The Builder’s Guide to Proof of Reserve for Wrapped Tokens
Driven by the demand for a more holistic Web3 user experience, cross-chain bridges are used to transfer digital assets from one blockchain network to another through wrapped tokens—one-to-one digital representations of tokens from another blockchain. They’re needed because blockchains are generally not interoperable by default. Wrapped tokens unlock cross-chain liquidity, but often require additional trust assumptions compared to assets native to a single blockchain.
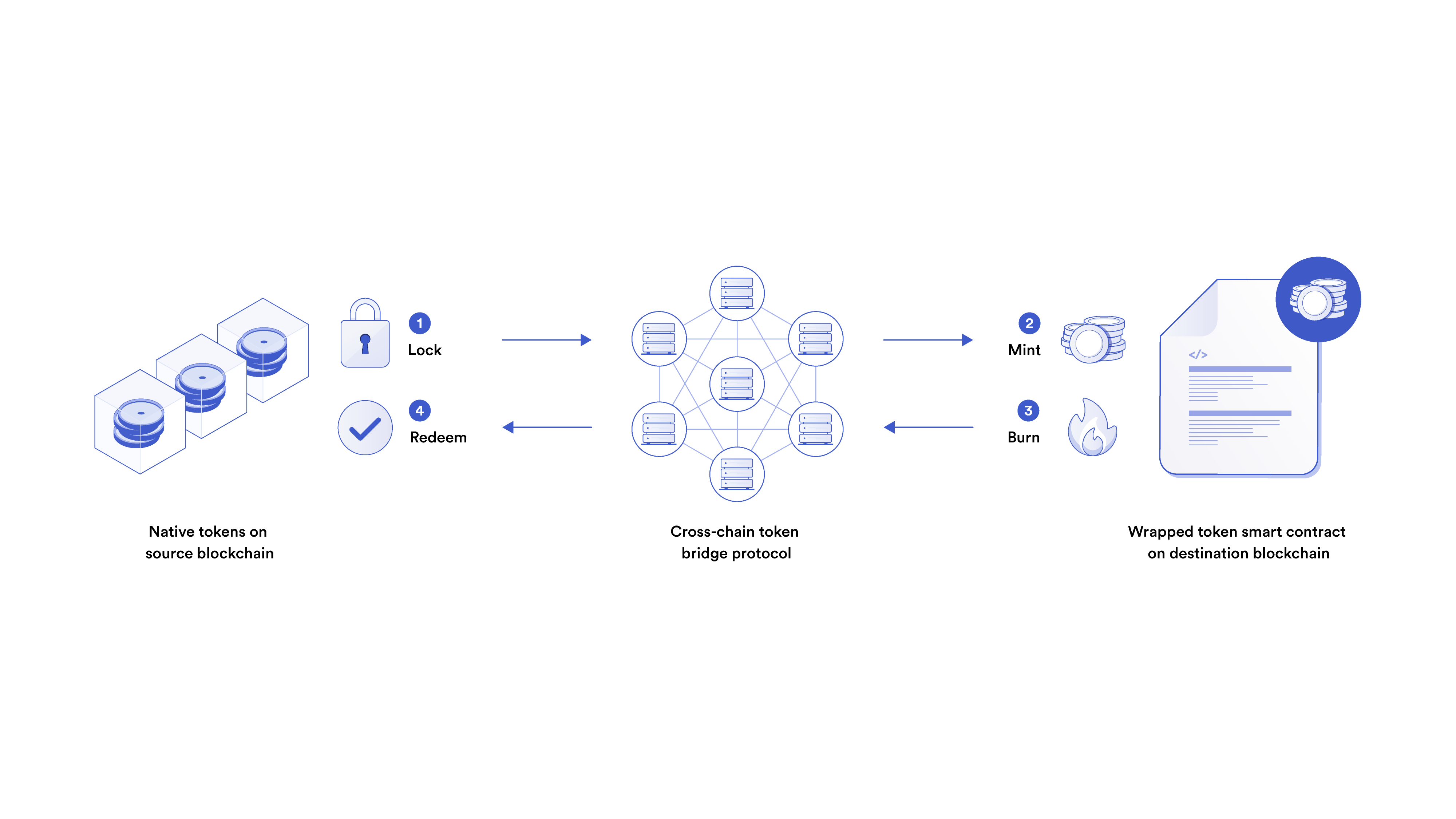
The Complexities of Cross-Chain Bridge Security
Cross-chain token bridges face an array of security challenges, from securing private keys to ensuring airtight smart contract code. Developers must take a comprehensive defense-in-depth approach to cross-chain bridge architecture, with independent layers of security at every step, from technical to social.
