What Is Zero-Knowledge Encryption?
Zero-knowledge encryption ensures end-to-end data security and privacy within services like cloud storage and password management.
Zero-knowledge encryption ensures end-to-end data security and privacy within services like cloud storage and password management.
<div class="educational-divider sections-divider"></div>
The Basics of Encryption
While today’s encryption technology relies on complex mathematical formulas and equations that the average layperson may not understand, the underlying concept behind encryption is quite simple.
Encryption is the process of converting information (data) into a special code to prevent unauthorized access to that information. Unencrypted messages are referred to as plaintext. Once encrypted, they become ciphertext. An easily understandable example is the Caesar cipher—also known as a “shift cipher”—which is explained below.
Consider the following plaintext message: “THIS IS A BLOG”
We’re going to encrypt this message using a right shift of two. All this means is that “A” becomes “C,” “B” becomes “D,” and if we go toward the end of the alphabet, it wraps around so that “Z” becomes “B.”
Thus, the encrypted ciphertext message is: “VJKU KU C DNQI”
Encryption Keys
Encryption keys are used to encrypt or decrypt a message.
In the Caesar cipher example above, the sender and receiver must create the encryption key beforehand. An example could be starting each message with a single letter that identifies the shift. A = right shift of one, B = right shift of two, and so on. These function as encryption keys.
The key question to ask regarding whether a service offers zero-knowledge encryption is: Who has knowledge of the encryption key? It should only be the user.
Symmetric Encryption
The Caesar cipher is an example of symmetric encryption, which simply means that the sender and receiver use the same key to encrypt and decrypt the message. For this type of encryption to be effective, both parties must know what the key (right shift of 2) is, and the key should be difficult to guess or steal.

Asymmetric Encryption
Most of the Internet today is underpinned by asymmetric encryption, also known as public-key cryptography. Encryption keys are generated in mathematically-related pairs—public and private keys. The key benefit of using asymmetric encryption is that anybody can use a public key to encrypt a message, but only the entity with the private key can decrypt the message.
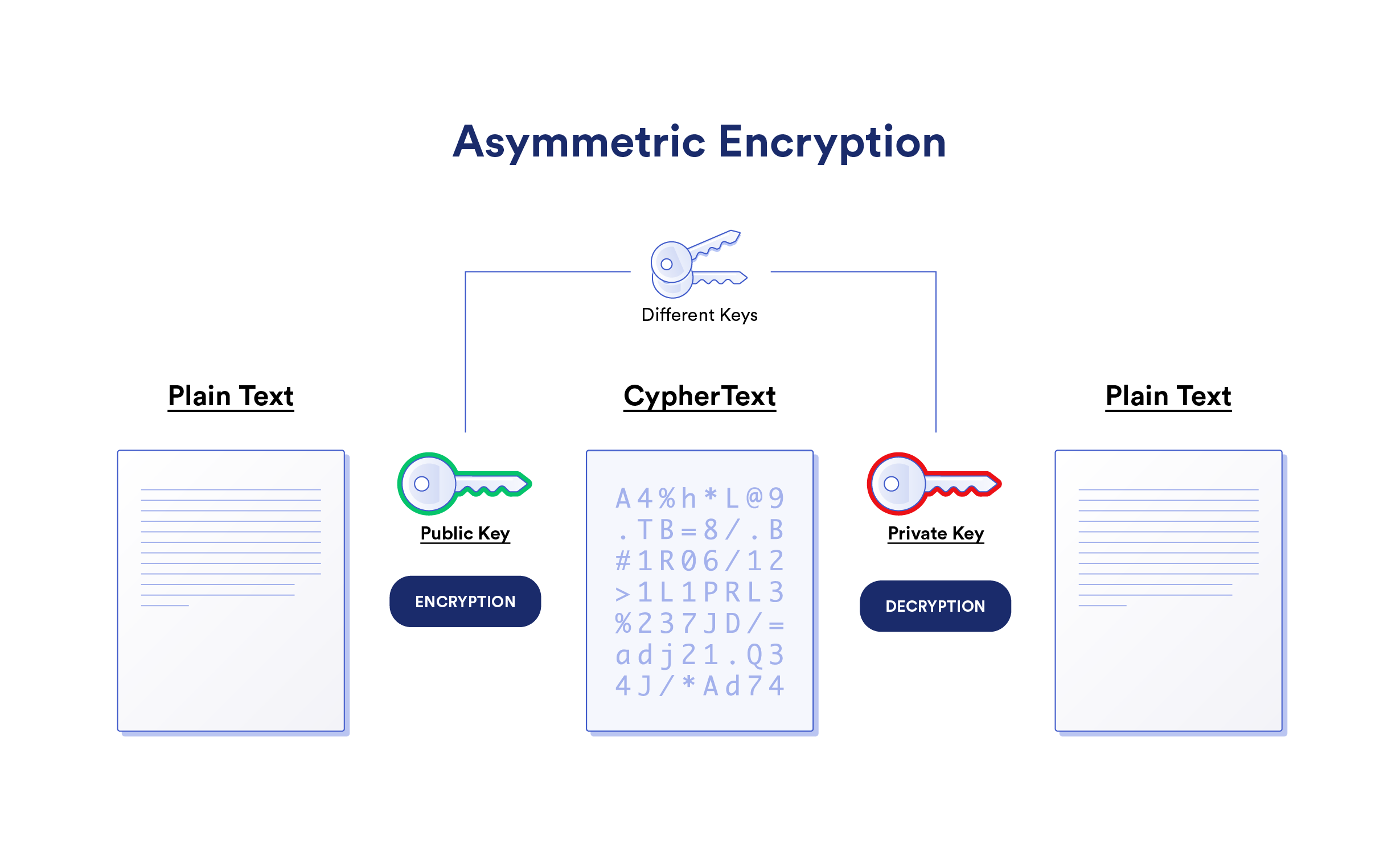
This handy feature is widely used alongside symmetric counterparts to underpin Internet security, and it’s currently used within protocols like HTTPS as well as a wide range of email services, blockchains, messaging applications, and more.
<div class="educational-divider sections-divider"></div>
How Does Zero-Knowledge Encryption Work?
Encryption is adopted by all major applications, websites, and services on the Internet to varying degrees. Existing encryption protocols such as Advanced Encryption Standards (AES) and Transport Layer Security (TLS) are widely used and have become standards for Internet applications and services.
Zero-knowledge encryption is not a specific encryption protocol, but a process that focuses on preserving a user’s data privacy and security to the maximum extent. In order for a service to be truly zero-knowledge, a user’s data must be encrypted before it leaves the device, while it’s being transferred, and when it is stored on an external server.
This is because modern encryption in general is incredibly effective at barring unauthorized participants from decoding encrypted data. It’s functionally impossible to crack modern-day encryption using brute-force approaches. However, for ease of use and UX benefits, many service providers also hold a user’s encryption key—introducing an additional point of failure that’s attractive for malicious actors because service providers often hold many user keys. There are a variety of benefits (and also detriments) when service providers share knowledge of an encryption key, but it also means that someone other than the user can decrypt the data—which makes it not zero-knowledge.
The key question to ask regarding whether a service offers zero-knowledge encryption is: Who has knowledge of the encryption key? It should only be the user.
Authentication With Zero-Knowledge Proofs
Most zero-knowledge cloud storage providers have a simple UX that’s familiar to users—type in the password to access the account. But a service provider doesn’t know or store your password, so how do they verify it’s correct?
The answer is zero-knowledge proofs, which enable service providers to verify a user knows the encryption key/password without requiring the user to reveal the key itself. This solves the authentication issue, but there are still a variety of encryption protocols needed to secure the data as it’s moved, uploaded, downloaded, and stored.
Client-Side Encryption
Client-side encryption means that data is encrypted on the side of the sender before it is transferred to an external server. In the context of zero-knowledge encryption, this means that the data is encrypted before a user ever communicates with the service provider—making it effectively impossible for the service provider to decrypt the data without knowledge of the encryption key even if they’re hosting it.
Encryption-in-Transit
Encryption-in-transit protects your data when it is in transit. In simple terms, when some information—whether a message, a file, or other types of data—is being uploaded or downloaded, encryption-in-transit ensures nobody can break in and see the message while it’s being transferred.
The industry standard for encryption-in-transit protocols is TLS.
Encryption-at-Rest
Whether the data is being stored on a personal computer or on a cloud server, encryption-at-rest refers to the encryption of data wherever it is being stored.
The industry standard for encryption-at-rest protocols is AES, specifically AES-256.
<div class="educational-divider sections-divider"></div>
Pros and Cons of Zero-Knowledge Encryption
Using a service with zero-knowledge encryption comes with a variety of benefits and detriments.
The Pros of Zero-Knowledge Encryption
When it comes to data privacy and security, zero-knowledge encryption is unmatched. Because only the user has access to the encryption key, nobody else can decrypt and see their data.
This is most useful in cloud storage and password management services, where a hack or exploit on the server side (i.e on an external server) can result in significant privacy breaches for users. By implementing a zero-knowledge encryption design, service providers have less liability because any external attack still won’t reveal user data, while users have additional peace of mind that their data is protected even in the case of server attacks.
The bottom line: if a user wants to preserve their data’s privacy and security while still hosting it on an external server for easy data management, there’s no better option than zero-knowledge encryption.
The Cons of Zero-Knowledge Encryption
The main benefit of zero-knowledge encryption also necessitates some tradeoffs.
No Recovery of Encryption Key
One limitation of zero-knowledge encryption design is that if a user ever loses access to their encryption key or forgets their password, there is often no way to access their data from that point on. Service providers can’t offer recovery as they don’t know the encryption keys.
One method of counteracting this limitation is to give users the ability to create a recovery key beforehand, but this is often implemented as a one-time use—making recovery a problem again after the first time a user leverages this option.
Slow Speeds
Zero-knowledge encryption designs guarantee security and privacy at every step of the way. Service providers that offer the full zero-knowledge encryption guarantee are typically slower than less secure counterparts simply because it takes more work to securely transfer and store user data.
Diminished Application Feature Set
Service providers often use user data to create tailored experiences. For example, Apple’s photo application will automatically look through a user’s photos to create curated experiences and lookbacks.
Because service providers that offer zero-knowledge encryption designs don’t have access to any of a user’s data, they’re unable to build out features that require a user’s data to create a better and more convenient user experience. This is true even for simple functionality, such as the ability to preview images, files, and folders before fully opening them.
<div class="educational-divider sections-divider"></div>
Conclusion
With the correct design, service providers offering zero-knowledge encryption solutions are inherently replacing brand-based promises with mathematical guarantees. Users don’t have to trust zero-knowledge cloud storage providers or password managers to keep their data safe—their data is safe by virtue of the implementation.
This form of cryptographic guarantee is what Web3 is really about, and zero-knowledge encryption designs within cloud storage and password management providers are just the start. Blockchains and expanded zero-knowledge proof designs go past the limited nature of zero-knowledge encryption design to preserve a user’s data privacy, sovereignty, and security while still enabling the wealth of innovation society has seen from the open flow of data.














