What Is a Sybil Attack?
Named after the protagonist of the 1973 book Sybil, which recounts the story of a young woman diagnosed with Disassociative Identity Disorder (DID), the concept of a Sybil attack was first defined by Microsoft researchers Biran Zill and John R. Douceur in the early 2000s.
In a Sybil attack, a single entity directly or indirectly controls a significant number of network nodes. The goal is to trick honest network participants into believing each node is a distinct and separate participant, when in reality a significant number of nodes are dishonestly controlled by a single attacker.
Understanding Sybil Attacks
Sybil attacks aim to exploit and manipulate peer-to-peer networks—often open and decentralized blockchain networks—through multiple fake identities. In the context of Sybil attacks, “identities” can refer to a blockchain node, a social media account, a pseudoanonymous wallet address, or any other entity.
A successfully executed Sybil attack requires creating and controlling a large number of pseudoanonymous entities to influence the network in a malicious manner. For blockchains, this can result in a 51% attack or transaction censorship. In a social media network, Sybil attacks can be used to disseminate misinformation and create a false sense of community consensus.
There are two main types of Sybil attacks:
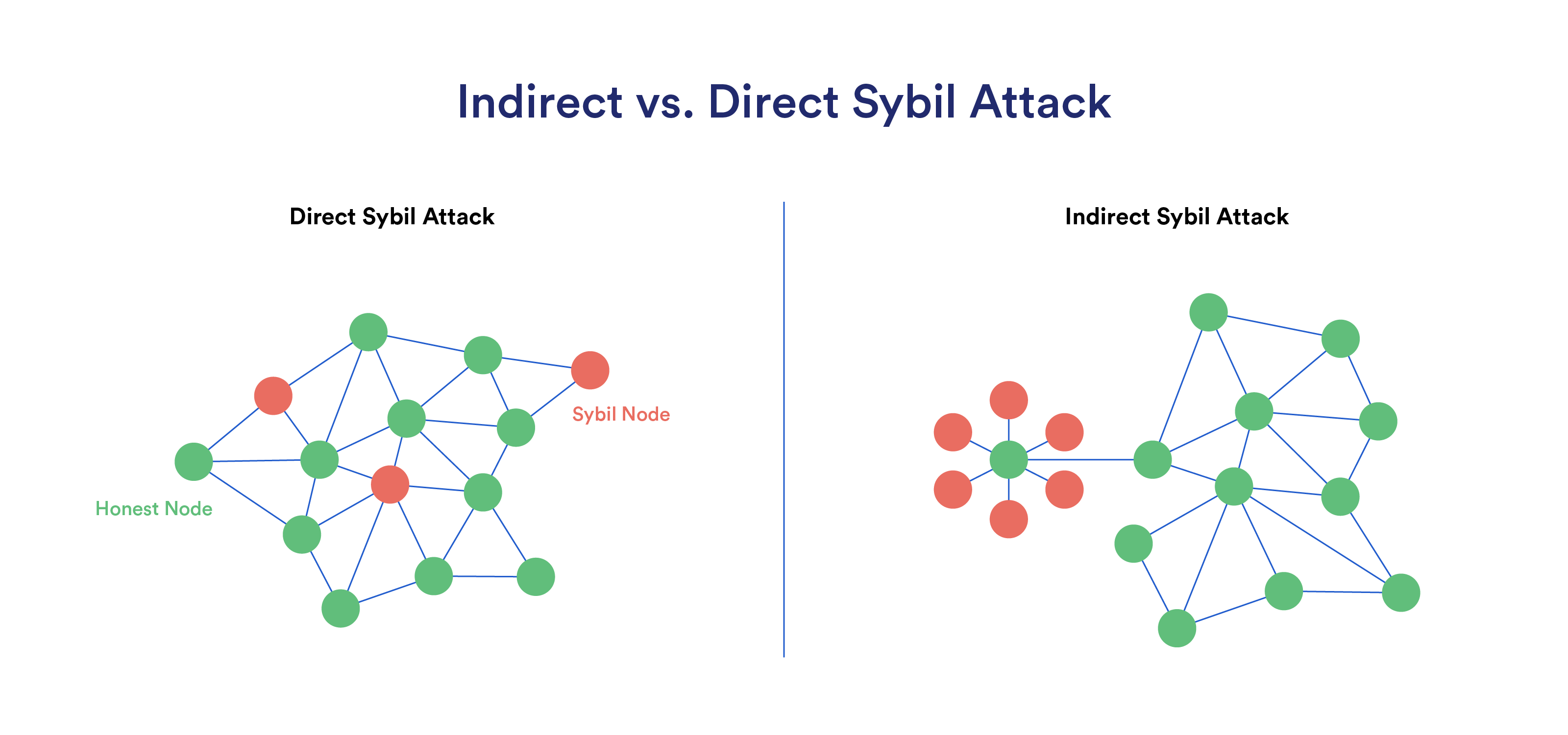
- Direct Sybil Attacks: Malicious nodes influence the network by directly communicating with honest nodes to take control of decision-making processes, voting procedures, or consensus mechanisms.
