Chainlink Confidential Compute: Unlocking Private Smart Contracts on Any Blockchain
Building on years of innovation and engineering, we’re announcing Chainlink Confidential Compute, a breakthrough service that unlocks private smart contracts on any blockchain.
Privacy shouldn’t be something we have to compromise on when making the next generation of smart contracts; we’re fixing that. We have also seen that a lack of privacy is the greatest barrier holding back large-scale institutional adoption of onchain finance.
Chainlink Confidential Compute unlocks a new class of private smart contracts that connect to real-world financial data and Web2 systems and interoperate across blockchains while keeping proprietary data, business logic, external connectivity, and computation fully confidential. This unlocks new, previously impossible onchain use cases for institutions, such as:
- Private Transactions: Enable onchain value exchange with confidentiality, concealing key transaction details so transactions and market positions remain confidential.
- Privacy-Preserving Tokenization (RWAs): Bring new types of institutional real-world assets (RWAs) onchain, such as tokenized bonds, private credit pools, and fund allocations, without exposing investor information, deal sizes, or pricing terms.
- Confidential Data Distribution: Monetize and securely distribute your proprietary data onchain, such as benchmark indices, reference rates, and valuations, to approved subscribers only in a privacy-preserving manner, while also giving smart contracts the capacity to perform operations without revealing underlying data.
- Privacy-Preserving Cross-Chain Interoperability: Execute transactions across public and private blockchains without revealing key transaction data to Chainlink node operators or other third parties, enabling use cases like Delivery vs. Payment (DvP) settlement where tokenized assets and stablecoins/CBDCs exist on different chains.
- Privacy-Preserving Identity and Compliance: Prove compliance and verify identities using existing identity providers and APIs without revealing underlying personal or institutional data onchain or to the nodes themselves.
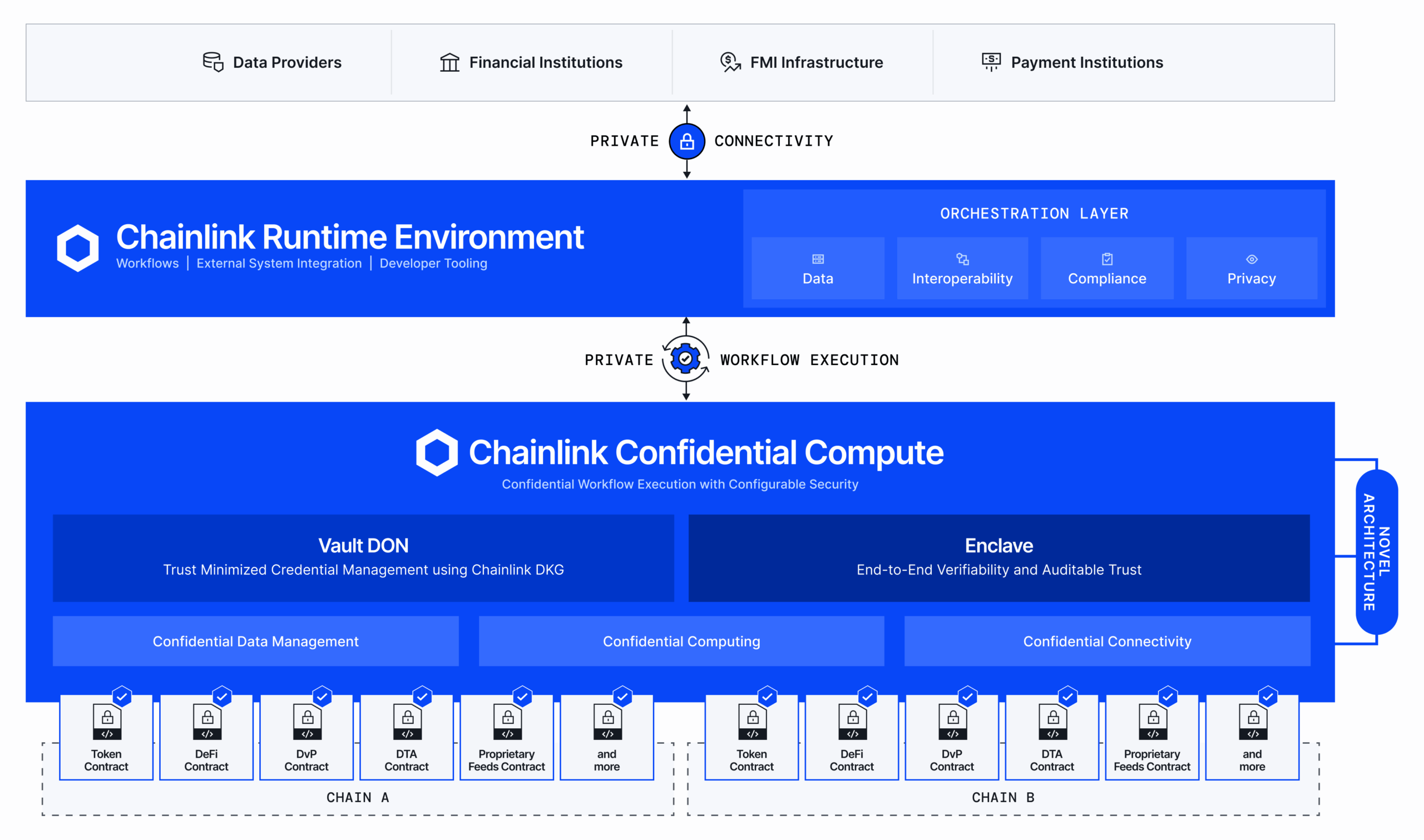
Chainlink Confidential Compute makes privacy-preserving use cases possible on any blockchain. It’s powered by the Chainlink Runtime Environment (CRE), which enables the creation of workflows that execute across blockchains and existing systems while connecting to key data, automating compliance policy enforcement, and leveraging private computation. By incorporating Confidential Compute into CRE, privacy can underpin every part of the transaction lifecycle, from data inputs, API requests, and identity verification to transaction processing, cross-chain transfers, and final settlement. CRE is your all-in-one orchestration layer for executing private smart contracts end-to-end.
The Early Access version of Chainlink Confidential Compute will be available through CRE in early 2026, with General Access launching later in 2026.
Read the whitepaper to learn more and contact an expert below.
The Privacy Opportunity
Every pillar of the global financial system, from capital markets and FX to money markets and derivatives, depends on privacy as a core principle. Without it, firms can’t protect client data, trading strategies, or business logic—the assets that underpin trust and competitiveness in modern finance. Institutional adoption of blockchain technology will only accelerate once tokenization frameworks ensure data confidentiality, transaction privacy on and across chains, and privacy-preserving regulatory compliance.
