Why Does Your Automation Infrastructure Need To Be Decentralized, Not Just Distributed?
Automating low-level maintenance tasks enables projects to focus their developer resources on enriching their applications with additional features that drive growth. When choosing an automation solution, it’s important to recognize the costs of homegrown solutions and the various risks associated with centralized, distributed, and bounty-based anti-patterns. As a decentralized alternative, teams can integrate Chainlink Automation for hyper-reliable, cost-efficient, and secure automation.
Homegrown Solutions
Regardless of whichever design pattern a homegrown solution employs, having to build and maintain a custom automation solution brings its own costs and risks.
Time-Consuming
Setting up and running a homegrown automation solution is a lot more difficult and time-consuming than most think. For example, if you’re building an automation solution with Web2 technologies like cloud-based job schedulers or a cron job smart contract, you’ll need to check every block for transactions, listen for events, account for reorgs in the chain, send alerts when token balances get low, and much more. Not to mention that you’ll also need to handle Remote Procedure Call (RPC) unresponsiveness, which can be especially challenging for multi-chain applications. Additionally, multi-chain applications may require separate automation architecture for each chain the application is deployed on.
Lack of Economies of Scale
Setting up a homegrown automation solution can be costly when done for a single application, especially when it’s responsible for protecting user value and requires specialized resources and deep expertise. The high cost can ultimately make applications uncompetitive compared to competitors employing more efficient automation solutions.
The Anti-Patterns: Centralized, Distributed, and Public Bounties
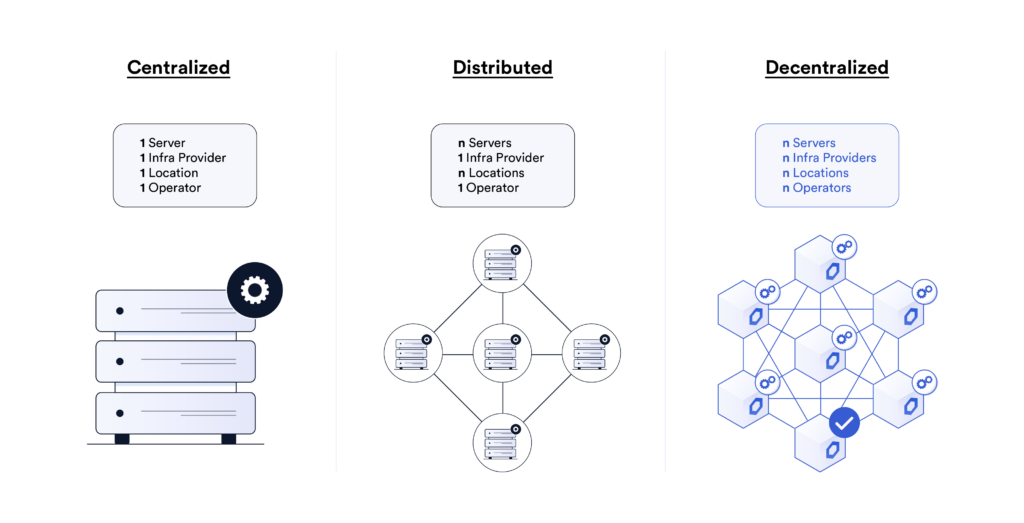
Centralized: Costs and Risks
Private Keys Exposed
Securing private keys is mission-critical for smart contract developers. However, when initiating transactions from centralized services, developers risk exposing their private keys. As blockchains ensure that only the private key holder can access funds stored at the corresponding blockchain address, this presents a major risk to the security of a protocol treasury.
Single Point of Failure
Centralized solutions that automate smart contract functions introduce a single point of failure that makes protocols vulnerable to manipulation and technical failures. Whether these centralized automation solutions rely on scripts running on centralized servers or DevOps teams manually monitoring conditions and calling on-chain contracts, these practices introduce a central point of failure that can lead to protocol insolvency, trade slippage, and the loss of user funds.
Distributed: Costs and Risks
False Assumptions
Distributed systems have proven to be especially dangerous to applications and their users because they can result in false assumptions about the security, reliability, and decentralization of their protocol. When inevitable outages do occur, these can create significant financial and reputational losses for affected projects.
Outages
Beyond security concerns, inconsistent uptime remains a constant concern for DevOps teams that rely on distributed solutions. For example, distributed solutions often rely on cloud providers that have gone offline repeatedly, which results in downtime for many dApps. These outages are much more common than many realize and impact even the most reputable cloud providers. There were 15,000 cloud outage events in 2022 alone, according to ThousandEyes, a Cisco network intelligence company.
Public Bounties: Costs and Risks
An alternative to centralized and distributed automation systems is to integrate autonomous execution directly into the protocol by offering bounties, a financial reward allotted to the first automation bot to call an on-chain function when certain conditions are met.
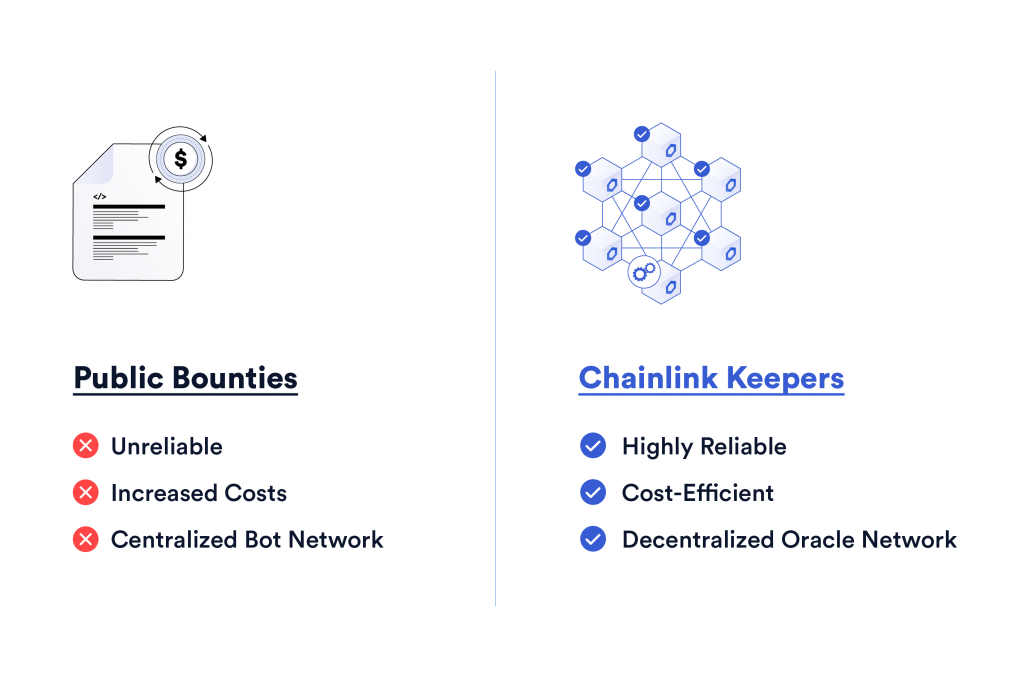
Unreliable
Balancing the bounty incentive structure is especially challenging for developers. If you set the bounty too low then it’ll never get called, but if you set it too high you can damage your protocol. Public bounties don’t provide protocols with any assurances or commitments that the automation bots will operate consistently, especially when they’re needed most. When there’s extreme market volatility or network congestion, automation bots may fail to operate to avoid paying high gas prices or run out of funds—it’s possible your transactions will not be executed at all.
Increased Costs
Another issue with the approach of offering autonomous bounties is that it increases the running costs of the protocol. dApps pay the bounties (i.e. rewards) from their revenues to whoever calls the function first. This cost then grows as automation bots end up in a winner-takes-all competition and drive priority gas auction (PGA) bidding wars. As automation bots raise the gas price they’re willing to pay in order to get miners to process their transactions first and win the bounty, the overall cost increases, as most jobs include a base cost plus gas fee. Ultimately these costs fall on end-users, who have to cover the higher fees.
Centralized Bot Network
Over time, competition for public bounties can lead to centralization as well-capitalized actors submit aggressive prices for extended periods, drive away the competition, and corner the market. As fewer automation bots monitor and submit transactions, the reliability available to dApps can diminish dramatically.
Anti-Pattern Consequences
Relying on centralized/distributed solutions or public bounties that are prone to various issues is highly risky for applications that secure value on behalf of users. This is a risk at all times and can be significantly greater in the midst of a bull market.
Financial Loss and Reputational Damage
When applications have gone down due to unplanned infrastructure outages, financial losses for protocols and their users have occurred, with funds being unrecoverable. For example, the failure to trigger liquidations on a DeFi platform can leave them with undercollateralized loans that lead to insolvency and a loss of user funds. Financial losses lead to reputational damage, which has seen users permanently leave platforms for more reliable alternatives.
Operations Impact
Recovering from unplanned downtime creates a whole host of problems. An all-hands developer war room and immediate special actions are often required to help mitigate the damage. Following immediate actions, redesigning the protocol and integrating more reliable solutions is usually required to prevent future issues, which can be both time-consuming and costly.
Decentralized Alternative: Why Developers Choose Chainlink Automation
Chainlink Automation enables developers to unlock a wide array of use cases thanks to smart contract automation while offering several advantages over the above alternatives.