- Indirect Sybil Attacks: Malicious nodes or participants do not directly interact with honest nodes, but instead aim to silently leverage malicious nodes to artificially increase the reputation of particular nodes, alter a network’s topology, or isolate certain parts of the network.
Vulnerabilities to Sybil Attacks
Sybil attacks are most relevant to networks defined by pseudoanonymous participation. Social media networks, blockchain networks, and other peer-to-peer networks are all vulnerable to Sybil attacks because pseudoanonymity is a feature—it is purposefully simple to operate multiple entities in the network.
Blockchain networks are particularly targeted for Sybil attacks because they represent high-value targets for attackers. If a Sybil attack is successfully performed, it often leads to the direct loss of user funds. In contrast, a successful Sybil attack on a social media network often results in the spread of targeted misinformation, false societal consensus, and user privacy breaches.
Examples of Sybil Attacks on Blockchain Networks
The dangers of Sybil attacks on blockchain networks are well documented, but poor security features have, and likely will continue to, lead to successful onchain Sybil attacks.
Some prominent examples of Sybil attacks on blockchain networks include:
Ethereum Classic
Ethereum Classic is a fork of the Ethereum blockchain that emerged in 2016 after the infamous Ethereum DAO hack. In August 2020, the Ethereum Classic blockchain was repeatedly struck by a 51% attack—a specific form of Sybil attack unique to blockchain networks—that resulted in multiple block reorganizations and millions in stolen funds.
Verge
Verge is a privacy-preserving blockchain network that uses a proof-of-work consensus mechanism similar to the Bitcoin Network. In 2021, the Verge blockchain experienced its third 51% attack, which resulted in a major block reorganization that rewrote more than 200 days of network transactions.
Sybil Attack Prevention and Defense Mechanisms
Sybil attacks represent an interesting phenomenon for blockchain networks. While Sybil attacks are uniquely dangerous for blockchains (high-value target, pseudoanonymous participation), blockchains are also purpose-built to be resilient against them.
Cryptoeconomic Security
One of the main innovations of the Bitcoin network, and the blockchain ecosystem at large, was the creation of cryptoeconomic security. Whether in a proof-of-work or proof-of-stake mechanism, requiring network participants to give proof of computational work or economic stake makes it economically or technically impractical for a single entity to directly control a majority of nodes, hashrate, or stake.
Reputation Systems
Another countermeasure against Sybil attacks is to build reputation systems directly into the network. For example, delegated proof-of-stake networks rely on a group of known and reputable, but potentially pseudoanonymous, entities to perform the major functions of a blockchain. This limits, and often completely removes, the ability for a Sybil attacker to join and influence the network as multiple entities.
Similarly, reputation systems that record a node’s trustworthiness based on its history and contributions make it difficult for a Sybil attacker to masquerade as multiple entities because the attacker must maintain and build up reputation and influence across many nodes over time.
Identity Verification
All Sybil attacks depend on semi-permissionless and pseudoanonymous access to a network. The reason that the vast majority of networks don’t need to worry about Sybil attacks is because they are permissioned and participants are known.
Thus, a very effective, but often unviable, protection mechanism against Sybil attacks for peer-to-peer networks is to validate node identities before they enter the network. While this doesn’t work for public blockchain networks that have been specifically designed to be permissionless while staying tamper-proof against Sybil attacks, it is nonetheless an incredibly effective defense against any form of Sybil attack—and may be used in the future alongside decentralized, privacy-preserving identity protocols.
Conclusion
Sybil attacks are an ever-present threat to blockchain networks, but their architecture and impact are well-known and well-documented in the cybersecurity space. In fact, a core, net-new innovation of public blockchain networks is their ability to stay resilient against Sybil attacks while still maintaining an open and permissionless design.
As blockchain technology and decentralized, peer-to-peer systems continue to evolve, so too will the strategies needed to defend against Sybil attacks, from new forms of digital identities to tailored consensus mechanisms. And that’s just one facet of protection in a sprawling ecosystem of not only blockchain networks but applications and other forms of mission-critical onchain infrastructure.
Learn more about the various forms of cyberattacks and the technologies that prevent them:
