Homomorphic Encryption
Homomorphic encryption is a cryptographic technique that allows computations to be performed on encrypted data without requiring decryption.
Current encryption technology is incredibly valuable. It underpins the Internet, lies at the heart of Web3, and empowers individuals to protect their personal information. However, traditional encryption schemes have a major limitation—data has to be decrypted before it can be analyzed and computed. Naturally, decrypting private data and exposing it to third parties undermines the reasons to encrypt data in the first place.
Homomorphic encryption overcomes this limitation by enabling encrypted data to be computed, meaning you can get cloud providers or web-based services to compute your data without ever having to expose your raw data to them. For organizations and individuals who value data privacy, homomorphic encryption is set to enable vastly higher levels of functionality—without compromising security.
<div class="educational-divider sections-divider"></div>
What Is Homomorphic Encryption?

Homomorphic encryption is a cryptographic technique that allows computations to be performed on encrypted data—without requiring decryption. That means raw data can remain fully encrypted while it’s being processed, manipulated, and run through various algorithms and analyses. This enables you to keep data private while sharing it with third parties for computation. Given that current encryption methods cannot run computations on encrypted data, homomorphic encryption is set to unlock many exciting use cases.
Why is homomorphic encryption so transformative? Imagine you want to use a service that tests your genome to identify risk factors for genetic diseases. With most of today’s platforms, you’d be giving a third party complete access to your DNA, along with the medical conditions you may currently have or be at high risk for. Homomorphic encryption could enable you to access all the benefits of this service without having to expose a single sequence of your personal genome data.
Although homomorphic encryption was envisioned in 1978 by Rivest, Adleman, and Dertouzos, it wasn’t until 2009 that it was first fully constructed—a feat achieved by a brilliant MacArthur Fellowship recipient and computer scientist named Craig Gentry. Here’s how Gentry described homomorphic encryption, analogizing it to wearing special gloves that enable you to manipulate objects locked inside of a black box:
“Anybody can come and they can stick their hands inside the gloves and manipulate what’s inside the locked box. They can’t pull it out, but they can manipulate it; they can process it… Then they finish and the person with the secret key has to come and open it up—and only they can extract the finished product out of there.”
<div class="educational-divider sections-divider"></div>
Homomorphic Encryption Use Cases
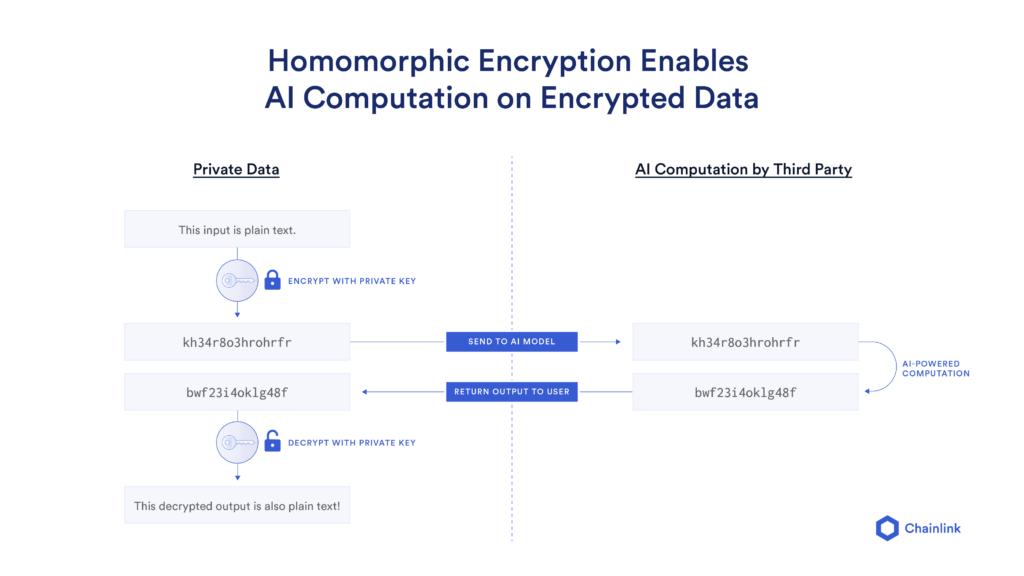
Secure Artificial Intelligence/Machine Learning
AI/ML algorithms can be trained on sensitive data without the raw data ever being exposed. This guaranteed data privacy can give large populations of individuals the confidence and security needed to share their data with AI projects, providing them with the huge volumes of raw data necessary to run AI algorithms that make a real-world impact.