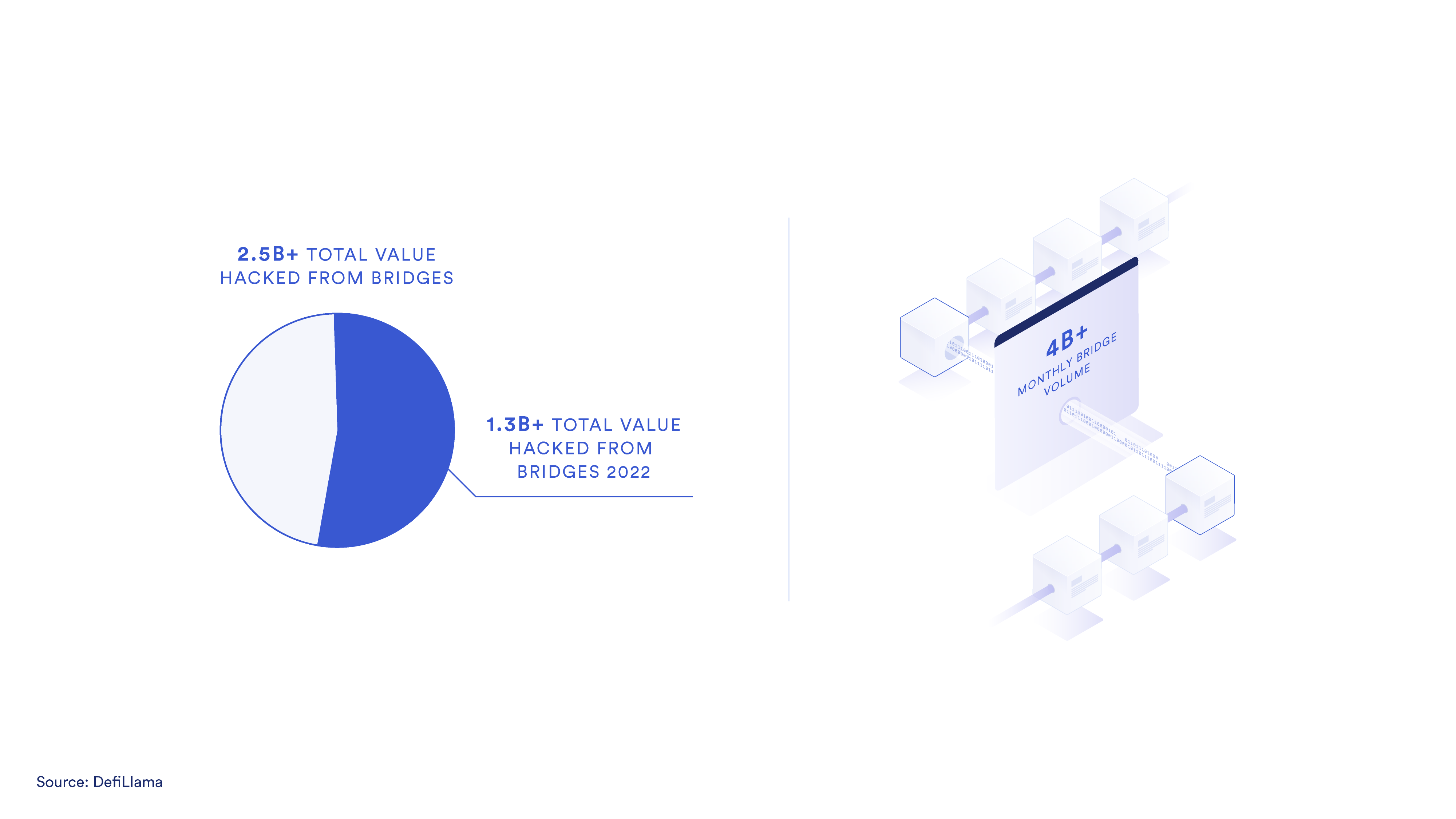
Cross-chain bridge security shouldn’t just be reactive; it should proactively account for the possibilities of an attack or exploit and protect against the potential outcomes. The key question is: What do you do when a carefully laid security plan goes awry?
Exploit and Attack Risks
Regardless of how a bridge is compromised, there are often two immediate risks that come from bridge attacks and exploits.
