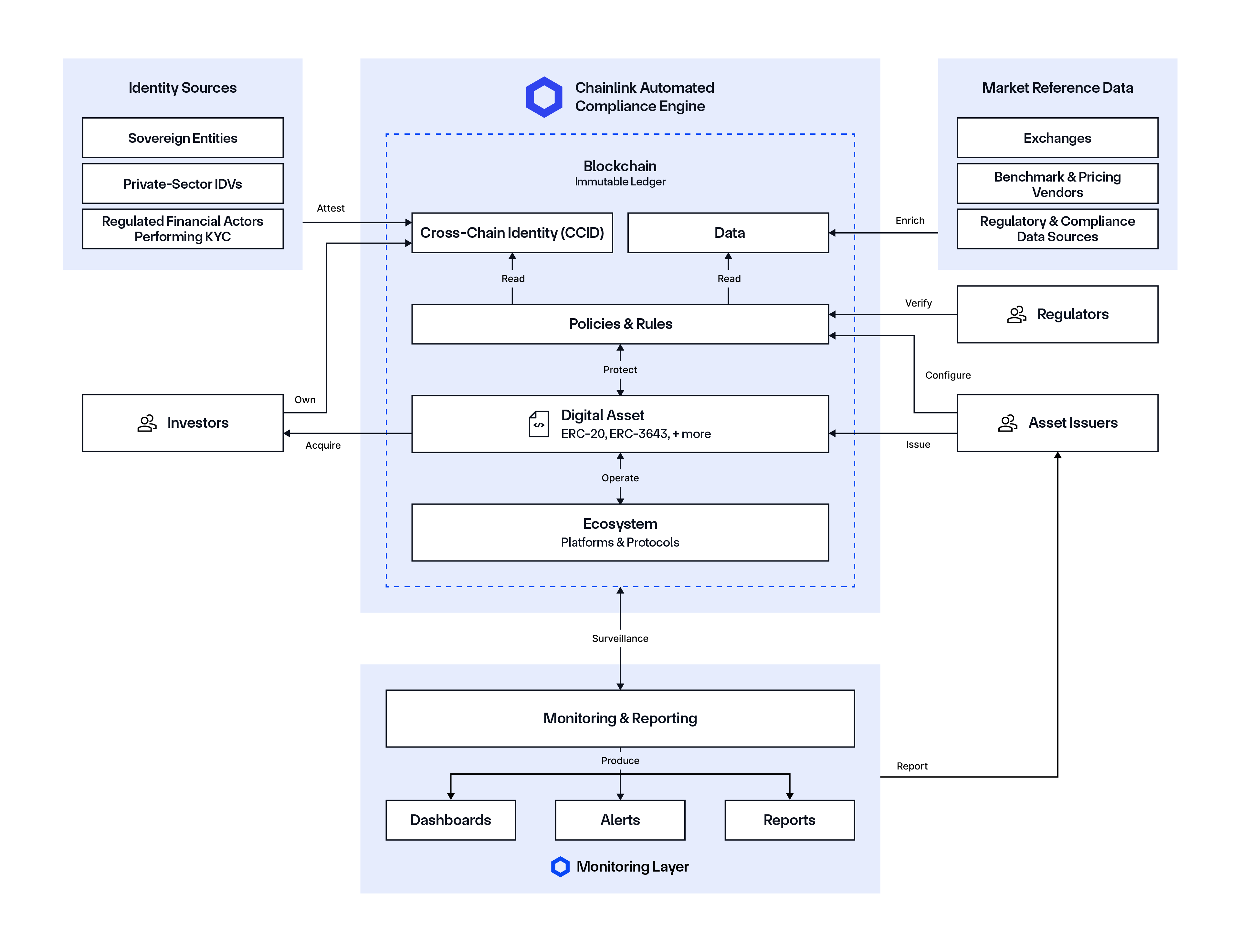
Whether it’s financial institutions, financial market infrastructure, DeFi protocols, data and identity providers, regulators, and more, Chainlink ACE empowers you to build compliance workflows for digital assets and transactions. It’s agnostic to the different blockchains, token standards, and offchain data and systems that can be utilized, while also providing you with the fine-grained control to implement specific policies for each transaction.
If you want an early preview or to start building with Chainlink ACE, reach out to us.
To learn more about Chainlink, visit chain.link, subscribe to the Chainlink newsletter, follow Chainlink on Twitter and YouTube, and follow Chainlink Labs on LinkedIn.
—
Disclaimer: This post is for informational purposes only and contains statements about the future, including anticipated product features, development, and timelines for the rollout of these features. These statements are only predictions and reflect current beliefs and expectations with respect to future events; they are based on assumptions and are subject to risk, uncertainties, and changes at any time. There can be no assurance that actual results will not differ materially from those expressed in these statements, although we believe them to be based on reasonable assumptions. All statements are valid only as of the date first posted. These statements may not reflect future developments due to user feedback or later events, and we may not update this post in response. Please review the Chainlink Terms of Service, which provides important information and disclosures.