Imagine a medical researcher who wants access to a hospital’s patient data so she can run an AI algorithm that identifies the optimal treatment for a rare form of cancer. Unfortunately, the hospital can’t share that data because it would breach their privacy standards. However, they could send their encrypted data to the researcher—enabling her to identify the optimal cancer treatment while keeping individual patient data completely private.
Secure Cloud Computation
Traditional cloud-based computation methods require access to unencrypted data to perform computations, which exposes sensitive data to cloud operators and any malicious actors that breach the network. With homomorphic encryption, cloud servers can compute directly on encrypted data and return encrypted results to the owner of the data, who can then decrypt them locally.
Regulatory Compliance
Data privacy regulations such as GDPR have created privacy challenges for businesses across the globe. Homomorphic encryption can expand a company’s ability to provide online services to citizens, whilst still meeting regulatory requirements and protecting user data.
Secure Voting
Voters can securely cast their votes without ever having to reveal who they voted for. This could make elections fairer and more transparent, and the enhanced privacy could encourage voter participation. A simple Paillier encryption scheme—a partially homomorphic encryption type—could be used to add up votes in a way that keeps them secret and allows third parties to verify the accuracy of the vote count.
Supply Chain Security
Many companies must share sensitive data with their contractors, vendors, and other third parties so they can coordinate their supply chains and operations. Even if these third parties never act maliciously, exposing raw data to a supply chain software system creates an attack vector. Homomorphic encryption can help companies mitigate these risks by using encrypted data within their backend systems, which can compute the necessary actions required for third parties without ever exposing any sensitive data.
<div class="educational-divider sections-divider"></div>
Types of Homomorphic Encryption Schemes
Homomorphic Encryption TypesPartiallySomewhatLeveled FullyFullyRatingSimpleIntermediateAdvancedMost advancedComputationsAddition or multiplicationAddition and multiplicationComplex but limitedComplex and unlimitedUse casesSum or productBasic statistical analysisAI/ML, MPCAI/ML, MPC
Partially Homomorphic Encryption
The simplest type, partially homomorphic encryption, enables either additions or multiplications to be performed on the encrypted data, but not both. It can compute the product or sum of a dataset.
Somewhat Homomorphic Encryption
Somewhat homomorphic encryption allows for both addition and multiplication operations to be performed on the encrypted data, although it has some limitations. Specifically, the number of operations that can be performed is bounded and the accuracy of the computation may degrade as more operations are performed. This scheme can be useful for evaluating simple functions or performing basic statistical analyses.
Leveled Fully Homomorphic Encryption
A more advanced scheme, leveled fully homomorphic encryption can perform an arbitrary number of computations on encrypted data, as long as it has a pre-defined sequence of computations to be specified ahead of time. It can be used for complex computations such as machine learning (ML) algorithms and secure multi-party computation (MPC).
Fully Homomorphic Encryption (FHE)
The most advanced type, FHE allows any number of computations to be performed on encrypted data without a predefined sequence or limit. Any computation on plaintext data, including ML and MPC, can be evaluated. However, FHE schemes are currently computationally expensive, making them impractical for many use cases.
<div class="educational-divider sections-divider"></div>
Conclusion
The impact of a new technology rises exponentially when combined with similarly transformative innovations. For example, blockchains gained much more functionality with the introduction of smart contracts, then oracle networks unlocked entire new design spaces across DeFi, NFTs, and insurance, and now zero-knowledge proofs are helping the Web3 ecosystem scale to support hundreds of millions of users.
Not only does homomorphic encryption unlock many exciting use cases on its own, it can also bring together two of the most transformative technologies in the world today—Web3 and AI. Oracle networks could play a key role in enabling AI algorithms to compute encrypted data stored on blockchains in a secure, reliable, and decentralized manner. While further research into homomorphic encryption is needed to make fully homomorphic encryption more cost-effective and scalable, homomorphic encryption is already enhancing data privacy and security, and this trend is set to continue.