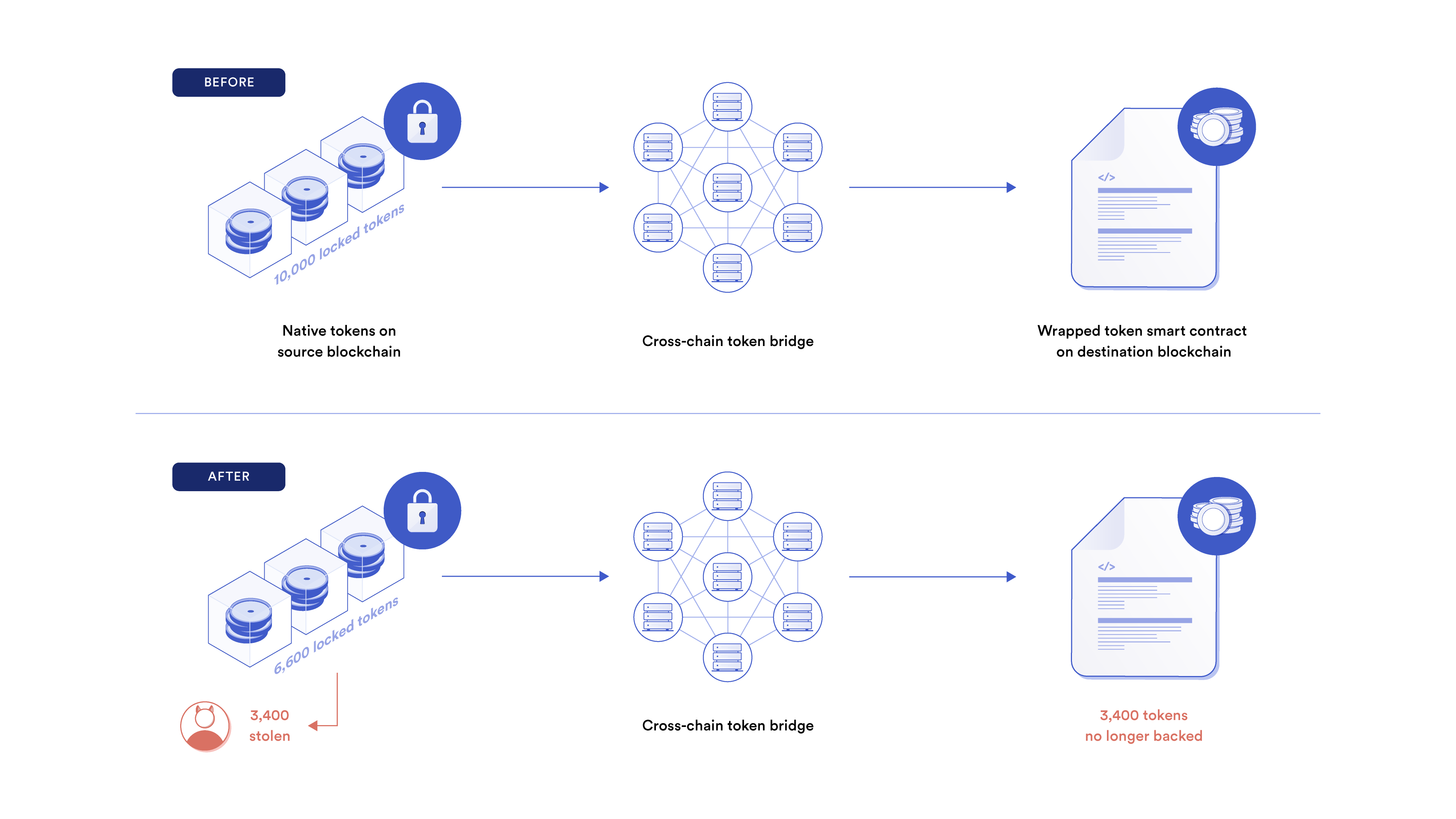
1. Collateral on the source chain is withdrawn without correct ownership.
User funds on the source blockchain are stolen and corresponding wrapped tokens are no longer fully backed. Because wrapped assets only hold value due to their cross-chain backing, stealing locked assets on the source blockchain effectively makes corresponding wrapped assets worthless.