Privacy unlocks tokenization of not only visible assets like T-bills and real estate, but also complex institutional-grade instruments that may require confidentiality and more extensive compliance. However, until now, achieving privacy onchain meant building on isolated, privacy-focused blockchains or relying on specialized cryptographic methods, each with trade-offs in performance, interoperability, or trust assumptions. These limitations have prevented institutions from bringing proprietary data onchain, performing confidential transfers, and supporting fully regulated workflows.
Chainlink Confidential Compute changes that equation. Enabled by novel R&D from the world-class Chainlink Labs research team, Chainlink Confidential Compute combines the performance of trusted execution environments with advanced, trust-minimizing cryptographic techniques to deliver decentralized confidential computing to any blockchain. By merging privacy, connectivity, performance, and verifiable security together in a single architecture, Chainlink Confidential Compute provides the foundation for private smart contracts and scalable onchain markets built to institutional standards.
Chainlink Confidential Compute is based on technology from Town Crier, DECO, and many other leading privacy innovations created by the Chainlink Labs research team, and makes it easy for users to implement Mixicles, the Blockchain Privacy Manager, CCIP Private Transactions, and many other unique approaches to privacy, which will be available using CRE. These solutions have unlocked novel use cases, such as ANZ, ADDX, and Chainlink leveraging ADDX’s investment platform, ANZ’s Digital Asset Services, and CCIP Private Transactions to expand access to tokenized assets across borders while meeting user confidentiality requirements.
The Evolution of Onchain Privacy
Blockchains are fully transparent by design, with every transaction and contract visible to the public. While transparency enables verifiability, open participation, and trust without intermediaries, it also deters financial institutions from transacting onchain, since sensitive business logic, financial data, and client information could be exposed.
Over the past decade, multiple technologies have advanced onchain privacy, each contributing essential building blocks:
- Trusted execution environments (TEEs), also referred to as enclaves, deliver high performance, but require complementary safeguards to mitigate potential hardware vulnerabilities.
- Zero-knowledge proofs (ZKPs) are a foundational breakthrough for proving correctness without revealing underlying data, well-suited for use cases such as selective disclosure, identity attestations, and transaction confidentiality. Extending them to complex, multi-party, or continuously updating financial workflows remains an active area of research and engineering.
- Secure multiparty computation (MPC) and fully homomorphic encryption (FHE) offer powerful methods for collaborative private computation and encrypted data processing. These technologies are progressing rapidly, though broad, real-time, and developer-friendly deployment is still evolving.