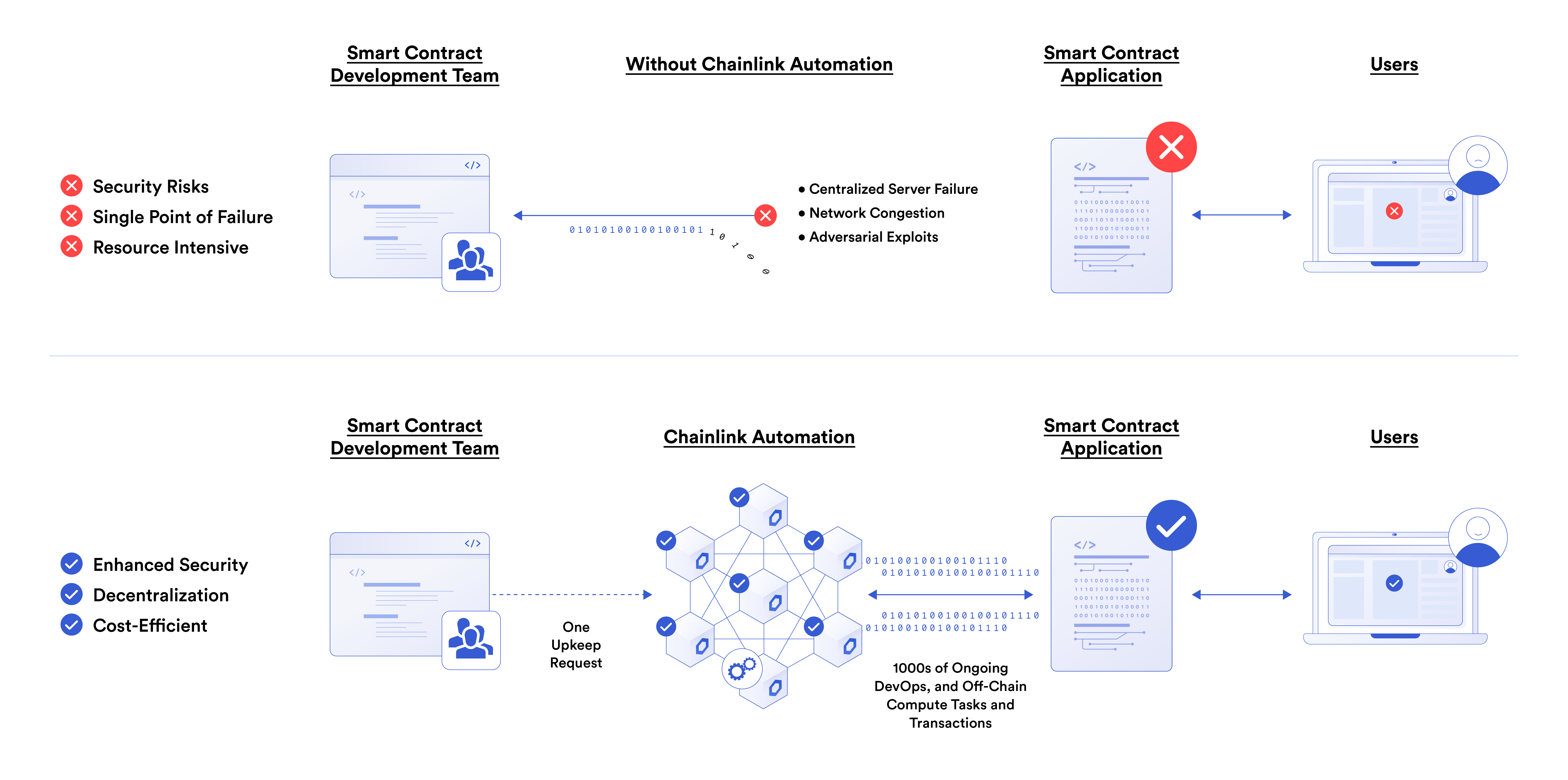
Enhanced Security
Chainlink nodes perform upkeeps in a trust-minimized manner, giving developers and users confidence that their smart contracts will be executed exactly as intended without the possibility of manipulation by any outside entity. By using decentralized infrastructure, Automation helps ensure that user-defined service agreements are enforced on-chain.
As nodes sign on-chain transactions themselves, automated execution is possible without exposing private keys at any point. This enhances the security of the entire protocol as it removes one of the major risks of centralized automation solutions.
Decentralization—No Single Point of Failure
Automation uses Chainlink’s decentralized oracle network to perform upkeeps, meaning developers can rely on the same Sybil-resistant, tamper-proof nodes that are already responsible for helping secure tens of billions of dollars across DeFi. With multiple Automation nodes per chain and a rotating node selection process providing added redundancy, Automation will continue to remain completely decentralized.
Increased Efficiency
Chainlink Automation has several gas-optimizing features, including a rotating node selection process, which helps prevent PGA bidding wars and lowers the cost for end-users. Automation also saves DevOps teams hundreds of hours of work and increases the efficiency of projects. By simply plugging into Chainlink Automation infrastructure with an Automation-compatible contract and registering an upkeep, developers can rest assured their contract will continue executing when predefined conditions are met. This ultimately leaves more resources available for developing and growing their protocol.
Reliability and Long-Term Sustainability
Chainlink Automation continues to provide decentralized automation in periods of extreme network congestion and high gas prices, and are not subject to the centralized infrastructure outages that see centralized solutions fail. Even when networks are volatile, Automation continues to successfully trigger liquidations and help maintain the solvency of protocols, and provide reliable support for many other use cases.
Full Technical Support
Chainlink provides full technical support for applications integrating Chainlink Automation. Consult with a world-class team of smart contract developers and security experts who will help you integrate Automation into your app.
To integrate Automation into your dApp, email [email protected] or visit the Automation docs for more information.