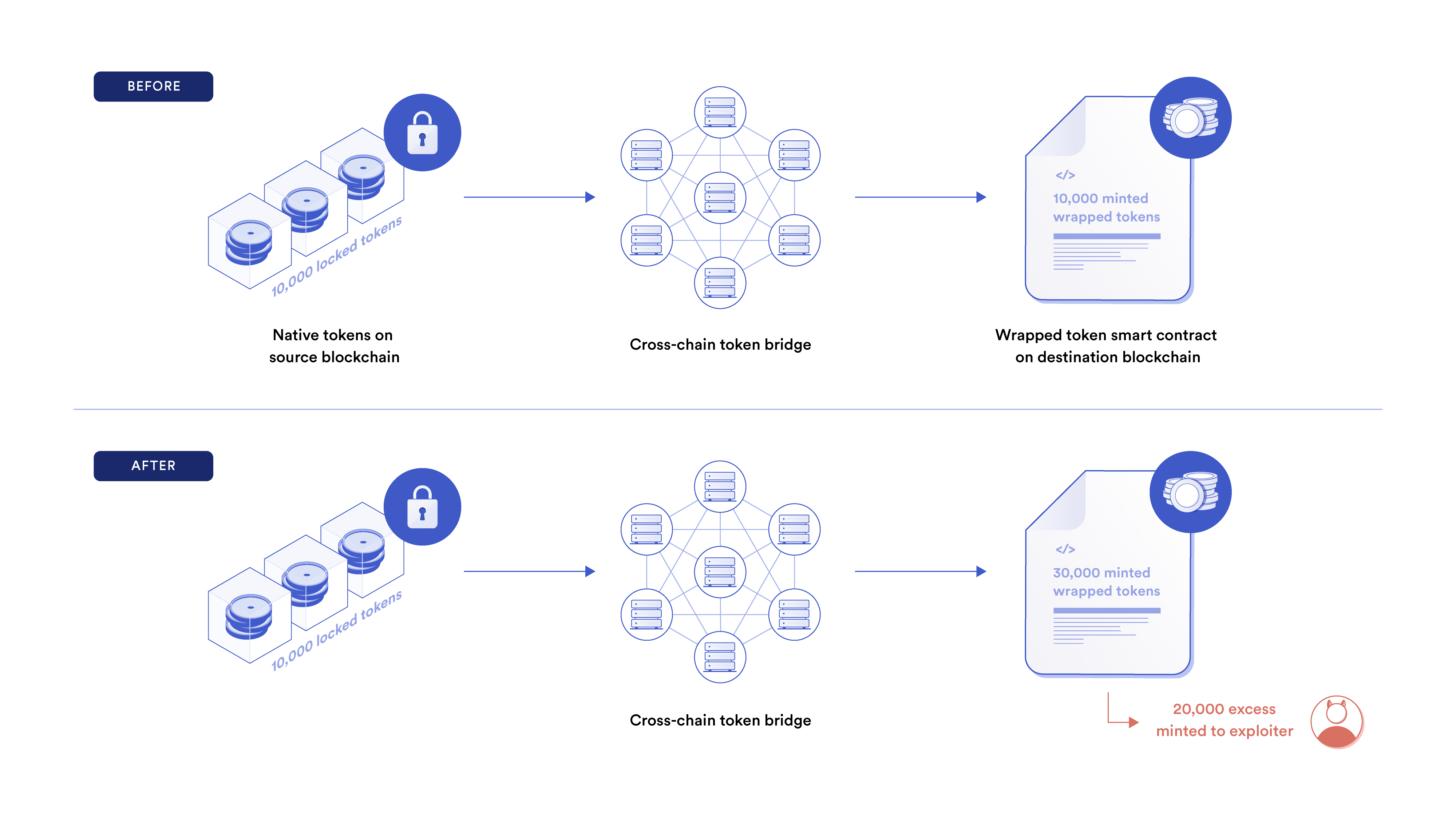
2. Cross-chain tokens on the destination chain are minted without sufficient collateral.
Known as an “infinite mint” exploit, this is when an excess of wrapped tokens without sufficient reserves are minted, meaning they are no longer sufficiently collateralized. Infinite mint exploits lead to fractional reserve practices, and malicious actors can take advantage of this by either selling the wrapped token assets on a decentralized exchange or using the tokens as collateral on a lending market.
Ecosystem Risk
A compromised cross-chain token bridge poses an immediate risk not only to bridge users but also to any project that directly integrates support for the wrapped token. Wrapped tokens are often used within DeFi protocols, and an exploit or hack can significantly impact operations and sometimes lead to protocol insolvency.
For example, using wrapped tokens as collateral within a pooled DeFi lending market can put users at risk, even if they only lend or borrow network-native assets. If a wrapped token used as collateral is exploited, it can result in the loss of lender (or protocol) funds, leading to insolvencies that can not only impact users, but cause ripple effects across the wider ecosystem.
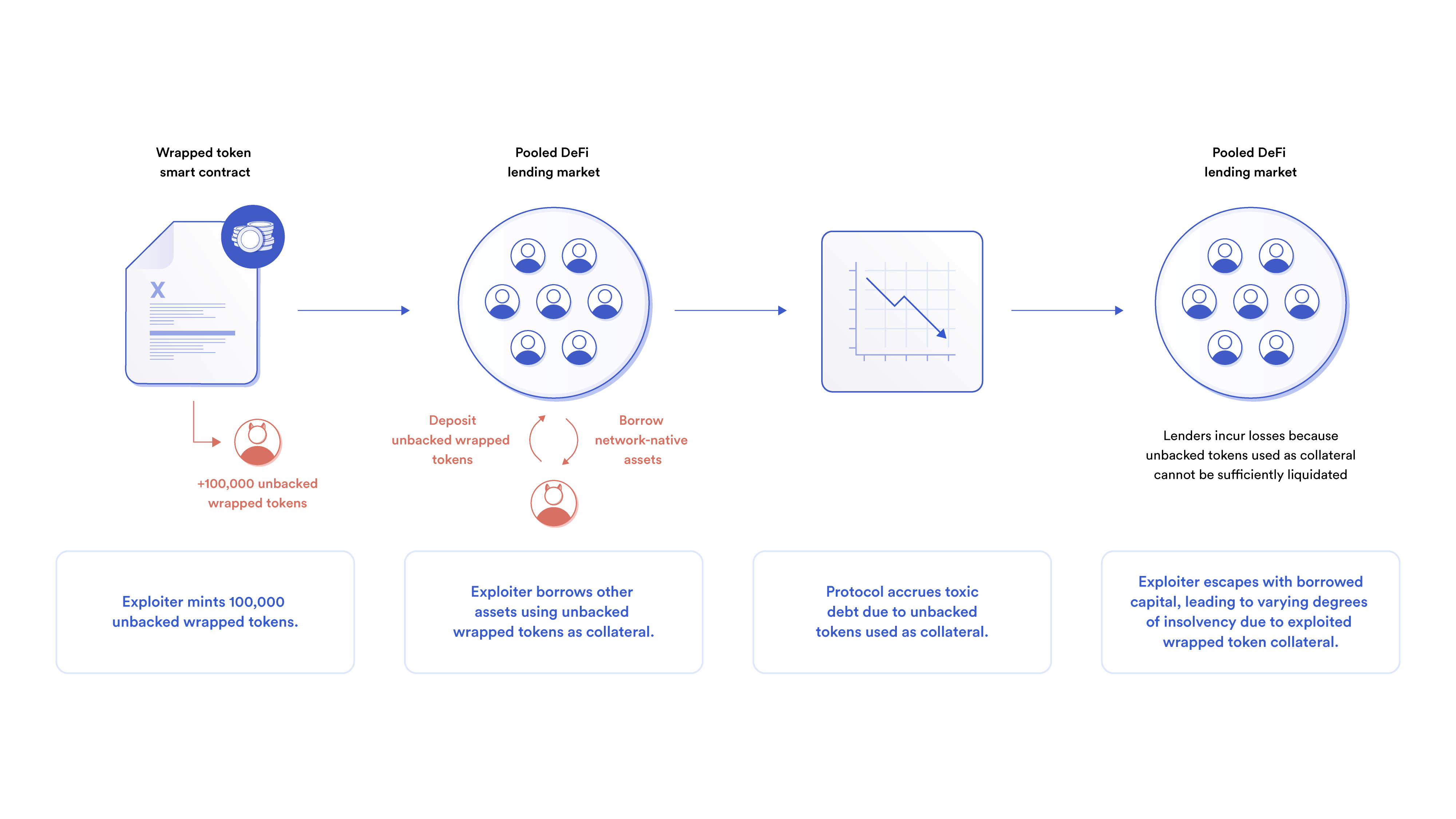
As cross-chain token bridges and their wrapped tokens gain adoption, the ecosystem risk, if a bridge’s security is compromised, grows.
How Chainlink Proof of Reserve Helps Supercharge Wrapped Token Transparency and Security
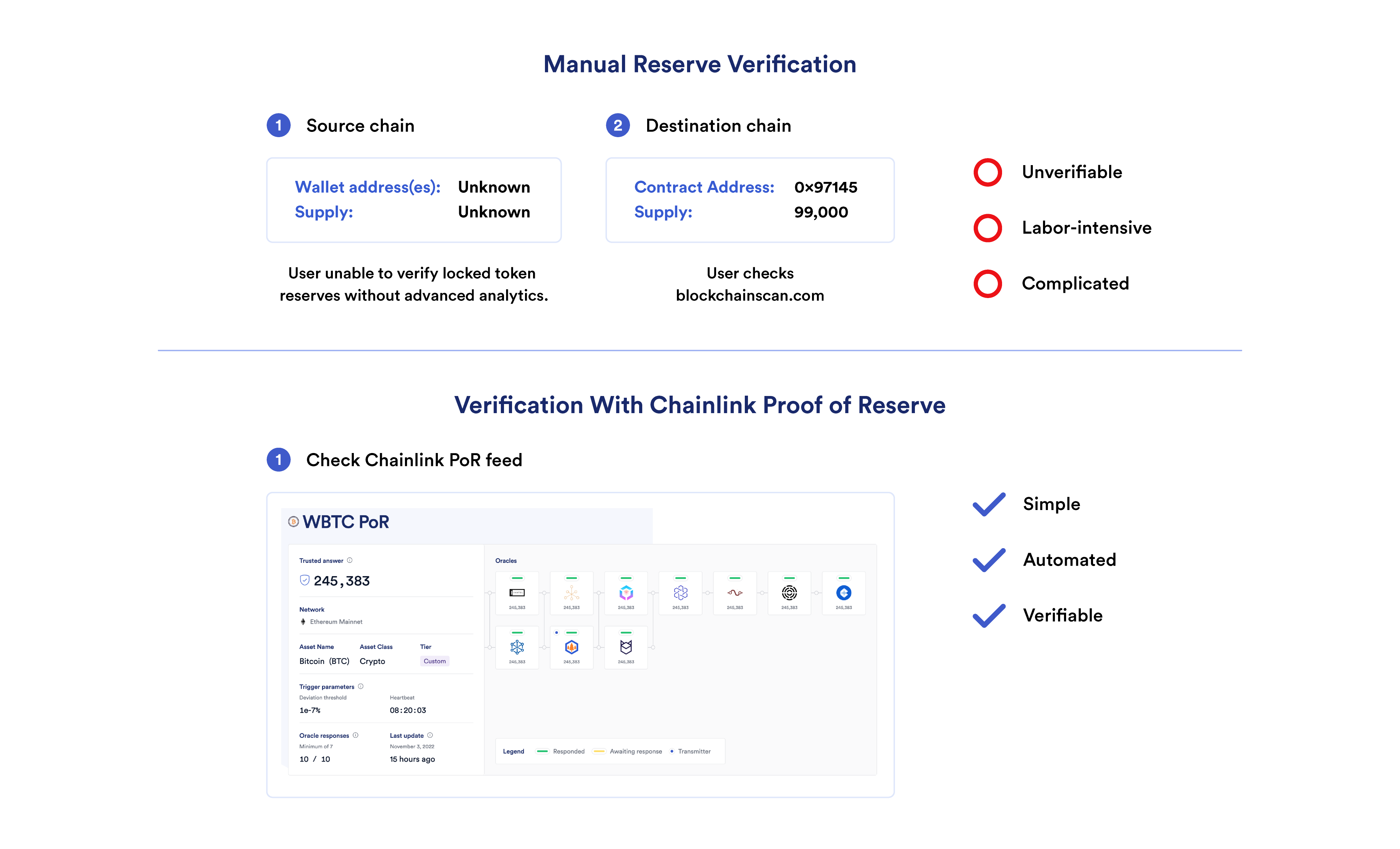
Chainlink Proof of Reserve (PoR) provides smart contracts with the information needed to calculate the true collateralization of any cross-chain reserves backing wrapped tokens. Operated by a decentralized network of oracles, Chainlink Proof of Reserve verifies cross-chain collateral—acting as a data layer for a wrapped token bridge.
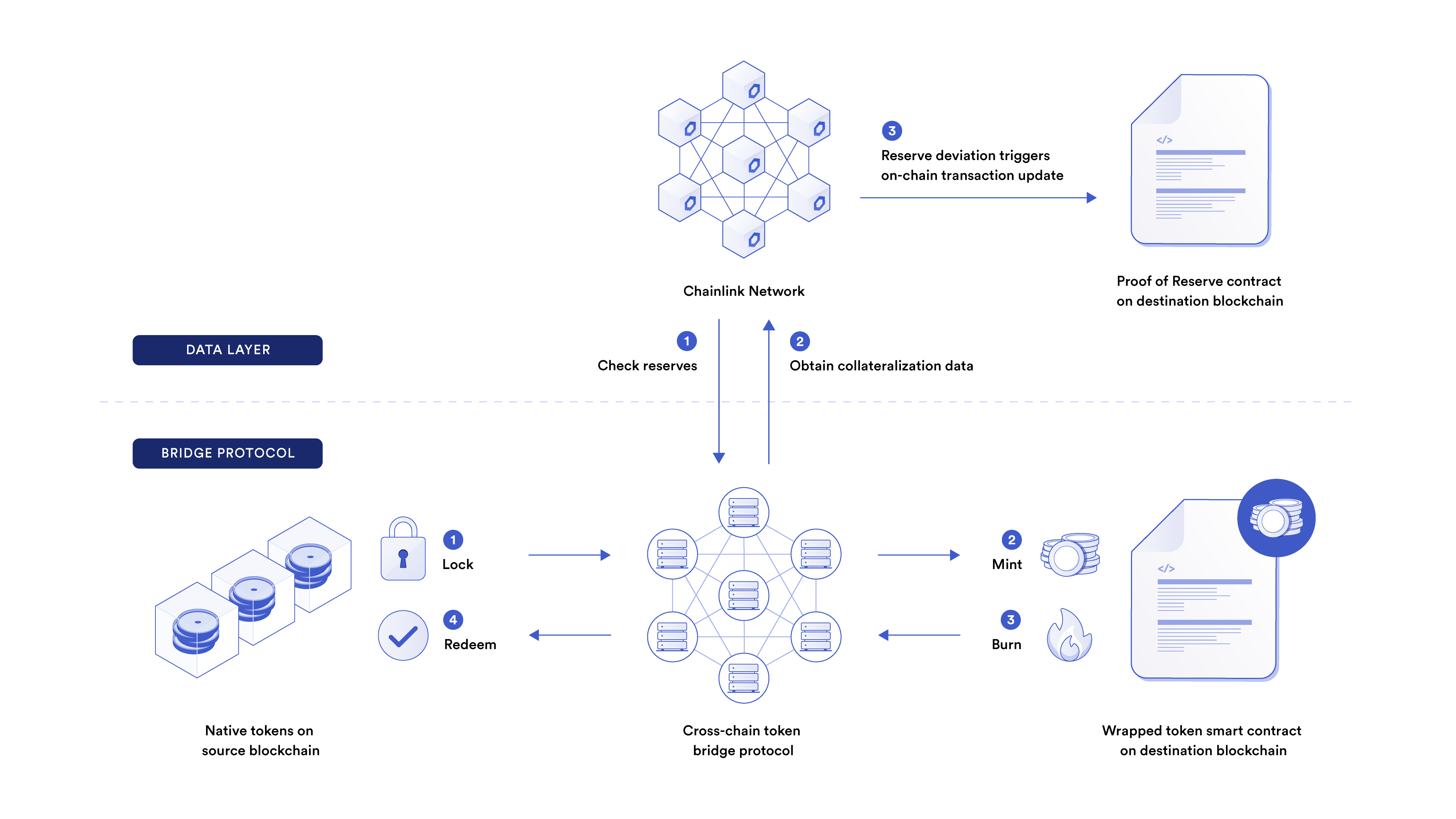
Note: Chainlink PoR increases transparency into the reserves backing wrapped tokens, and can be used for additional safeguard features, but doesn’t prevent a cross-chain bridge from being drained due to an exploit. Rather, PoR can be used by bridges and dApps to help mitigate the impact of such events.
There are 3 main benefits to using Chainlink Proof of Reserve for wrapped tokens.
1. Safeguard Smart Contract Functions
A robust and decentralized reserve data feed gives bridge developers the tools to build automatic fail-safe measures that can halt the minting, redeeming, and burning of a wrapped token. For example, one way to help protect against infinite mint attacks is to use Chainlink Proof of Reserve data feeds to check if there is an equal or greater amount of reserves than wrapped tokens. If there aren’t, the minting of additional wrapped tokens is reverted.
Because on-chain reserve data from Chainlink Proof of Reserve can help serve as a critical fail-safe in case of a bridge exploit or hack, it’s important that data feeds are secure, reliable, and accurate even in outlier circumstances.
By leveraging a decentralized, Sybil-resistant network of nodes run by proven node operators, Chainlink Proof of Reserve provides best-in-class cross-chain reserve verification services, with updates reliably posted on-chain regardless of market or network conditions.
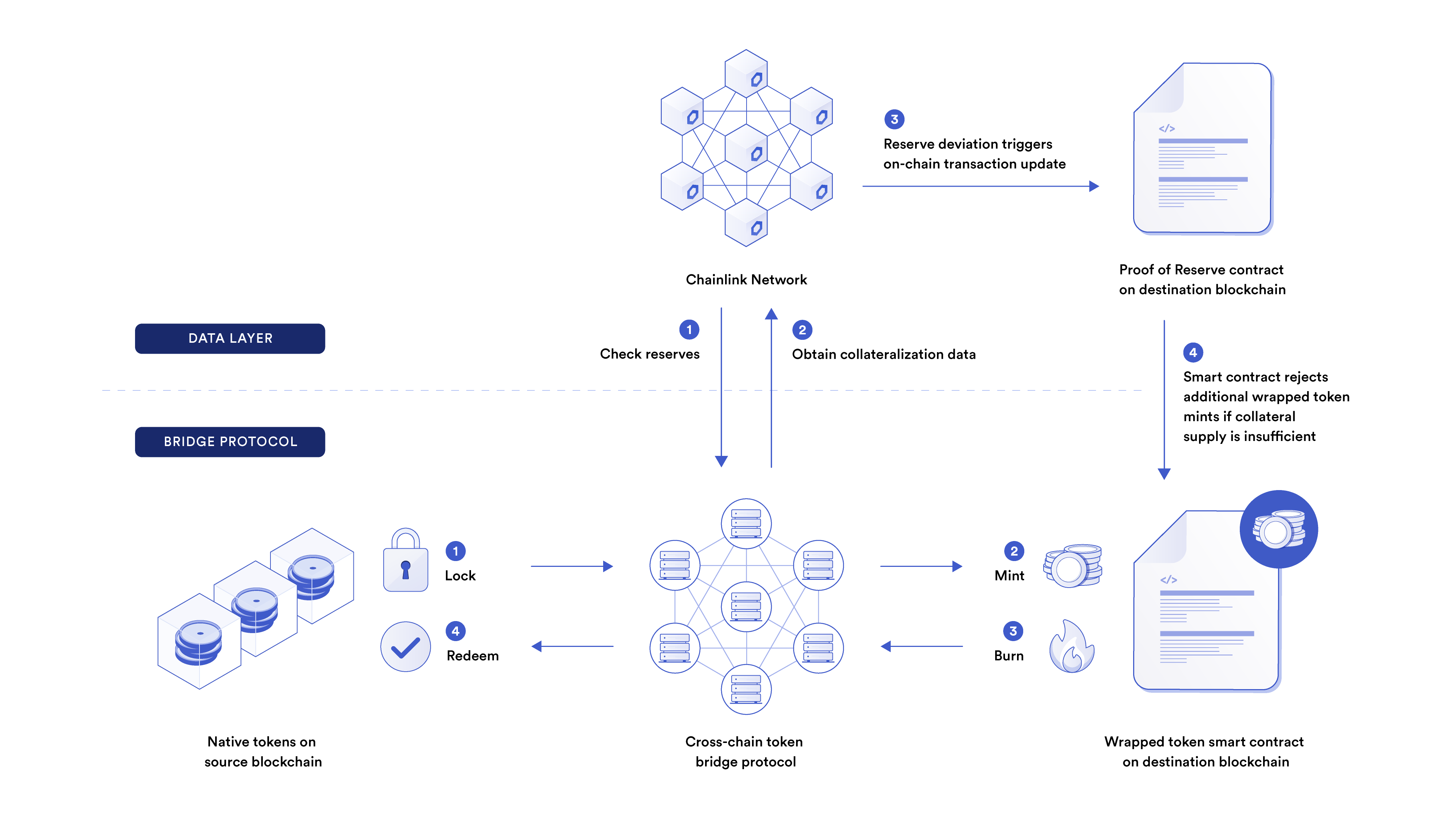
2. Enable Automatic DeFi Responses
Robust on-chain proof of reserves surrounding wrapped tokens through Chainlink PoR enables DeFi developers to build in protections against potential bridge hacks or exploits. This helps mitigate DeFi contagion risk, and as more DeFi protocols implement these failsafe measures, ecosystem resiliency and anti-reflexivity will grow.
For example, DeFi lending protocols could add circuit breakers that automatically pause lending pools using wrapped assets as collateral by reading data from Chainlink PoR data feeds. If there aren’t enough reserves locked on the source blockchain, the DeFi lending protocol can then automatically halt operations to reduce the severity of the event.
A good proof of reserves solution for wrapped token assets makes it easy for DeFi developers to leverage the data for this exact reason. To lower the bar for implementations, reserve data feeds should be simple to implement, use a standardized solution, and be posted natively on-chain.
As the industry-standard oracle solution for DeFi protocols, with over five billion data points delivered to blockchains, Chainlink Proof of Reserve enables DeFi developers to easily integrate reserve data into their dApp in just three steps.