- Private or permissioned blockchains provide data confidentiality, but can limit interoperability and composability with the broader onchain ecosystem.
Together, these approaches represent a growing toolkit for achieving privacy on public ledgers, but each of these individual solutions has their own distinct trade-offs.
Chainlink Confidential Compute’s Novel Architecture
Outlined below are the fundamental architectural innovations that differentiate Chainlink Confidential Compute from existing blockchain privacy solutions, including two new systems: Chainlink Distributed Key Generation (DKG) and the Vault Decentralized Oracle Network (DON).
1. Decentralized Secrets Management via Chainlink DKG and the Vault DON
Chainlink Confidential Compute features a decentralized, institutional-grade system for secrets management and long-term storage of confidential data.
- The Vault DON securely stores and manages secrets (e.g., API credentials, proprietary data, etc.) using threshold encryption and a trustless setup provided by Chainlink DKG. This creates a trust-minimized system that ensures no node operators or other entities can ever obtain access to your credentials.
- Chainlink DKG works by cryptographically dividing access to secrets amongst a quorum of independent node operators. When a secret is required to execute a confidential workflow, the nodes provide the enclave executing the confidential workflow with a set of decryption shares only after having performed all authorization checks and remote attestations. The enclave recombines the decryption shares received from the nodes into the secret, executes the confidential workflow, and finally discards the secret as soon as the execution is complete.
- This guarantees node operators and other entities cannot see, access, or act on secrets beyond what the user explicitly authorizes.
2. A Flexible Framework for Confidential Workflow Execution
By designing a decentralized architecture that enables users to select their underlying privacy-preserving technology, Chainlink Confidential Compute establishes the foundation for a new era of scalable, efficient, and verifiable privacy across decentralized systems.
- In the initial design, cloud-hosted TEEs process each workflow under a strict need-to-know model, only accessing the minimal information required to execute. Amongst other privacy technologies, TEEs offer vastly superior, more cost-effective performance, as they leverage hardware-level isolation to protect data during computation without the heavy computational costs associated with fully cryptographic approaches, such as MPC or FHE. This unlocks many practical, privacy-preserving use cases that were previously infeasible using purely cryptographic approaches.
- While also following the strict need-to-know model, future versions of Chainlink Confidential Compute will enable users to leverage different confidential computing technologies, which may include TEEs, ZKPs, MPC, or FHE as these technologies mature.
- With Chainlink Confidential Compute’s customizable framework available natively in CRE, users can write fully private workflows that securely connect any API with multiple blockchains and perform onchain and offchain actions, payments, data requests, and identity verification without ever revealing sensitive data or logic.
3. End-to-End Workflow Verifiability
Every confidential workflow executed in Chainlink Confidential Compute generates cryptographic attestations of the processed data and executed logic without revealing the data or logic itself.
- These cryptographic attestations can include additional workflow-specified data for enhanced auditability and verifiability.
- The additional workflow-specified data can be encrypted to designated parties, such as an auditor or regulator, ensuring strict need-to-know access.
- This creates blockchain-grade verifiability for private CRE workflows, enabling users to verify what was executed, when, and under what workflow, without revealing sensitive data or logic.
Read the Chainlink Confidential Compute whitepaper for a comprehensive view into the architecture and systems design.
Private Smart Contracts Powered by Chainlink Confidential Compute
Private smart contracts combine onchain verifiability with offchain scalability, confidentiality, and connectivity powered by CRE. They allow sensitive data and proprietary logic to be processed securely and efficiently while maintaining the transparency, integrity, and reliability guarantees that define blockchain systems.
CRE enables the creation of private smart contracts by bringing together:
- Onchain smart contracts across any blockchain: They enable private smart contracts to access onchain liquidity, permissionlessly integrate with the DeFi ecosystem in a fully composable manner, and accept arbitrary onchain requests.
- Chainlink Confidential Compute: This is the key technological innovation unlocking the creation of private smart contracts through decentralized secrets management, confidential and verifiable workflow execution, and confidential connectivity.
- Offchain data: Private smart contracts can securely connect to any offchain source of truth—including market data, reference rates, KYC/AML databases, internal enterprise systems, and authenticated APIs. Using Confidential Compute and the Vault DON, credentials and data access permissions remain private, ensuring that even sensitive or permissioned information can be used securely onchain. This enables use cases, such as triggering API-based payments, fetching proprietary benchmarks for tokenized assets, validating identities, or reconciling transactions, all without exposing data or credentials to any third party.
The Benefits of Chainlink Confidential Compute
- Privacy-preserving connectivity: Use your existing data and systems in a privacy-preserving manner to seamlessly transact across blockchains, enterprise networks, and the Chainlink platform.
- Compatible with public and private chains: Access confidential compute on any blockchain without migrating your contracts—build once, connect anywhere, no vendor lock-in.
- Decentralized secrets management: All secret data is threshold-encrypted and only the minimal data required for each computation is decrypted and processed, reducing exposure and protecting proprietary information.
- Verifiable and performant confidential computing: Leverage decentralized confidential compute, multi-cloud deployment, and advanced encryption and verifiability for institutional-grade security and scale.
- Cryptographically-attested workflow execution: Computations run in isolated TEEs and are independently verified by a decentralized oracle network, providing proof that every operation was executed as intended.
New Use Cases Unlocked With Chainlink Confidential Compute
Proprietary Data Feeds
Many financial smart contracts need access to proprietary data in order to service tokenized assets and facilitate settlement. However, data providers don’t often want to make their proprietary data available on public blockchains where it can be copied and redistributed.
Chainlink Confidential Compute enables data providers to securely distribute their data to approved subscribers only in a privacy-preserving manner. This allows data providers to monetize confidential information safely while giving smart contracts verifiable access to trusted offchain data streams, such as benchmark indices, market pricing, and corporate action data used to value and settle institutional RWAs. This data can be used to trigger automated onchain actions, such as executing token trades.
Private Tokens (RWAs)
Many financial institutions require privacy over specific aspects of their onchain transactions, such as token balances, transaction amounts, and counterparties involved. This is especially critical for institutional RWAs—such as private credit, structured debt, and fund shares—where transaction confidentiality and portfolio privacy are mandatory.
Chainlink Confidential Compute enables private tokens—onchain assets where sensitive transaction information remains private while still maintaining full auditability and regulatory controls. This makes it possible for institutions to tokenize and settle a broader range of financial instruments securely onchain. Chainlink Confidential Compute simplifies the design of private tokens, supporting confidentiality of onchain balances and transaction amounts as well as privacy of sender and receiver addresses.
Identity and Compliance
In financial markets, regulatory compliance depends on identity verification, such as for KYC (Know Your Customer), AML (Anti-Money Laundering), or investor eligibility. However, many digital asset systems expose more data than necessary, creating risks around privacy, data leakage, and regulatory uncertainty.
Chainlink Confidential Compute enables institutions to prove compliance without revealing underlying personal or institutional data. At its simplest, Chainlink Confidential Compute can verify digital credentials inside a confidential computation, releasing only a specific attribute onchain (e.g., Y/N, user > 21 years old). Chainlink Confidential Computation can also support a more advanced identity system by serving as a “credential re-certifier.” The re-certified credentials can be efficiently used and verified onchain without requiring another invocation of Chainlink Confidential Compute. This approach enables synchronous onchain verification while maintaining user privacy and unlinkability.
Confidential API Access
Access to API data and services—from market feeds and payment gateways to compliance databases—is essential in modern financial systems. When connecting these APIs over HTTPS to blockchain-based systems, developers face a critical challenge: how to authenticate securely without exposing sensitive credentials like API keys or client certificates.
Chainlink Confidential Compute elegantly solves this problem based on the Town Crier approach for secure and verifiable HTTPS queries. API credentials are encrypted and forwarded to the TEE, where they are decrypted, used to authenticate to the external API, and immediately discarded. This mechanism also generalizes to more complex interactions, where additional encrypted secrets can be provided as private inputs or where only selected parts of the API response are revealed in the output. For example, a user could supply an encrypted credit card number to enable a payment provider to process transactions securely without exposing the card details to the blockchain, developer, or any node outside the TEE.
Interested in Chainlink Confidential Compute?
Chainlink Confidential Compute’s architecture is intentionally built to be flexible and future-proof, so it can support innovative technologies like FHE as research around privacy-enhancing technologies develops and new solutions become more viable. This ensures the system remains future-proof and gives users choice over the privacy-preserving technologies they use based on their unique needs.
If you’re an institution or Web3 protocol looking to build private smart contracts using Chainlink Confidential Compute, reach out to us. You can learn more by reading the Chainlink Confidential Compute whitepaper.
—
Disclaimer: This post is for informational purposes only and contains statements about the future, including anticipated product features, development, and timelines for the rollout of these features. These statements are only predictions and reflect current beliefs and expectations with respect to future events; they are based on assumptions and are subject to risk, uncertainties, and changes at any time. There can be no assurance that actual results will not differ materially from those expressed in these statements, although we believe them to be based on reasonable assumptions. All statements are valid only as of the date first posted. These statements may not reflect future developments due to user feedback or later events, and we may not update this post in response. Please review the Chainlink Terms of Service, which provides important information and disclosures.