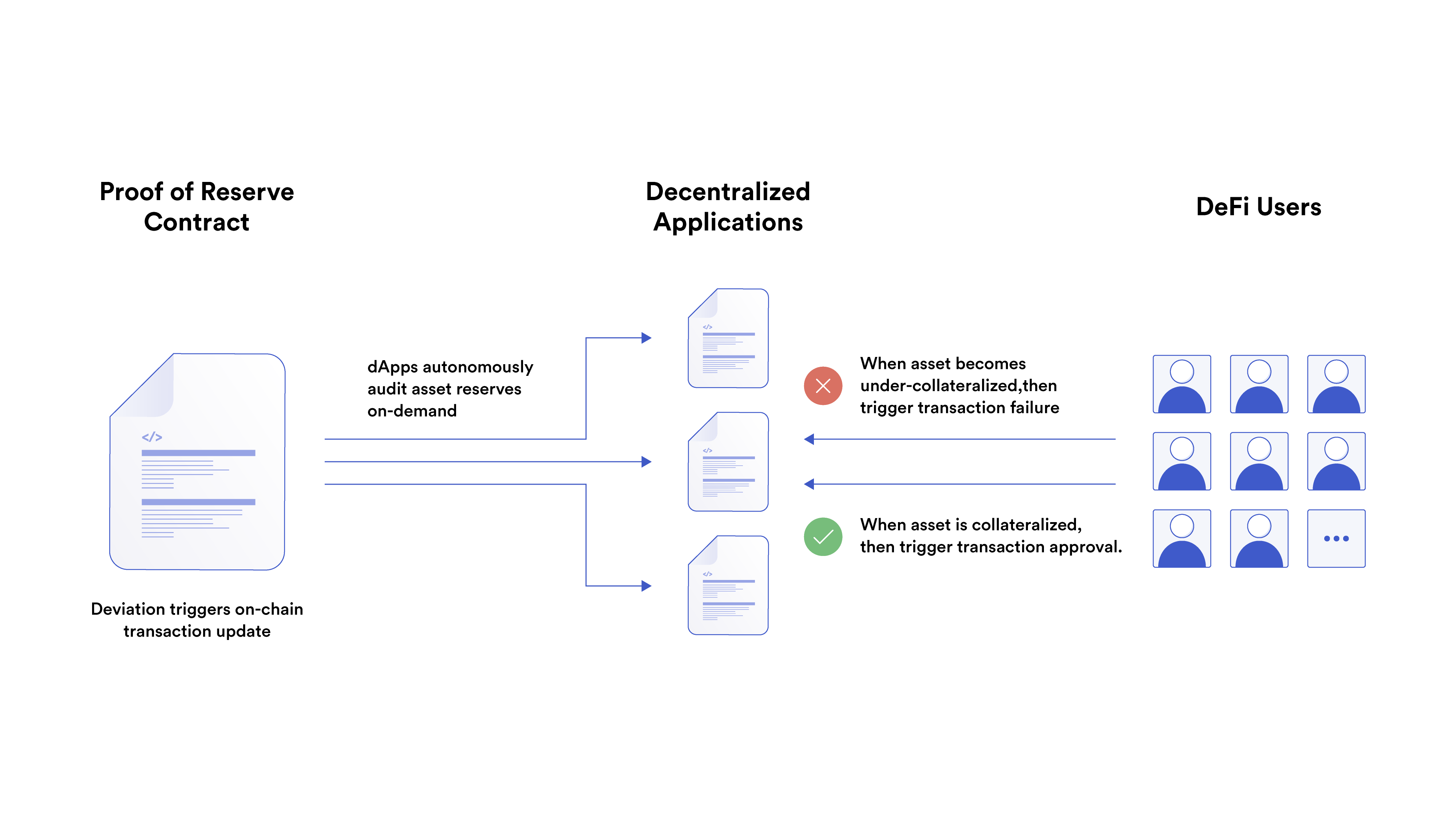
3. Provide Users With Transparency Around Cross-Chain Collateral
Automating data delivery on cross-chain reserves enables users to seamlessly verify the collateral backing of a wrapped token and quickly make informed decisions during outlier events—a key competitive edge for wrapped asset issuers looking to gain user adoption. Without proof of reserves, it can be difficult for users to verify on-chain that wrapped assets correspond on a one-to-one basis with assets on the source blockchain.
One key consideration is that exploits or hacks can happen quickly. Reserve data feeds should be designed to update on-chain in near real-time to give users maximum transparency into the state of the cross-chain bridge, particularly when it’s most needed.
That’s why Chainlink Proof of Reserve checks token reserves off-chain at regular intervals and updates the reserve data on-chain when it reaches a deviation threshold or heartbeat trigger, helping ensure real-time updates during unexpected events while saving on gas costs when reserves remain stable.
Conclusion
Bringing reserve data to blockchains provides crucial protection for cross-chain token bridges by enabling anyone to independently verify the collateral backing a wrapped token and projects to integrate automate failsafes in the event of a hack or exploit.
To find out more about how you can use Chainlink to help ensure the security of your wrapped token asset or DeFi protocol, reach out to our experts.
